Penetration Testing – Vaccine for the digital economy
Penetration testing (Pentesting) is an important field in the cyber security industry and plays a crucial role in securing systems and data from increasingly sophisticated cyber attacks.
The history of Penetration Testing (Pentesting)
Few are aware that pentesting was originated from “phreaking” activities in the 1960s.
In the 1960s, the blossoming of telecommunications and computing technology in the United States marked a new era and has forever changed the lives of people ever since. Methods of communication and information exchange between people (telephone, radio, etc.) and computing machines made great progress. All of these technologies were commercialized, making them accessible and usable to anyone.
This was also the time when exploits began, and is considered the origin of what we now call “hacking”. Hacking was started by a small group of telephone network users. After a period of use and observation, they discovered a number of vulnerabilities in the telephone network’s switching system, which allowed them to perform multiple actions such as: call spoofing, free calling, eavesdropping, information theft, etc. These acts were quickly spread and shared with many others (although they are illegal now, these acts were not prohibited at that time as no relevant laws were enacted yet). From there, people who shared the same passion and extensive knowledge of this exploitation gathered, formed a community and engaged in it enthusiastically. The term “phreaking” was created to define exploitation actions, and those who performed these actions call themselves “phreakers”.
The photo depicts the Phreaking activity of a group of phreakers in 1971 taken by Bob Gudgel (Wired magazine)
In the early 1970s, as Phreaking activities flourished, some phreaker groups developed specialized devices for automated exploitation and sold them to general users. This caused significant damage to telecommunications networks. The US Government and the US Department of Defense identified this as a criminal act. However, they also acknowledged potential risks related to national security and defense, as well as extensive effects in the near future. The US government and companies thus joined hands to establish and sponsor groups called “Tiger teams”. The mission of these groups was to research network/computer systems to find and figure out ways to exploit vulnerabilities or risks, before they were discovered by any phreaker groups or anyone else. The term “Penetration Testing” was consequently created, and is nowadays referred to as “pen-testing” or “pentest”.
Talking about pentesting without mentioning James P. Anderson would be a mistake. He is a computer scientist and security expert, who developed a comprehensive and refined process that enabled ‘tiger teams’ to operate more professionally and increase the effectiveness of pentesting activities. Today, this process is still considered a foundation model. Thanks to those great contributions, · James P. Anderson ·is widely known as the father of pentesting.
From the beginning of phreaking, the field of pentesting in particular, and security in general, has grown to become an integral part of all organizations, from governments to enterprises, as humanity enters a new era of the digital economy.
The application of pentesting has widely spread across various fields, from the military to commercial businesses. Pentesting techniques and tools are constantly evolving, helping to improve the efficiency and accuracy of system security assessment.
The importance and benefits of Pentesting in the era of digital economy
In the digital economy era, in which data becomes a valuable asset and cybercrime increases, pentesting becomes more crucial than ever. In particular, for important systems/products that contain sensitive information, pentesting will usually be conducted continuously from the beginning until the end of the product’s life cycle.
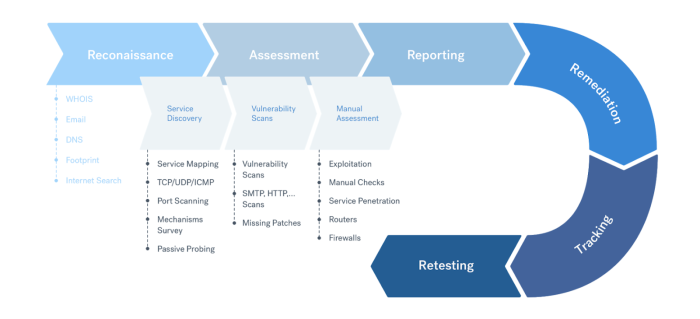
Description of the penetration testing process (Source: Cobalt.io).
Nowadays, pentesting plays an essential role in protecting businesses from cyber attacks, including:
- Detect and resolve security vulnerabilities: Pentesting helps identify weaknesses in systems, applications and networks, allowing organizations to take timely corrective measures for cyber attack prevention.
- Improve cyber defenses: Pentesting enables businesses to evaluate the security level of their systems, putting in place effective preventive measures to minimize the risk of attack, getting a clearer view of the overall security picture, the challenges faced, and how to address them.
- Enhance customer trust: Through Pentesting and vulnerability patching, businesses can enhance consumer trust in their data protection capabilities and improve their products and services to be more comprehensive and reliable.
- Follow regulations: Many data security regulations requires businesses to periodically perform Pentesting to ensure compliance.
- Raise security awareness: Pentesting helps raise employees’ awareness of the importance of security and encourages them to implement safe protection measures for the system.
“Vaccine dose” to protect data for organizations in the digital era
After 60 years, humanity has taken great leaps, with phreakers using classic telephone systems now part of history, but cybercrime has evolved into dangerous forces, posing a constant threat to any organization or individual. However, as time goes on, the “white-hat hackers” teams (referred to as pentesters) have become increasingly skilled and proficient. They continue to quietly search for vulnerabilities and potential risks within systems, alerting companies and organizations to fix any issues before hackers discover and take advantage of them.
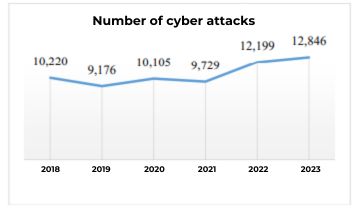
Statistics of cyber attacks in Vietnam (Source: Ministry of Information and Communications, report dated January 19, 2024)
In 2023, the Vietnamese Ministry of Information and Communications issued warnings and guidelines on how to handle 12,846 cyber attacks, an increase of 5.3% compared to 2022. Government organizations, financial institutions, banking systems, industrial systems, and other crucial systems were the targets that saw the most attacks over the previous year. In that context, Pentest service becomes an urgent and continuous need for organizations and businesses to test and detect security vulnerabilities, perform system penetration testing.
According to a Mordor Intelligence report, the market size for penetration testing is expected to reach USD 12.76 billion by 2029, rising at a CAGR of 24.59% over the forecast period (2024–2029). The growth of Pentest has resulted in the appearance of numerous individuals and organizations offering cybersecurity services, posing a challenge for customers to seek for a reliable and competent cybersecurity service provider. Thanks to becoming an official member of the CREST organization, FPT IS can demonstrate credibility and capability in the field of cybersecurity testing. We are also given plenty of opportunities to connect with over 300 partners and potential customers within the CREST community.
The annual number of cyberattacks has been rising quickly so far, making any individual or business a potential “easy prey” for cybercriminals. Therefore, equipping your system with “vaccines” is extremely critical to maintain safety in a dynamic network environment that presents both possibilities and hazards.
In Vietnam, there are already many individuals who have achieved international standards, or organizations that provide standard pentest services and have been evaluated and certified by international bodies. Therefore, we can be fully confident that Vietnam has the capability to compete fairly with international peers and provide high-quality services and the best values to customers and partners.
FPT IS is now among the few companies operating in the field of cybersecurity in Vietnam that meets the qualifications to be an official member of CREST after passing the rigorous assessment process of the CREST organization. FPT IS is also currently the only company in Vietnam to hold both the CREST certification for Pentest service and PCI.QSA certification for consultant, assessment and validation of one’s compliance to PCI DSS.
FPT IS has officially become a member of the CREST organization for Penetration Testing Services (Pentest)
Learn more about FPT IS’s capabilities and services in the Information Security and Cybersecurity industry at: https://fpt-is.com/bao-mat/
——–
Exclusive article by FPT IS Technology Expert
Pham Viet Hoa
Information Technology Security Engineer
Cyber Security Center – FPT IS.