Chrome Users Beware: Cookie-Bite Technique Targets Your Session Cookies
In the context of increasingly sophisticated cybersecurity threats, a new attack technique called Cookie-Bite was discovered by security researchers and announced on April 2025. This technique exploits a Chrome browser extension to steal session cookies from Azure Entra ID, thereby bypassing multi-factor authentication (MFA) and maintaining access to cloud services like Microsoft 365, Outlook, and Teams.
Details
MFA is designed to prevent unauthorized access, but attackers continuously develop techniques to bypass this security barrier. Cookie-Bite is a prime example, allowing attackers to steal user identities by hijacking session cookies, thus accessing cloud services without needing passwords or MFA.
By using malicious browser extensions and automation scripts, attackers can extract and reuse authentication cookies to impersonate legitimate users. They can even mimic the victim’s operating system, browser, and network to bypass Conditional Access Policies (CAP), maintaining long-term access without detection.
How does Cookie-Bite work?
Cookie-Bite is an attack that uses a malicious Chrome extension functioning as an infostealer. This extension targets two critical types of cookies in Azure Entra ID—Microsoft’s cloud-based identity and access management service:
- ESTAUTH: This is a temporary session token that confirms the user has been authenticated and completed MFA. This cookie is valid throughout the browser session, up to 24 hours, and expires when the application or browser is closed.
- ESTSAUTHPERSISTENT: This is the persistent session cookie version, created when the user selects the “Stay signed in” option or when Azure applies the KMSI (Keep Me Signed In) policy. This cookie can last up to 90 days.
Steps of the Cookie-Bite Attack
1. Monitor Login Events:
-
- The malicious extension is programmed to monitor the victim’s login events by listening for tab updates related to Microsoft’s login URLs (such as login.microsoftonline.com).
- When a login event is detected, the extension reads all cookies related to this domain.
2. Extract Cookies:
-
- The extension filters and extracts the two target cookies (ESTAUTH and ESTSAUTHPERSISTENT).
- The cookie data is packaged as JSON and sent to the attacker through a Google Form, ensuring anonymity and making detection difficult.
3. Automate Extension Deployment:
-
- If the attacker has physical or remote access to the victim’s device, they can use a PowerShell script run through Windows Task Scheduler to automatically reinstall the malicious extension every time Chrome starts, exploiting the browser’s Developer Mode.
- According to Varonis, after packaging the extension into a CRX file and testing it on VirusTotal, no security vendors detected the extension as malicious, indicating a high level of sophistication and evasion capability.
4. Inject Cookies and Bypass MFA:
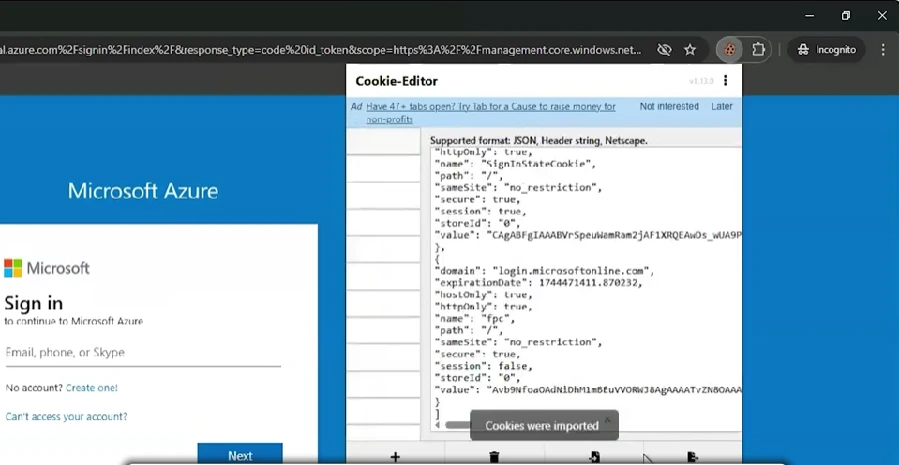
- The attacker uses legitimate tools like Cookie-Editor (another Chrome extension) to import the stolen cookies into their browser, associating them with the domain login.microsoftonline.com.
-
- After refreshing the page, Azure Entra ID considers the attacker’s session fully authenticated, bypassing the MFA requirement and granting access equivalent to the victim’s.
- Further Exploitation:
- With access, the attacker can use tools like Graph Explorer to list users, roles, and devices in the organization.
- They can send messages, access chats on Microsoft Teams, read or download emails from Outlook Web, or even search for sensitive information like stored passwords in emails.
- Advanced actions like privilege escalation, lateral movement, or unauthorized app registration can also be performed using tools like TokenSmith, ROADtools, or AADInternals.
Flexibility of Cookie-Bite
Although designed to target Microsoft’s cookies, this technique can be customized to steal cookies from other services like Google Workspace, Okta, AWS, or even GitHub. Here are some common target cookies:
| Platform/Service | Target Cookie | Purpose |
| Azure Entra ID | ESTSAUTH, ESTSAUTHPERSISTENT | Access Office 365, Teams, Azure Portal |
| Google Workspace/Gmail | SAPISID, SSID, HSID, APISID, NID | Long-term login (Gmail, Drive, etc.) |
| AWS Management Console | aws-userInfo, aws-creds | Maintain session on AWS Console |
| Okta (SSO) | sid, DT, t | Session management on Okta Portal |
| GitHub | user_session, dotcom_user | Login session on GitHub.com |
Other Cookie Theft Methods:
Attackers use various techniques to steal authentication cookies, including:
1. Adversary-in-the-Middle (AITM) Attack:
- AITM is an advanced phishing attack that uses reverse proxy tools like Evilginx, Modlishka, or Muraena to intercept information between the victim and the legitimate authentication service (such as Microsoft 365 or Google).
- When the victim logs in, the proxy records login information, MFA tokens, and session cookies, allowing the attacker to reuse them to bypass MFA without needing a password.
2. Browser Process Memory Dumping:
- Browsers like Chrome or Edge decrypt cookies in memory when a login session is active. Infostealers can inject code into the browser process (such as chrome.exe) to read this memory and extract cookies in plain text, bypassing the need to decrypt from disk.
3. Malicious Browser Extensions:
- Malicious extensions, like in the case of Cookie-Bite, are installed under the guise of legitimate tools but request excessive permissions. They can:
- Access the browser’s storage API.
- Intercept network requests.
- Inject JavaScript code to steal session cookies in real-time.
- This technique is hard to detect because it doesn’t require injecting code into the system or decrypting the disk, and the stolen data is sent directly to the attacker’s server.
- Browsers store cookies in an encrypted SQLite database. For example:
- On Windows: %LOCALAPPDATA%\Google\Chrome\User Data\Default\Network\Cookies (encrypted with DPAPI).
- On macOS: /Library/Application Support/Google/Chrome/Default/Cookies (protected by TCC).
- An attacker needs to:
- Access the cookie database and the encryption key (e.g., the AES key in the Local State file on Windows).
- Decrypt the AES key using DPAPI or steal the DPAPI Master Key from C:\Users\…\AppData\Roaming\Microsoft\Protect.
- DPAPI ties encryption to the user profile and machine, so attackers often have to decrypt on the victim’s device.
Stolen cookies are often valued based on their exploit potential. For example, cookies from enterprise accounts (like Microsoft 365, Google Workspace) are more valuable than social media accounts because they allow attackers to access sensitive data, escalate privileges, or move laterally across the entire enterprise network.
Recommendations
To mitigate the risk from Cookie-Bite and similar attacks, organizations need to implement comprehensive security measures focusing on identity management, monitoring, and browser extension control. Here are in-depth recommendations:
1. Monitoring and Detecting Anomalies
- Monitor Unusual Logins: Microsoft flagged logins in Varonis’s test as “atRisk” due to VPN use (risk type: anonymizedIPAddress). Organizations should enable tools like Microsoft Defender for Cloud Apps or Azure Monitor to detect unusual login behaviors, such as:
- Logins from unfamiliar geographic locations.
- Logins from new devices or browsers.
- Multiple logins in a short time from different IPs.
- Log Analysis: Use Azure Sentinel or SIEM solutions to analyze login logs and access cookies, helping to detect suspicious activities early. For example, detecting two successful logins with the same Session ID from different locations or browsers in a short time.
2. Apply Conditional Access Policies (CAP)
- Restrict Login Scope:
- Set up CAP to only allow logins from trusted IP ranges (e.g., internal networks or company VPN).
- Require devices to be managed by Microsoft Intune and comply with security standards (such as encryption, OS updates).
- Disable the “Stay signed in” option: Disable the KMSI policy to prevent the creation of the ESTSAUTHPERSISTENT cookie, reducing the session cookie’s validity period.
- Token protection: Combine CAP with Token Protection to ensure tokens are only used on valid devices.
3. Strictly manage Chrome extensions
- Apply Chrome ADMX policies:
- Only allow installation of pre-approved extensions from the Chrome Web Store or an internal list.
- Block users from installing extensions from unknown sources.
- Disable Developer Mode:
- Use Group Policy or administrative tools to completely disable Developer Mode on Chrome, preventing the installation of unsigned extensions.
- Monitor extensions:
- Use solutions like Google Workspace Admin or endpoint security tools to check and monitor extensions installed on employee devices.
4. Enhance device security
- Deploy EDR (Endpoint Detection and Response):
- Use solutions like CrowdStrike, Microsoft Defender for Endpoint, or SentinelOne to detect and block malicious activities, including running suspicious PowerShell scripts.
- Control device access rights:
- Apply the principle of least privilege to limit user permissions on devices, reducing the risk of attackers deploying scripts or installing malicious extensions.
5. Raise Awareness and Training
- Employee Training:
- Conduct regular training sessions on cybersecurity, emphasizing the risks of installing unknown extensions or clicking on malicious links.
- Guide employees on how to check and report suspicious extensions.
- Enhance Alerts:
- Provide tools like browser extension scanners for employees to check installed extensions themselves.
6. Regularly Review and Update
- Security Configuration Checks:
- Regularly assess CAP policies, extension management, and MFA configurations to ensure they remain effective against new threats.
- Software Updates:
- Ensure Chrome and other software are always updated to the latest versions to patch security vulnerabilities.
References
Cookie-Bite attack PoC uses Chrome extension to steal session tokens
| Exclusive article by FPT IS Technology Experts
Nguyen Van Trung – FPT IS Cyber Security Center |