Just 10 meters away, an attacker can turn headphones into a spying device.
A Bluetooth vulnerability can turn wireless headphones into eavesdropping tools and a stepping stone to infiltrate phones without user interaction.
Overview
Bluetooth headsets have long been considered “harmless” personal devices for specific purposes like listening to music, making calls, or supporting virtual assistants. However, at the end of December 2025, security research by ERNW discovered a series of zero-day vulnerabilities that completely changed this perception. A series of serious vulnerabilities in Bluetooth chips developed by Airoha Systems revealed that wireless headphones can become eavesdropping tools and a perfect entry point for hackers in today’s cybercrime world.
The trio of serious vulnerabilities, CVE-2025-20700, CVE-2025-20701, and CVE-2025-20702, were found. These vulnerabilities are not in the application or operating system but originate directly from the firmware and internal protocol of the Bluetooth chip. Even more concerning, attackers do not need a connection, authentication, or user interaction; they only need to be within Bluetooth range to exploit them. From reading/writing headset memory, eavesdropping through the microphone, to stealing connection keys to impersonate the device and access smartphones, the impact goes far beyond traditional Bluetooth risks.
List of Affected Devices
- Beyerdynamic
- Amiron 300
- Bose
- QuietComfort Earbuds
- EarisMax
- Bluetooth Auracast Sender
- Jabra
- Elite 8 Active
- JBL
- Endurance Race 2
- Live Buds 3
- Jlab
- Epic Air Sport ANC
- Marshall
- ACTON III
- MAJOR V
- MINOR IV
- MOTIF II
- STANMORE III
- WOBURN III
- MoerLabs
- EchoBeatz
- Sony
- CH-720N
- Link Buds S
- ULT Wear
- WF-1000XM3
- WF-1000XM4
- WF-1000XM5
- WF-C500
- WF-C510-GFP
- WH-1000XM4
- WH-1000XM5
- WH-1000XM6
- WH-CH520
- WH-XB910N
- WI-C100
- Teufel
- Tatws2
Main Impacts
- Unauthorized eavesdropping.
- Violation of personal privacy.
- Takeover of paired devices.
- Expansion of attacks to smartphones.
- Widespread risk on a large scale.
- Difficult to detect and monitor.
Vulnerability Description
- CVE-2025-20700
- Identifier: CVE-2025-20700
- Severity Level: High
- CVSS Score: 8.8
- Vulnerability Type: EoP
- Description: This vulnerability allows remote privilege escalation without requiring additional execution privileges. User interaction is not necessary for this vulnerability.
- CVE-2025-20701
- Identifier: CVE-2025-20701
- Severity Level: High
- CVSS Score: 8.8
- Vulnerability Type: EoP
- Description: This vulnerability allows bypassing permissions and accessing critical data of the RACE protocol through the Bluetooth LE GATT service.
- CVE-2025-20702
- Identifier: CVE-2025-20702
- Severity Level: Critical
- CVSS Score: 9.6
- Vulnerability Type: EoP
- Description: This vulnerability allows bypassing permissions and accessing critical data of the RACE protocol through the Bluetooth LE GATT service.
Initial Definition
Bluetooth LE GATT ?
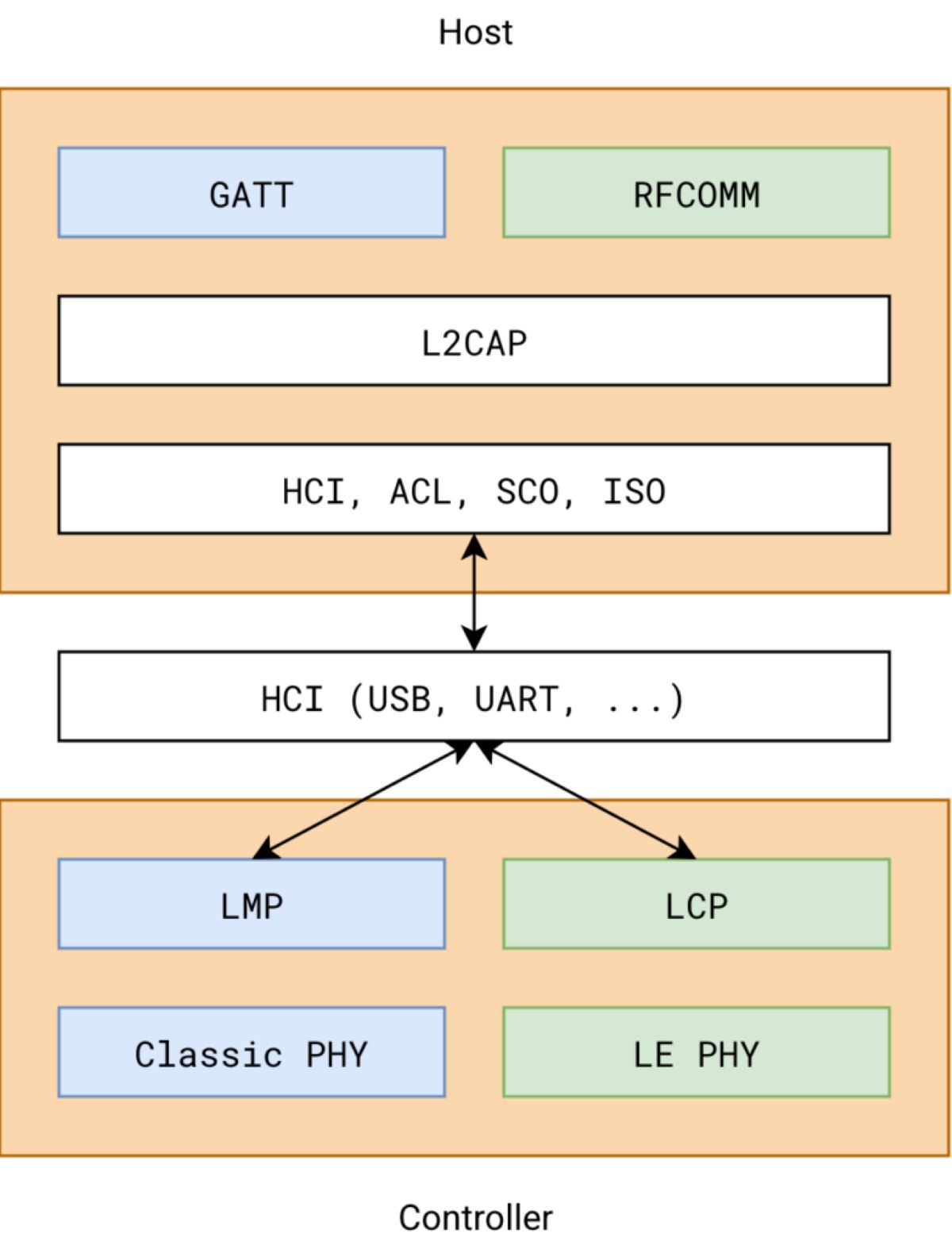
As mentioned above, this chain of vulnerabilities is related to Bluetooth LE GATT (Generic Attribute Profile) and the RACE protocol. Before diving into the details of the vulnerabilities, let’s go through a few definitions in the initial section.
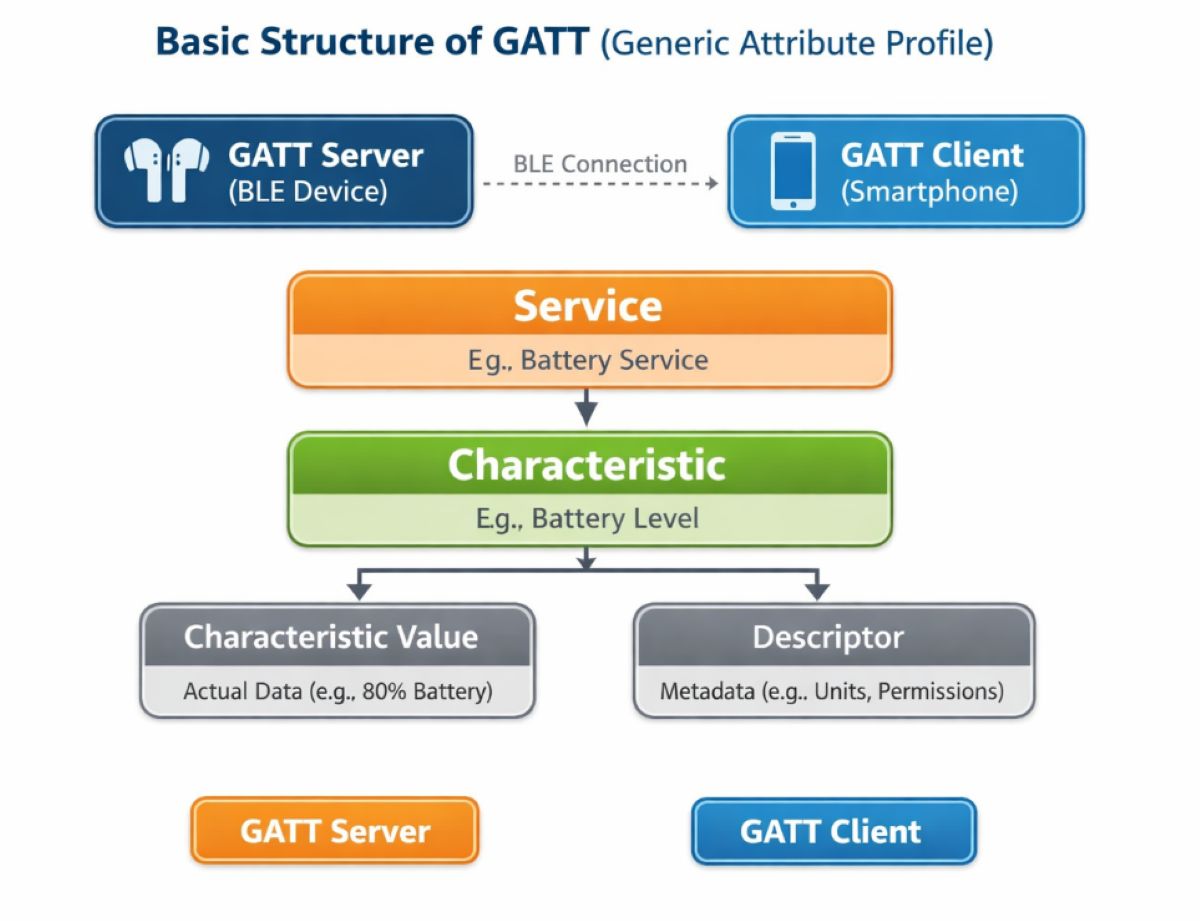
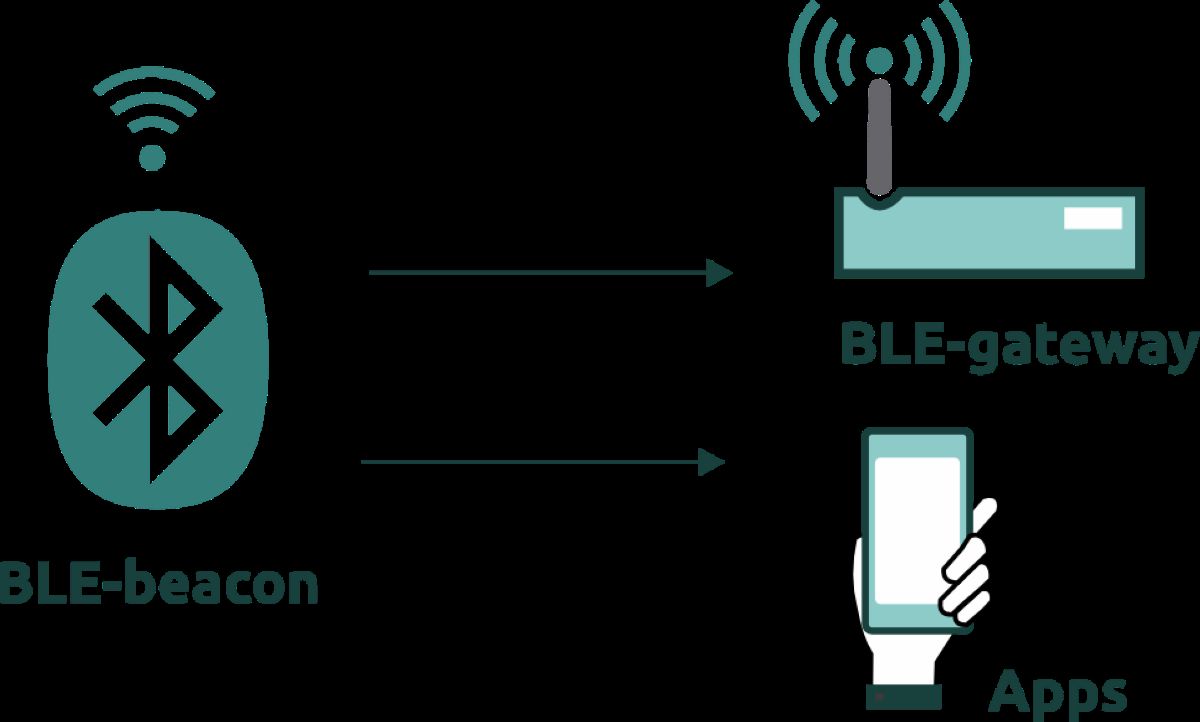
Bluetooth LE GATT (Generic Attribute Profile) is a data communication model used in Bluetooth Low Energy (BLE), allowing Bluetooth devices to exchange data in a standardized, lightweight, and energy-efficient manner. Simply put, GATT defines how a device reads or writes data from another Bluetooth device.
GATT is organized in a hierarchical data model.
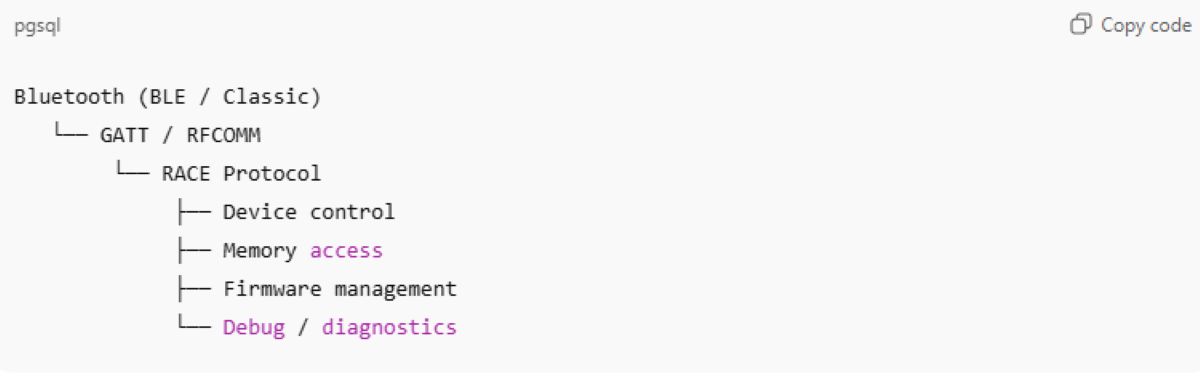
What is the RACE Protocol?
RACE (Remote Access Control Engine) is a vendor-specific protocol designed by Airoha Systems, integrated into the Bluetooth chip firmware used for headphones, earbuds, and wireless audio devices. In Airoha’s architecture, RACE functions as the device’s “management gateway”.
The structural model like this has left some serious security issues with RACE:
- RACE is exposed externally
- Lack of authentication and authorization
- Excessive access privileges
During the analysis, experts identified 4 Commands that attackers could use to exploit:
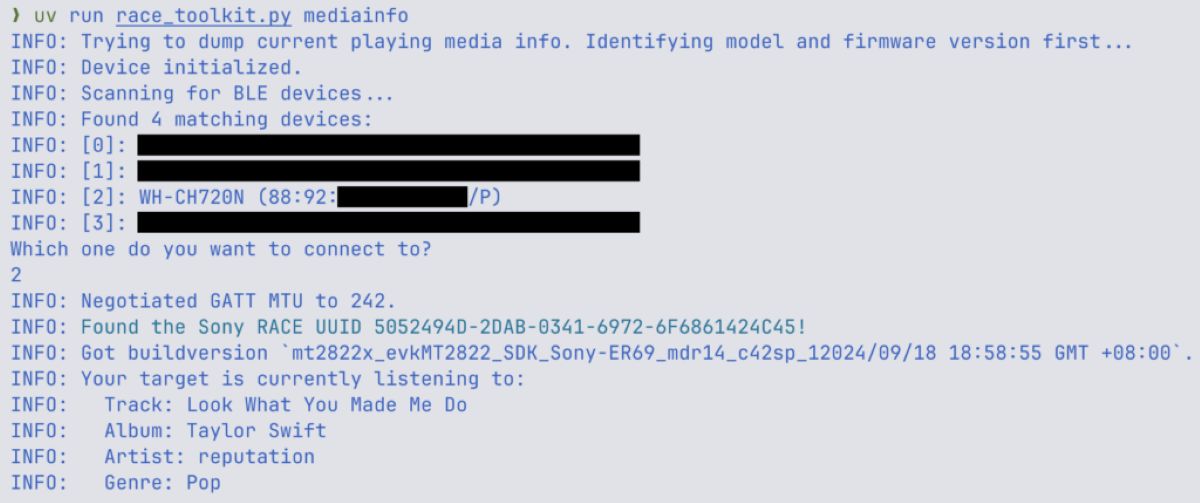
- Get Build Version (0x1E08): This command returns the SOC model as well as the SDK/firmware version. This inadvertently allows for precise device fingerprinting.
- Specific chip line.
- Vulnerable SDK version.
- Build time → speculate patch level.
- Read Flash (0x0403): This command reads data directly from flash memory, including storage areas, page numbers, and memory addresses. This also leads to proprietary firmware leakage, allowing attackers to extract Bluetooth keys, pairing data, or even the device’s internal logic.
- Read/Write RAM (0x1680 / 0x1681): This command can read the entire RAM space. As known, RAM stores and contains runtime states, controls execution flow, and directly interacts with hardware. Once these elements are used, attackers can manipulate the device’s state or simply bypass protection logic.
- Get BD_ADDR (0x0CD5): Returns the device’s Bluetooth Classic public address (MAC) to disable higher-level randomization measures or support passive tracking in public spaces.
What is BLE?
Bluetooth Low Energy (BLE), also known as Bluetooth Smart, was introduced with Bluetooth 4.0.
The main goals of BLE:
- Maximize battery saving
- Support small devices, IoT
- Intermittent communication, no need for continuous connection
BLE operates on a Client – Server model
- GATT Server: BLE devices (e.g., headphones, smartwatches)
- GATT Client: Phones, computers
Attack Process
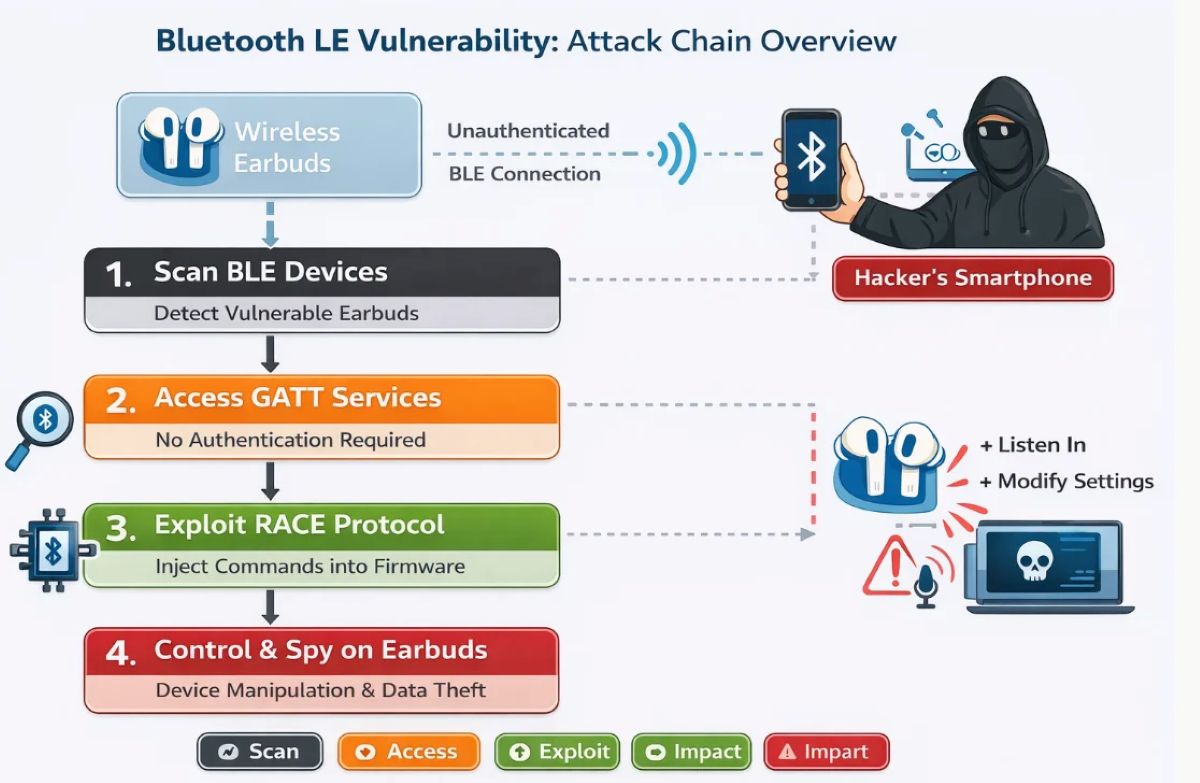
First, to exploit a pair of headphones, the attacker needs to connect to them. To do this, the attacker uses CVE-2025-20700 for initial detection and connection. As mentioned earlier, these headphones often advertise their presence via BLE. Anyone within range (from 10m to 30m) can scan for BLE devices, connect to them, and use the appropriate GATT service to speak the RACE protocol. Here’s the key point: no user consent or button press is needed to connect—something that Bluetooth was originally designed to require.
After successfully connecting to the RACE protocol service, the attacker continues to scan and finds an open GATT service for RACE and accesses it. On Bluetooth Classic, the attacker uses RFCOMM to open a similar channel. Naturally, neither of these processes requires authentication. Since RACE is designed for debugging and flashing firmware, it has very high privileges on the device.
The attacker exploited CVE-2025-20701 at this stage to add a Bluetooth Classic channel and used it to:
- Transmit larger data
- Be more stable than BLE
- Interact deeply with the firmware
After gaining access to the target device, the attacker will attempt to take control using CVE-2025-20702—this is the highest-scoring CVE in this attack chain and the ultimate goal for the attackers. By controlling RACE, the attacker can easily:
- Read RAM information
- Read Flash information
- Dump firmware for analysis
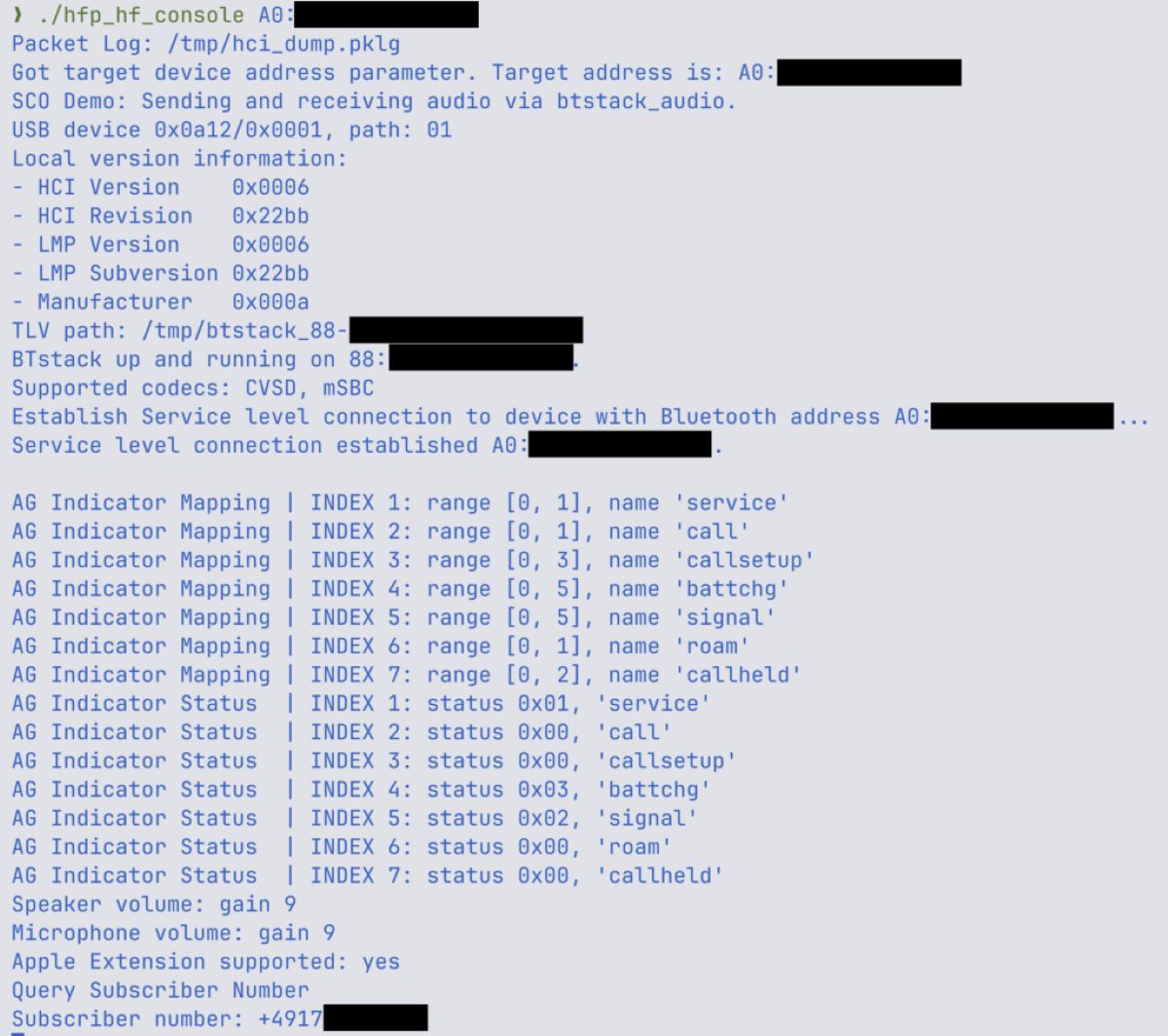
With these actions, the attacker can control your headphones and may use the Bluetooth Hands-Free Profile (HFP) to make/receive calls through the headphones. This could lead to eavesdropping on the microphone or making arbitrary calls by exploiting the link keys obtained.
Another noteworthy point is that having link keys makes it easy to impersonate the legitimate device to steal data.
Conclusion
The Bluetooth Low Energy vulnerability chain analyzed in this article reveals a concerning reality: devices that seem “simple” like wireless headphones actually have a much deeper and more complex attack surface than commonly perceived. Exposing BLE services and internal control protocols without proper authentication, authorization, and access control mechanisms has inadvertently turned headphones into a remote firmware access point.
From a broader perspective, this research serves as a warning to the entire IoT ecosystem: every debug interface, proprietary protocol, and internal function should be considered a potential attack surface. Only when security is integrated from the design stage—rather than through reactive patching—will smart devices truly be safe in an increasingly complex wireless environment.
Recommendations
- Update headphone firmware as soon as possible
- Check and update firmware through the manufacturer’s official app (Sony Headphones Connect, Bose Music, JBL Headphones, etc.).
- Prioritize updates as soon as the manufacturer releases a security patch related to Bluetooth.
- Avoid using outdated or unknown source firmware.
- For Sony version
- For Bose version
- For JBL version
- For Jabra version
- Turn off Bluetooth when not in use
- Do not keep Bluetooth on your phone or laptop if it’s not needed.
- Pay special attention when at:
- Coffee shops
- Airports
- Conferences or crowded events
- Work offices
- Remove unused paired devices
- Delete old headphones and Bluetooth devices from the “Paired devices” list.
- This helps to:
- Reduce the risk of exploiting the Bluetooth Link Key.
- Limit attackers from impersonating legitimate devices.
- Limit the use of Bluetooth headphones in sensitive environments
- Do not use Bluetooth headphones when:
- In internal meetings
- Discussing sensitive information
- Working with important data
- Prefer:
- Wired headphones
- Or devices that have confirmed security patches
- Do not use Bluetooth headphones when:
- Enhance security for paired devices
- Enable a strong screen lock (long PIN, biometrics).
- Limit permissions for:
- Virtual assistants
- Calling/messaging features via Bluetooth when the screen is locked.
- Regularly update the phone’s operating system.
Reference
| Exclusive article by FPT IS Technology Experts
Luu Tuan Anh – FPT IS Cyber Security Center |