DarkSpectre: Unraveling the Chinese Cybercrime Organization Behind 8.8 Million Browsers Infected with Malware
For over a decade of researching cybersecurity, experts have encountered countless malware campaigns—from small opportunistic attackers to organized crime groups. However, on December 25, 2025, researchers from Koi Security discovered one of the most well-funded and sophisticated cybercrime organizations ever recorded, which they named DarkSpectre. This is not just an ordinary hacker group, but a highly organized entity running at least three major malware campaigns, infecting over 8.8 million users across more than 7 years on Chrome, Edge, and Firefox browser platforms.
Scale and Nature of the Threat
DarkSpectre represents a completely different operational model compared to typical opportunistic cybercriminals. This is not three separate hacker groups running similar campaigns—this is a single highly organized entity with three parallel attack strategies, each targeting different objectives: consumer fraud, mass surveillance, and corporate espionage. This diversity of operations, combined with the ability to maintain parallel campaigns across multiple platforms for years, indicates a level of funding, organization, and strategic vision that most threat actors cannot sustain.
In total, researchers have identified nearly 300 browser extensions related to DarkSpectre, including actively malicious extensions, “sleeping” extensions waiting to be weaponized, and those in the trust-building phase. This number not only reflects the scale of the operation but also shows the patience and long-term planning of this organization.
Discovery Chain: From ShadyPanda to the Entire Network
Starting Point: ShadyPanda Campaign
The investigation began with the discovery of the ShadyPanda campaign, one of the largest browser extension malware campaigns ever recorded. Initially, research into ShadyPanda revealed a 7-year campaign infecting 4.3 million users through extensions disguised as productivity tools—new tab pages, translation tools, tab managers—while actually functioning as comprehensive spyware.
After publishing the initial ShadyPanda investigation, researchers decided to revisit and expand the analysis of Indicators of Compromise (IOC). They expected to find a few more related extensions. Instead, they uncovered over 100 additional extensions—a much larger network than initially anticipated.
“Clean Bait” Strategy: Reusing Legitimate Infrastructure
The turning point in the investigation was two domains from the original ShadyPanda research: infinitynewtab.com and infinitytab.com. This is the smartest part of DarkSpectre’s strategy—these domains are not Command & Control (C2) servers or data exfiltration servers. Instead, they are completely legitimate websites providing real functionality for extensions: new tab features, weather widgets, things users actually want.
But DarkSpectre reused these “clean” domains across various extensions connecting to a completely different malicious C2 and exfiltration infrastructure. The legitimate side of their operation became the thread that tied everything together. This strategy allowed the extensions to easily bypass initial reviews, as their main functionality was entirely legitimate and worked as advertised.
Expanding the Investigation: New Clusters Emerge
From the initial two domains, researchers identified extensions communicating with this infrastructure. By delving into their source code, they discovered additional hard-coded domains, API endpoints, and redirect chains. Two new clusters emerged:
Cluster jt2x.com: Extensions use api.jt2x.com for C2 operations, downloading configurations, data theft, and affiliate fraud schemes.
Cluster zhuayuya.com / muo.cc: A separate group using different domains but following the exact same activity patterns.
This process continues to expand in a continuous loop: one domain leads to extensions, those extensions reveal new domains, and those domains connect to even more extensions. Some extensions lead to publishers with dozens of other extensions using completely different infrastructures. The network keeps growing: over 100 extensions on Chrome, Edge, and Firefox.
GhostPoster Connection: Same Technique, Same Actor
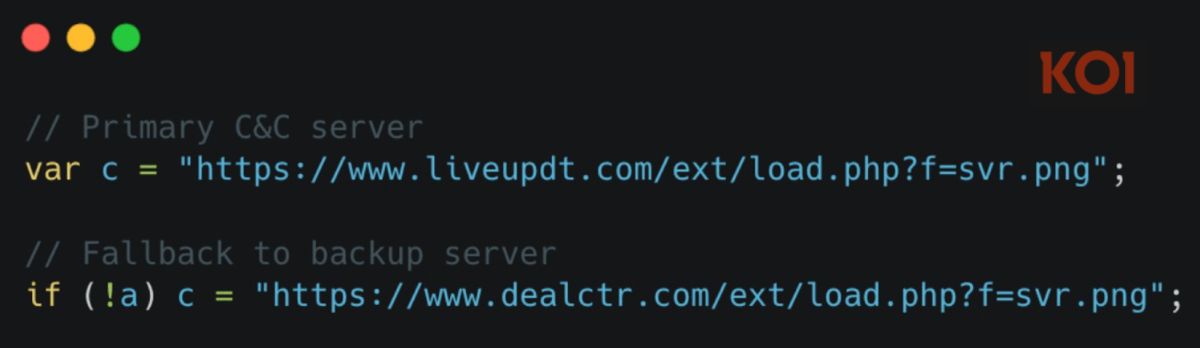
Among the newly discovered extensions is “New Tab – Customized Dashboard” – a sophisticated time bomb extension that waits 3 days before activating. Its C2 infrastructure caught the attention of researchers: liveupdt.com and dealctr.com.
When preparing to flag these domains in the system, a popup warning appeared: “These domains have been flagged as GhostPoster.” These are exactly the same C2 domains they identified in the GhostPoster investigation—a campaign infecting 50,000 Firefox users through malicious PNG icons. The same infrastructure, the same payload delivery technique (code disguised as PNG files), different markets—but the same operator.
Zoom Stealer Connection: Discovery of a Third Campaign
But the investigation isn’t over. An extension appeared during the ShadyPanda expansion that didn’t match the usual pattern: Twitter X Video Downloader. This extension communicates with infinitynewtab.com – the core infrastructure of ShadyPanda. However, when analyzing its behavior, researchers discovered something unexpected: it not only runs data theft and user monitoring but also collects meeting information from over 28 video conferencing platforms.
Following this thread led to 17 other extensions doing the same thing—a completely separate campaign that researchers named The Zoom Stealer, aiming to build a searchable database of business meeting information.
Three Attack Strategies: Diverse Yet Synchronized
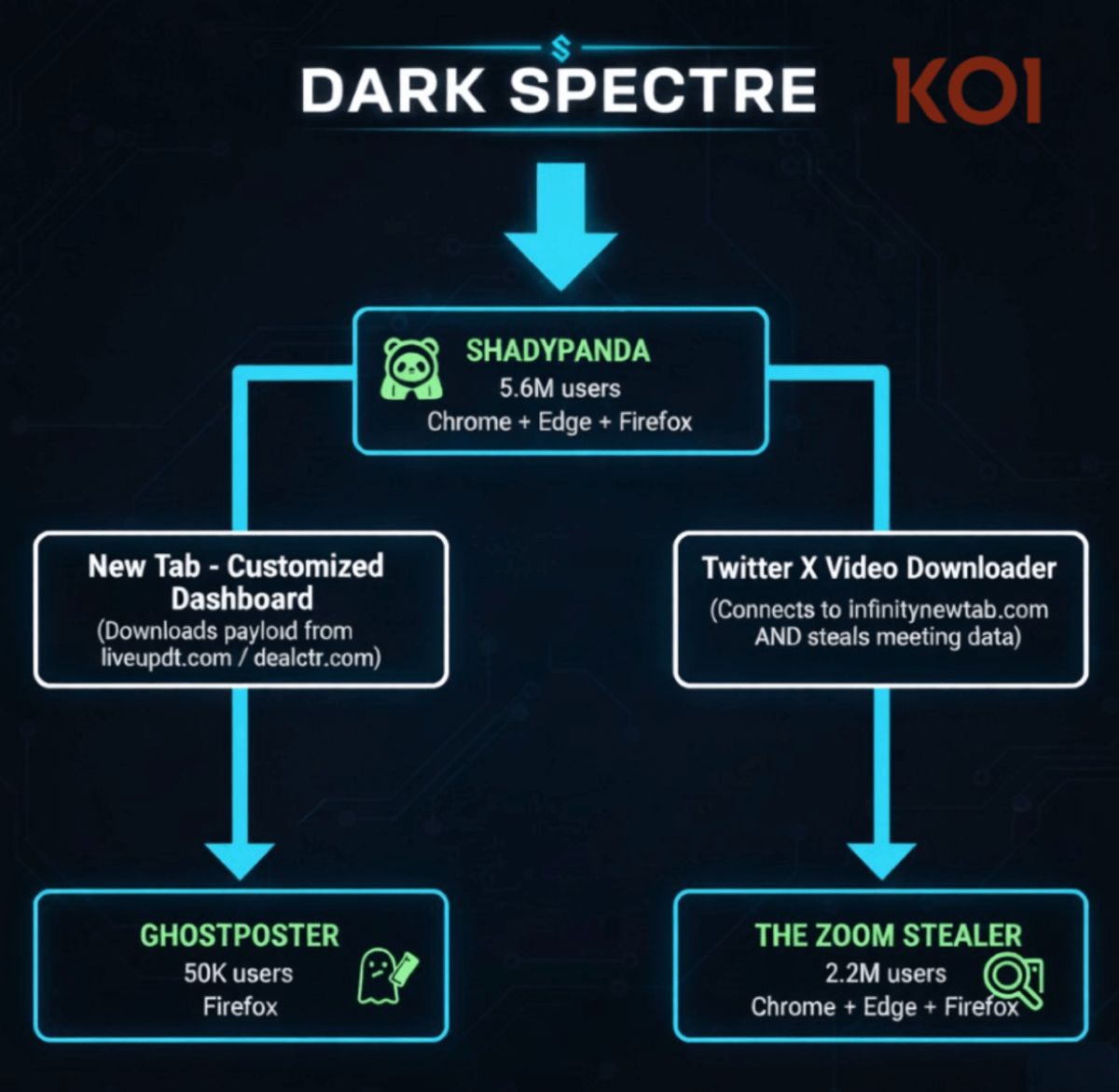
Playbook A: ShadyPanda – The Long Game (5.6 Million Victims)
ShadyPanda represents DarkSpectre’s “long game” strategy with 5.6 million victims across 100+ extensions on Chrome, Edge, and Firefox. The main goal is mass surveillance and large-scale affiliate fraud.
Operational Tactics
ShadyPanda’s operation is designed to build long-term trust before attacking:
- Upload completely legitimate extensions with genuinely useful functionality
- Maintain them for 3-5+ years, providing quality updates and user support
- Earn “Featured” and “Verified” badges from app stores
- Once trust and a large user base are achieved, weaponize the entire user base with a single update
Some extensions ran completely “clean” for over 5 years before turning malicious. This is a level of patience and discipline rarely seen in the cybercrime world.Phân Loại Tiện Ích Mở Rộng
Among the 100+ ShadyPanda extensions discovered:
- 9 active malicious extensions: Currently stealing data, hijacking searches, and committing affiliate fraud
- 85+ dormant extensions: Completely legitimate at the moment, waiting for a weaponized update
jt2x.com Cluster: Four Active Malicious Extensions
Four extensions are currently communicating with api.jt2x.com for C2 operations. Two extensions disguise themselves as translation tools, while the other two present as tab management tools. Behind these useful facades are sophisticated affiliate fraud and data theft activities.
How It Works:
When you install one of these extensions, it immediately contacts to download a malicious configuration. The C2 server responds with a JSON payload, telling the extension exactly what to do. This configuration-based approach means the operators can change the extension’s behavior without pushing an update—they just need to modify what the server returns.
Malicious Activities:
- Remote Code Injection: Downloads and executes JavaScript from bcaicai.com on every website you visit. The operators can change this code at any time—stealing passwords, recording keystrokes, injecting fake payment forms—without needing to update the extension.
- Continuous Tracking: Creates device/user identifiers to track across sessions and build behavioral profiles.
- Search Hijacking: Monitors 9+ search engines, modifying result links to route through tracking links.
- E-commerce Fraud: Targets JD.com and Taobao with URL pattern matching, replacing legitimate links with affiliate versions.
“New Tab – Customized Dashboard”: Timer Bomb Extension
This extension showcases the sophistication of DarkSpectre with delayed activation. When you submit the extension to Chrome or Edge, reviewers check for malicious behavior, but they don’t wait 3 days. The extension appears completely legitimate during the review period, passes all checks, gets approved, and only then activates the malicious payload.
Even better—it only activates on about 10% of page loads, making detection during testing much harder. The code is heavily obfuscated to avoid static analysis. The extension hides eval() calls by using string concatenation and object property access.
After the 3-day waiting period, the extension contacts the C2 infrastructure to download the actual malicious payload. The server responds with ~67KB of encrypted JavaScript disguised as a PNG image—the same technique and domain used in GhostPoster. The extension decrypts and executes this payload on every website you visit. No extension update is needed, and there is no review process to pass.
Payload Content:
- Continuous tracking: Every page you visit, every search you make, every link you click. A user ID is continuously stored in both local and sync storage, persisting even after reinstalling the browser.
- Link fraud: Targets affiliate links on Taobao and JD.com, capturing commissions through hidden redirects.
The entire payload is wrapped in multiple layers of obfuscation—custom encoding, XOR encryption, and packed JavaScript. Every part of this extension is designed to avoid detection.
WeTab: Top Spyware
WeTab remains the most comprehensive spyware in ShadyPanda’s arsenal. It performs:
- Collects full browsing history
- Records search queries
- Tracks clicks with pixel-level accuracy
- Steals personal data to 17 different domains (8 Baidu servers in China, 7 WeTab servers in China, and Google Analytics)
It maintains a dual presence in the Chrome market with over 300,000 combined installations. Still active. Still collecting data.
Playbook B: GhostPoster – Trojan Image (1.05 Million Victims)
GhostPoster represents a different technical approach, targeting 1.05 million Firefox and Opera users through 18 extensions. The goal is to stealthily deliver payloads to Firefox users.
Steganography Technique: Hiding Code in Images
GhostPoster uses steganography – the art of hiding malicious code inside PNG icon files. The extension downloads its own logo icon (an innocent-looking PNG file), extracts hidden JavaScript from within the image data, and then executes it.
This technique is particularly effective because:
- Static analysis tools typically do not check inside image files for code.
- The PNG file looks completely normal to the naked eye.
- The malicious code does not appear in the extension’s JavaScript source code.
Multiple Stage Loading and Evasion
GhostPoster uses a multi-stage loading system with a 48-hour delay and a 10% activation probability. This means:
- After installation, the extension waits a full 2 days before activating
- Even then, it only activates on 1 out of 10 page loads
- This makes detection during evaluations or routine checks extremely difficult
Shared Infrastructure
The most important aspect is that GhostPoster uses the same C2 infrastructure as ShadyPanda: liveupdt.com and dealctr.com. This is decisive proof connecting both campaigns to the same operator.
Playbook C: The Zoom Stealer – Corporate Espionage (2.2 Million Victims)
The Zoom Stealer represents DarkSpectre’s most dangerous target with 2.2 million users across 18 extensions on Chrome, Edge, and Firefox. This is not consumer fraud – this is corporate espionage infrastructure.
Different Target
While ShadyPanda and GhostPoster focus on surveillance, affiliate fraud, and backdoor RCE—monetizing user data while maintaining continuous access, The Zoom Stealer represents something more targeted: systematically collecting corporate meeting information.
Extensions: Useful Tools with a Dark Side
These are not obvious malware. They are functional tools that provide real value:
- Video downloader (actually works)
- Meeting timer (actually works)
- Auto accept assistant (actually works)
- Recording assistant (actually works)
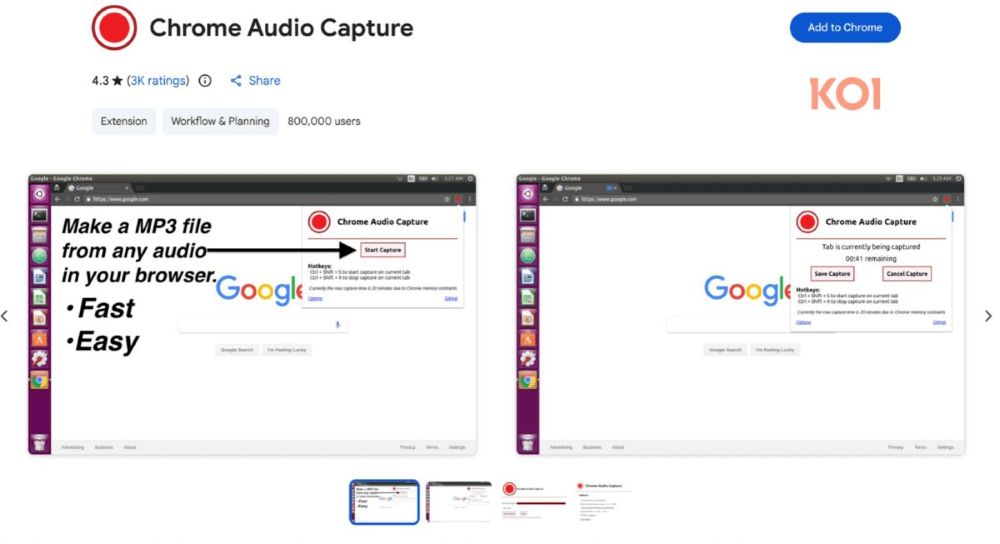
Users get what is advertised. The extensions earn trust and positive reviews. Meanwhile, surveillance runs silently in the background. One standout extension: Chrome Audio Capture with over 800,000 individual installations.
Signs from Access Permissions
Regardless of the stated function, every Zoom Stealer extension requires access to 28+ video conferencing platforms: Zoom, Microsoft Teams, Google Meet, Cisco WebEx, GoToWebinar, ON24, Demio, and 21+ other platforms.
A Twitter video downloader has no reason to access Zoom. A Google Meet timer has no reason to access WebEx. But every extension in this campaign demands access to all of them.
Data Collection Tools
When you visit a webinar registration page with one of these extensions installed, the extension’s content script starts working, scraping the page for any valuable information:
- Meeting URL with embedded password
- Meeting ID
- Topic and description
- Scheduled time
- Registration status
But it doesn’t stop at meeting details. The extensions systematically collect professional information from webinar speakers and organizers:
- Name and title
- Biography
- Profile picture
- Company links
For every webinar you register for, the extensions build a professional profile of the speaker. Beyond individuals, they collect company logos, promotional graphics, and session times—tracking whether registration succeeds or fails.
Real-Time Data Theft
The most alarming aspect is not only the type of data being collected — but how it is being transmitted.
Live streaming via WebSocket connections:
These are not extensions that run periodic checks. Instead, they establish a persistent WebSocket connection that continuously streams your meeting activity in real time. The moment you join a meeting, open a login page, or navigate to a video conferencing platform, the data is immediately sent to the attacker’s server.
Infrastructure
The extensions collect data in the Firebase Realtime Database (zoocorder.firebaseio.com) and track every page visit through Google Cloud Function. This activity uses a legitimate recording service – Zoomcorder.com – as a public front, adding credibility to the infrastructure while serving as a monetization channel.
All 18 extensions in this cluster use webinarstvus[.]cloudfunctions[.]net for data theft.
The Value of Meeting Information
DarkSpectre currently holds meeting data for 2.2 million users. How valuable is it?
Corporate Espionage: Competitors can buy access to strategic meetings, product roadmap discussions, and M&A negotiations. The database contains actual join links.
Sales Intelligence: Knowing which company attends which seminar reveals their interests, pain points, and purchasing timelines.
Social Engineering: Armed with names, titles, bios, and speaker photos, attackers create highly convincing phishing campaigns. “Hello, this is Sarah from the product roadmap webinar you attended…”
Direct Access: Selling meeting links to the highest bidder. Want to eavesdrop on a competitor’s earnings preview?
A Greater Threat
Phishing attacks and corporate espionage have surged in recent years. This campaign seems to be building the infrastructure to launch these attacks on a large scale. By systematically collecting meeting links, participant lists, and business information from 2.2 million users, DarkSpectre has created a database that can power large-scale phishing operations.
Source Analysis: China Connection
All evidence found by researchers points in one direction – a well-funded operation originating from China.
Infrastructure
- C2 servers are consistently hosted on Alibaba Cloud infrastructure in China.
- ICP (Internet Content Provider) registration is linked to Chinese provinces, particularly Hubei.
Source Code Traces
- Chinese language strings throughout the codebase
- Comments and variable names in Chinese
- Development patterns align with Chinese time zones
Attack Targets
- Affiliate fraud schemes specifically designed for Chinese e-commerce platforms (JD.com, Taobao)
- URL pattern matching tailored to the Chinese market structure
Operational Characteristics
- Extreme patience: Maintaining legitimate extensions for over 5 years before weaponizing
- Cross-platform capability: Operating simultaneously on Chrome, Edge, and Firefox
- Diverse targets: Consumer fraud, surveillance, and corporate espionage
- Scale: Over 8.8 million victims requiring significant infrastructure investment
Overall Assessment
The combination of patience, scale, technical sophistication, and diverse activities indicates an adversary with significant resources and long-term strategic goals. Whether DarkSpectre is state-sponsored, state-adjacent, or a well-funded criminal organization with state tolerance, they operate at a level that most threat actors cannot sustain. The discipline to maintain dozens of legitimate extensions for years—waiting for the right moment to weaponize—requires funding, organization, and strategic vision.
Ongoing Threat
Researchers identified DarkSpectre because they have infrastructure IOC to pivot from. They can track remnants from ShadyPanda to GhostPoster to The Zoom Stealer because they share infrastructure. DarkSpectre likely has more infrastructure active right now—extensions that look completely legitimate because they are legitimate, for now.
They are still in the phase of building trust, accumulating users, earning badges, waiting. Only time will tell what else they have prepared while we are detecting these three operations.
And DarkSpectre is just one group. How many other threat actors—China, Russia, North Korea, or others—are running similar long-term operations? Altogether, this group has nearly 300+ extensions found across multiple campaigns. The total number of dormant extensions across all threat actors is unknown.
Security Recommendations
Based on the findings about DarkSpectre, users and organizations should:
- Regularly review installed extensions: Remove extensions that are no longer in use.
- Consider access permissions: Be wary of extensions that request excessive permissions compared to their stated functions.
- Implement continuous monitoring: Marketplaces check once; continuous behavior monitoring is needed.
- Raise awareness: Train employees about the risks from browser extensions.
DarkSpectre has shown that the current security model of extension stores is insufficient to stop organized, patient, and well-funded actors.
Ioc
Domains – The Zoom Stealer
- meetingtv[.]us
- webinarstvus.cloudfunctions[.]net
- zoocorder.firebaseio[.]com
New Domains – Shady Panda
- infinitynewtab[.]com
- infinitytab[.]com
- jt2x[.]com
- zhuayuya[.]com
- 58.144.143.27
- muo[.]cc
- websiteshare[.]cn
- diytab[.]com
- userscss[.]top
- istartnewtab[.]com
- letsearchesp[.]com
- policies.extfans[.]com
New Domains – GhostPoster
- gmzdaily[.]com
Reference
- DarkSpectre Browser Extension Campaigns Exposed After Impacting 8.8 Million Users Worldwide
- DarkSpectre Hackers Infected 8.8 Million Chrome, Edge, and Firefox Users with Malware
- DarkSpectre: Unmasking the Threat Actor Behind 8.8 Million Infected Browsers
- “DarkSpectre” extensions harvest meeting data from 2.2 million browsers
- DarkSpectre Browser Extension Campaigns Exposed After Impacting 8.8 Million Users Worldwide
—————————————————————————
| Exclusive Article by FPT IS Technology Expert Dinh Van Manh – FPT IS Cyber Security Center |