DragonRank Campaign: When IIS Servers Became Tools for Hackers
Introduction
The hacker group DragonRank has recently become a serious threat by targeting Microsoft’s Internet Information Services (IIS) servers, exploiting unpatched vulnerabilities to gain control of the systems.
Technical Details
According to Microsoft, the vulnerability exploited by DragonRank involves handling HTTP Request Headers on IIS. Specifically, the attacker sends a specially crafted HTTP request with a header containing data that exceeds the buffer limit, causing a Buffer Overflow. This allows them to overwrite memory and execute arbitrary code (Remote Code Execution – RCE).
- Exploitation Mechanism:
When the IIS server parses headers likeContent-LengthorTransfer-Encoding, improper handling of unusually large values leads to a buffer overflow. DragonRank exploits this weakness to inject malicious code into memory and then triggers the payload to take control. - Malware Used:
According to a report from Cisco Talos, the group uses a variant of the ChinaChopper malware—a common webshell in attacks on web servers. This malware allows hackers to upload other tools like ransomware or cryptocurrency mining software.
DragonRank Campaign
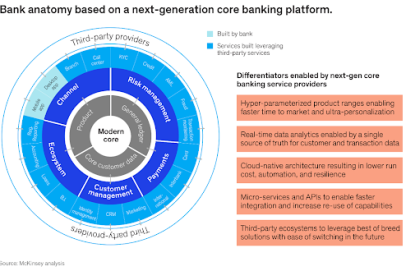
DragonRank is not just a random hacker group but a well-organized entity with clear strategies, regularly conducting large-scale attack campaigns. Here are some key details about their campaign:
- Targets:
DragonRank focuses on financial institutions, government agencies, and large enterprises in the Asia region, especially Southeast Asia and India. The targets often have complex IT systems but lack full security updates. - Attack Methods:
- Reconnaissance: Using scanning tools like Nmap and Shodan to identify unpatched IIS servers.
- Exploitation: Leveraging buffer overflow vulnerabilities to deploy webshells and gain control.
- Persistence: Installing backdoors and malware to maintain long-term access.
- Lateral Movement: Using stolen information to attack other systems within the same internal network.
- Tools Used:
- Webshells: ChinaChopper, C99, and custom variants.
- Exploit Kits: Utilizing exploit kits like Metasploit and Cobalt Strike.
- Anonymity Tools: Using VPNs and proxies to hide IP addresses.
- Objectives:
- Data Theft: Collecting sensitive information such as customer data and trade secrets.
- DDoS Attacks: Turning compromised servers into botnets to launch denial-of-service attacks.
- Financial Gain: Installing cryptocurrency mining malware (cryptojacking) on servers to earn profits.
Scope and Impact of the Attack
- Victims:
A report from Kaspersky Lab indicates that over 500 IIS servers in Southeast Asia and India were compromised in February 2025. Many of these servers belong to banks and healthcare agencies that have not updated Microsoft’s patches. - Impacts:
- Data Breach: Configuration files containing credentials (username/password) were stolen and sold on the dark web.
- DDoS Attacks: Some servers were turned into botnets to launch denial-of-service attacks on other targets.
Recommendations
- Microsoft:
Immediately apply the latest patch for IIS and enable Request Filtering to block HTTP requests with invalid headers. - CERT Coordination Center (CERT/CC):
Implement Network Segmentation to isolate web servers from critical internal systems. Use monitoring tools like Azure Sentinel or Splunk to detect suspicious activity. - Allow only the minimum necessary access. Also, regularly scan with tools like Nessus or Qualys to identify vulnerabilities.
Conclusion
The DragonRank attack on IIS not only highlights the sophistication of hackers but also underscores the importance of system updates and enhancing security awareness. Organizations need to combine multiple layers of security (multi-factor authentication, encryption, continuous monitoring) to minimize risks.
References
- Analyzing the BadIIS Malware Campaign: A Global Threat Exploiting IIS Server Vulnerabilities
- Hackers Compromising IIS Servers to Deploy BadIIS Malware
- Chinese DragonRank Hackers Exploit Global Windows Servers in SEO Fraud
- DragonRank SEO Attack: The Hidden Manipulation of IIS Servers
- DragonRank Exploits IIS Servers with BadIIS Malware for SEO Fraud and Gambling Redirects
| Exclusive article by FPT IS Technology Experts
Dinh Van Manh – FPT IS Cyber Security Center |