ShinyHunters – From the notorious international hacker group to the attack on the National Credit Information Center (CIC)
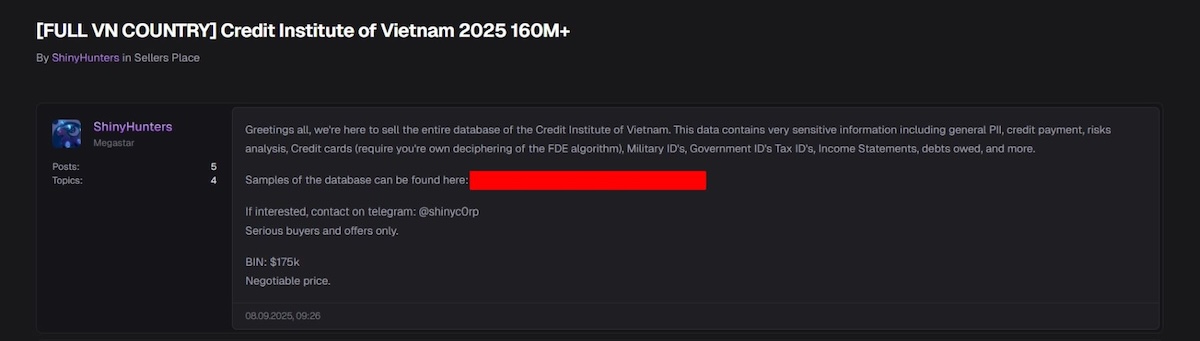
September 10, 2025, a large-scale attack targeted the National Credit Information Center (CIC) and was recorded by the Vietnam Cyber Emergency Response Center (VNCERT). According to reports, this campaign is linked to ShinyHunters – an international hacker group known for numerous major data breaches worldwide.
The hacker group ShinyHunters claimed to have successfully attacked and seized over 160 million data records from the National Credit Information Center of Vietnam (CIC – Credit Institute of Vietnam).
About ShinyHunters
ShinyHunters is known as a cybercriminal group (“black-hat hacker/extortion group”) famous for stealing and selling data. They emerged in the early 2020s with a series of well-known data theft campaigns. For those who don’t know, the name “ShinyHunters” is inspired by the Pokémon game—”shiny” in Pokémon refers to a rare version. Similarly, the hacker group views sensitive, valuable data as “rare and worth hunting.”
The main motivation of hacker groups is financial gain, for example, stealing data to sell on the black market or extorting victims by threatening to disclose their information unless they pay. In addition, generating publicity is also part of their strategy, as major data leaks help these groups gain notoriety in the cybercrime world.
Notable Campaign
In addition to the data attack at CIC in Vietnam, ShinyHunters has carried out many large-scale data campaigns worldwide, demonstrating the scope and sophistication of their operations.
They first emerged in 2020 with an attack on Tokopedia, a major e-commerce platform in Indonesia, marking their initial steps in the cybercrime world. The initial damage recorded included over 91 million user records stolen, such as emails, hashed passwords, and personal financial data.
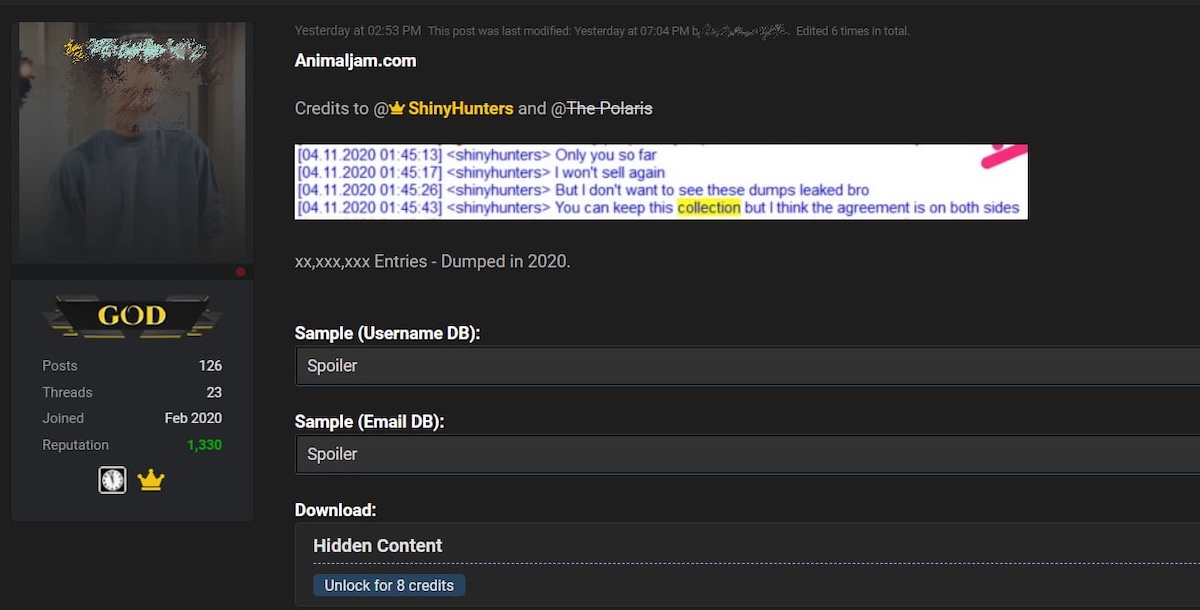
Later that same year, the hacker group’s victim was India’s Unacademy system, affecting tens of millions of accounts that had their information stolen. This incident led to the information of over 20 million customers being sold on the Dark Web for $40,000. In November, ShinyHunters was also responsible for leaking 46 million user records from the popular children’s game AnimalJam, and 3.2 million user records from the US Internet TV service Pluto TV.
Since the beginning of 2021, ShinyHunters has continued to be involved in major personal data breaches. Among the affected services is the online photo editing app PIXLR (with over 19 million users having their information stolen). Additionally, software for digital documents – Nitropdf was also targeted, with 77 million records sold on the Dark Web. Notably, the dating platform MeetMindful had 2.28 million personal records and sensitive information stolen for extortion. All three data systems were widely advertised on forums and easily available for purchase.
Continuing into 2022, they did not stop but expanded their campaigns with the Bonobos event, a well-known fashion retail chain, leading to the leak of approximately 70GB of sensitive customer data. Moving into 2023, ShinyHunters gained significant attention by taking over BreachForums, a forum dedicated to sharing leaked data, showing that their goal is not just to steal information but also to make a name for themselves in the cybercrime world.
Since 2024, this hacker group has become even more daring, targeting numerous large companies and corporations worldwide. Some of their victims, such as Adidas, LVMH, Qantas, and Allianz Life, have all been affected by attacks on environments using Salesforce and Snowflake, causing significant damage.
Methods and Techniques
ShinyHunters use a variety of methods to attack targets, including:
- Phishing or Vishing (fake phone calls, fake emails) to obtain login information and access systems.
- Exploiting software vulnerabilities, exploit kits, or systems that are unmaintained or unsupported.
- Attacking cloud storage/buckets like AWS/GitHub/etc — where source code, credentials, configurations, and APIs are stored.
- Organized attacks on major SaaS platforms like Salesforce, by impersonating connected apps or third-party tools (e.g., Data Loader), tricking employees into granting access.
ShinyHunters attack CIC
ShinyHunters claimed they attacked CIC through an “n-day” vulnerability in end-of-life software. “N-day” vulnerabilities are publicly known security flaws that already have exploit code.
Unlike “Zero-day” vulnerabilities, “n-day” vulnerabilities can be easily exploited if the target system hasn’t been patched. In this campaign, the ShinyHunters group initially scanned CIC’s systems to find outdated software (EOL).
They also often use SQL Injection, exploiting vulnerabilities in web databases to directly query sensitive data. They then exploited the discovered vulnerabilities to infiltrate CIC’s internal systems. And of course, after gaining access, ShinyHunters extracted, copied, and downloaded data (about 160 million records).
Impact on Users
- About 160 million personal information records of citizens were stolen
- Full name, date of birth, address
- ID card number, tax code
- Financial information, credit history, loan limits
- Although transactions will not be affected, cybercriminals may exploit this incident for fraud. Therefore, users need to be extremely cautious with calls, messages, or emails impersonating banks, CIC, or the police.
Conclusion
The attack campaign on CIC by the ShinyHunters group is not just a simple data leak but a serious wake-up call for national cybersecurity, highlighting the weaknesses in technical infrastructure and the awareness of regularly scanning for system vulnerabilities.
Recommendations
Từ các vụ tấn công của ShinyHunters qua từng năm, có thể rút ra nhiều bài học quan trọng cho các tổ chức và cá nhân trong việc bảo vệ dữ liệu. Trước hết, việc quản lý và giám sát dữ liệu phải được thực hiện nghiêm ngặt. Bên cạnh đó thì yếu tố con người vẫn là mắt xích quan trọng nhất.
-
Recommendations for Users:
- Check and protect personal information
- Proactively check if your personal information (ID card, phone number, email, bank account) has been leaked.
- If you suspect a leak, change your password/PIN and temporarily lock your account if necessary.
- Use strong passwords and multi-factor authentication (MFA)
- Avoid reusing passwords across multiple services.
- Passwords should be at least 12 characters long, including uppercase, lowercase, numbers, and special characters.
- Enable two-factor authentication (MFA) for bank accounts, email, and social media.
- Be cautious of phishing (impersonating CIC)
- Never click on suspicious links in SMS/emails claiming to be from CIC, banks, or the Ministry of Public Security.
- CIC will never call to request OTP verification or ask for account numbers.
- If you receive unusual information, contact the official hotline of CIC or your bank directly.
- Monitor credit reports and unusual financial activities
- Regularly check your personal credit report (via the CIC app or your bank).
- If you find unfamiliar loans or credit registrations not made by you → file a complaint immediately.
- Consider subscribing to credit change alert services (if provided by your bank).
- Check and protect personal information
-
Recommendations for Organizations:
- Review and remove outdated software (EOL)
- Immediately stop using software and operating systems that are no longer supported (end-of-life).
- Establish a process for regularly checking the IT asset list and updating software to officially supported versions.
- Establish a Vulnerability Management process
- Implement a comprehensive system for monitoring, scanning, and assessing vulnerabilities.
- Regularly scan internal and external systems to quickly detect n-day and zero-day vulnerabilities.
- Classify severity levels (CVE score) and plan patches based on priority.
- Review and remove outdated software (EOL)
References
Vietnam’s national credit registration and reporting agency hacked; most of the population affected – DataBreaches.Net
ShinyHunters, one of the most recognised threat actors among the hacking community
Cyber Extortion Group “Shiny Hunters” Targets Salesforce Customers
| Exclusive article by FPT IS Technology Experts
Luu Tuan Anh – FPT IS Cyber Security Center |