Multi-factor Authentication in Finance – Banking Transactions
The explosion of digital transactions in Banking – Finance
All socio-economic activities will inevitably follow the current global trend of traditional (over the counter) transactions giving way to digital transactions in Vietnam. Being the backbone of the economy, the finance and banking sectors must transition to digitalization as quickly as possible to support a more robust national digital transformation process.
The State Bank (SBV) released statistics indicating that in 2022, there were almost 48% more transactions through the Internet Banking channel than in 2021, with a value increase of over 1,328%, from VND 811,717 billion to VND 10,868,458 billion; additionally, there were 100% more transactions through Mobile Banking. Up to 8 million transactions on average were conducted every day by the end of 2023, with a total transaction value of over VND 900,000 billion or USD 40 billion.
Network security and safety concerns become more complex as digital transaction services are implemented. The frequency of cyberattacks linked to banking and finance is rising along with the level of damage. The reason for this is that hackers target industries with high transaction values, like finance and banking to make illicit earnings. As a result, organizations in these sectors must always be cautious about network security threats and dangers. In the first 11 months of 2023, Vietnamese Internet users reported almost 16,000 fraud cases through warning systems of which over 91% involved in fraud warnings in the finance and banking sector according to statistics provided by the Ministry of Information and Communications.
Single-factor and multi-factor identity authentication
Identity authentication is the process of verifying the legitimacy of a service user. The purpose of this verification is to prevent impersonators from using successful impersonation to gain unauthorized access to services that they are not allowed to use.
Building a set of representative user characteristics that correspond to the matching set of real users is a prerequisite for identity authentication. Users of digital transaction services engage in an interactive process that is facilitated by their representative characteristics rather than by the users themselves. Identity identification must therefore guarantee that no one else can replicate a person’s unique characteristics.
In single-factor identity authentication, a user’s identity is linked to a password that only the user knows. When using the service, the user provides an identity and password to the system. The identity and password are compared to the matching stored identity and password set by the system. If the information is accurate, the user is successfully authenticated and given access to the service based on the system’s authorization.
Since the password is the only factor, it is easy for another user to impersonate a user if the password is revealed. Additionally, the system itself needs an operating mechanism to ensure that when users store or send data over a network, their passwords remain secret. We utilize a new, user-specific factor in addition to the password to make the authentication process harder to falsify. This factor is completely different from the first factor to enable two-factor authentication. To be more secure, we use a third factor in addition to the first two to enable three-factor authentication. The authentication process that uses two or more factors is called multi-factor authentication. For multi-factor authentication to be effective, the user-specific factors chosen must be unique from one another and devoid of any similarities.
Multi-factor authentication often includes the following types of factors:
- First factor: Password, personal identification number (PIN). Obviously, you need to select a PIN or password that is difficult for other people to figure out.
- Second factor: Select an item, like a smart card, that is unique to the authorized user, is typically carried with them, and cannot be duplicated.
- Third factor: User’s biometric characteristics unique to the individual user. It might be a voice, face, iris, fingerprint, etc.
- Fourth factor :Accurate location of the user is determined without confusion. That is the IP address for computers.
- Fifth factor: Observe user behaviors such as: Touches and movements, like pattern passwords, for example.
Biometric authentication
Biometric authentication system is based on “who you are”. Compared to “what you know or have” authentication, it offers numerous advantages. Biometric solutions, for example, can eliminate the inconvenience of having to memorize lengthy passwords or losing tokens. Biometric authentication has become a commonly used and reliable method of access control.
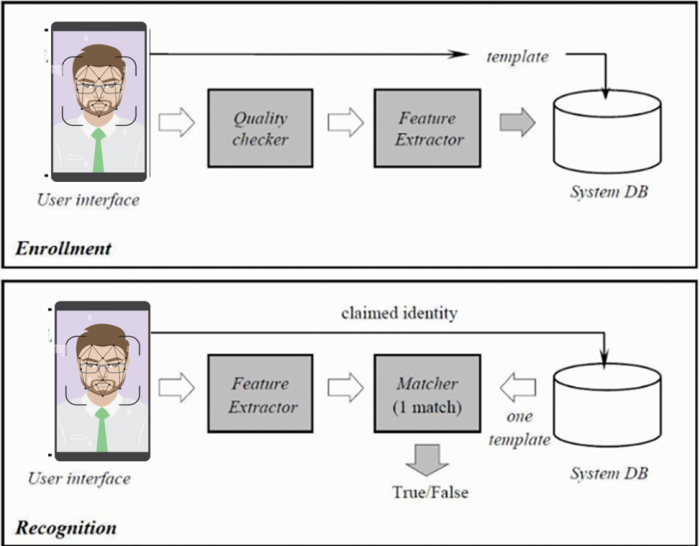
The biometric authentication model includes two stages: Enrollment and Recognition as shown below:
The registration phase includes the following steps:
- Biometric data acquisition (Biometric sensor and Input Image)
- Feature extractor
- Reference template creation (Template)
- Database storage (Database)
In a biometric authentication system, the registration phase is the most important step. The results of the phase are reference samples, which play a vital role in the ultimate success of authentication. As a result, the accuracy of the biometric features used is determined by the quality of the reference sample.
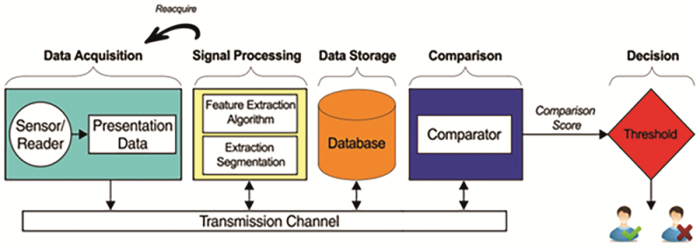
The registration phase includes the following steps:
- Data Acquisition
- Feature Extraction (Signal Processing)
- Reference sample comparison (Comparison)
- Decision making
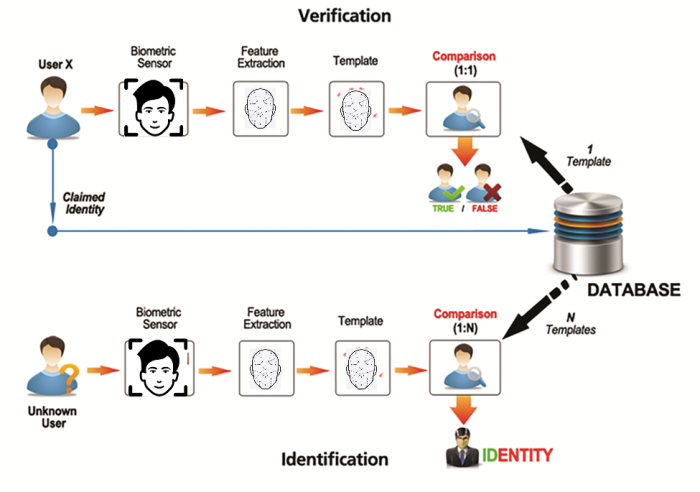
Depending on the nature of the identification system or verification system, the matching step with the reference sample varies (1:1 match for verification and 1:N match for identification).
Facial authentication is the most frequently used technology in real-world business applications currently among the various biometric authentication techniques for the following reasons:
- Low investment on terminals: Devices with cameras are only needed to take photos/videos of faces during the registration stage and transaction identification. All smartphones now have high-quality cameras, making facial biometric technology compatible with them.
- AI models used in facial biometric technology have increasingly improved and become more accurate.
However, biometric authentication can still be spoofed when a hacker successfully impersonates a user by falsifying biometric data obtained from the user. Hackers often use the following methods:
- During the registration phase, create fake samples using 3D printed samples, pre-staged pictures and films, or still photos.
- Hack the app to change biometric characteristics that are entered during the identification process.
Biometric authentication at Vietnamese financial and banking institutions
According to Decision 2345/QD-NHNN dated December 18, 2023 of the State Bank of Vietnam: from July 1, 2024, payment service providers and payment intermediaries on the Internet are required to use the following minimum authentication solutions:
Following a time of implementation, many shortcomings in Decision 630/QD-NHNN were discovered, exposing opportunities for hackers to take advantage of illegal money transfer transactions, including bank account hacking, scamming, and leasing/borrowing accounts. On October 12, 2023, the State Bank issued a document requesting feedback on the draft amendment to Decision 630/QD-NHNN dated March 31, 2017 in regards to solutions for safety and security in online payments and card payments.
The draft introduces a number of significant modifications to help ensure the security of payment transactions. Specifically:
| No | Transaction | Minimum authentication measure | |
| Individual customers | Business customers | ||
| 1 | Class A transaction | – Username, password or PIN (there is no need to authenticate at the transaction step if you have already authenticated at the login step). | – Username, password or PIN (there is no need to authenticate at the transaction step if you have already authenticated at the login step). |
| 2 | Class B transaction | – OTP sent via SMS, Voice, Email or OTT.
– Or OTP Matrix Card. – Or basic Soft OTP/Token OTP. – Or two-factor authentication – Or biometric identifiers associated with a smart handheld device – Or advanced Soft OTP/OTP Token – Or under the FIDO standards – Or by secure electronic signature |
– OTP sent via SMS, Voice, Email or OTT.
– Or OTP Matrix Card. – Or basic OTP Token, without Token user authentication function – Or by the biometric identifiers of the legal representative or the person in charge of accounting (if any) of the customer associated with a smart handheld device |
| 3 | Class C transaction | – By the customer’s biometric identifiers:
(i) matches the biometric data stored in the customer’s police-issued citizen identification card chip; (ii) or via the electronic identification and authentication system’s verification of the customer’s electronic identity – Or by the customer’s biometric identifiers that matches the biometric data stored in the customer biometric database that has been collected and verified, and can be combined with other methods like OTP authentication sent via SMS/Voice or Soft OTP/OTP Token |
-Soft OTP or basic OTP Token serves as a means of user authentication through the use of software and a Token
– Or two-factor authentication
|
| 4 | Class D transactions | By the customer’s biometric identifiers:
(i) matches the biometric data stored in the customer’s police-issued citizen identification card chip; (ii) or via the electronic identification and authentication system’s verification of the customer’s electronic identity; (iii) or matches the biometric data stored in the collected and verified customer biometric database, combining one of the following authentication measures: – Advanced Soft OTP/OTP Token – Or under the FIDO standards – Or by secure electronic signature |
– Advanced Soft OTP/OTP Token
– Or under the FIDO standards – Or by secure electronic signature |
Definition of transaction classification:
| No | Transaction type | Class A transaction | Class B transaction | Class C transaction | Class D transactions |
| I | Retail customers | ||||
| 1 | Group 1.1:
– Information lookup transactions – Money transfer within the same bank, same account holder |
All transactions | |||
| 2 | Group 1.2:
Payment transactions for legal goods and services are provided by payment service providers and payment intermediaries or at payment acceptance units operated by payment service providers and intermediaries, who are in charge of selection, appraisal, monitoring and management. |
Transactions meet the following conditions:
G + T <= VND 5 million |
Transactions meet the following conditions:
(i) G + T <= 5 million VND (ii) G + T <= 100 million VND |
Transactions meet the following conditions:
(i) G + T <= 100 million VND (ii) G + T <= 1,5 billion VND |
Transactions meet the following conditions:
G + T > VND 1.5 billion |
| 3 | Group 1.3:
– Money transfer within the same bank, different account holders – Domestic interbank money transfer – Money transfer between e-wallets – Money deposit into e-wallets – Money withdrawal from e-wallets |
Transactions meet the following conditions:
(i) G <= 10 million VND (ii) G + Tksth <= 20 million VND (iii) G + T <= 1,5 billion VND |
Transactions meet one of the following conditions:
1. Case 1: Transactions meet the following conditions: (i) G <= 10 million VND (ii) G + Tksth > 20 million VND (iii) G + T <= 1,5 billion VND 2. Case 2: Transactions meet the following conditions: (i) G <= 10 million VND (ii) G <= 500 million VND (iii) G + T <= 1,5 billion VND |
Transactions meet one of the following conditions:
1. Case 1: Transactions meet the following conditions: (i) G <= 10 million VND (ii) G + Tksth > 20 million VND (iii) G + T > 1,5 billion VND 2. Case 2: Transactions meet the following conditions: (i) G <= 10 million VND (ii) G <= 500 million VND (iii) G + T > 1,5 billion VND 3. Case 3: Transactions meet the following conditions: G > VND 500 million |
|
| 4 | Group 1.4:
Overseas interbank money transfer |
Transactions meet the following conditions:
(i) G <= 200 million VND (ii) G + T <= 1 billion VND |
Transactions meet one of the following conditions:
1. Case 1: Transactions meet the following conditions: (i) G <= 200 million VND (ii) G + T > 1 billion VND (iii) G + T > 1,5 billion VND 2. Case 2: Transactions meet the following conditions: G > VND 200 million |
||
| II | Business customers | ||||
| 1 | Group II.1:
Information lookup transactions |
All transactions | |||
| 2 | Group II.2:
Money transfer within the same bank, same account holder |
All transactions | |||
| 3 | Group II.3:
– Money transfer within the same bank, different account holders – Domestic interbank money transfer Payment transactions for legal goods and services are provided by payment service providers and payment intermediaries or at payment acceptance units operated by payment service providers and intermediaries, who are in charge of selection, appraisal, monitoring and management – Money transfer between e-wallets – Money deposit into e-wallets – Money withdrawal from e-wallets |
Transactions meet the following conditions:
(i) G <= 1 billion VND (ii) G + T <= 10 billion VND |
Transactions meet one of the following conditions:
1. Case 1: Transactions meet the following conditions: (i) G <= 1 billion VND (ii) G + T > 10 billion VND 2. Case 2: Transactions meet the following conditions: G > VND 1 billion |
||
| 4 | Group II.4:
Overseas interbank money transfer |
Transactions meet the following conditions:
(i) G <= 500 million VND (ii) G + T <= 5 billion VND |
Transactions meet one of the following conditions:
1. Case 1: Transactions meet the following conditions: (i) G <= 500 million VND (ii) G + T > 5 billion VND 2. Case 2: Transactions meet the following conditions: G > VND 500 million |
In which:
- G: Transaction value
- Tksth: Total amount of type A and type B transactions for each group of transactions made in a bank account (including deposit transactions into e-wallets) or in an e-wallet (not including deposits into e-wallets) Tksth of a bank account/e-wallet is calculated as 0 at the start of the day or right after that bank account or e-wallet has a transaction throughout the day using authentication measures for Type C or Type D transactions.
- T: Total value of each group of transactions made in a day in a bank account (including deposit transactions into e-wallets) or in an e-wallet (not including deposits into e-wallets).
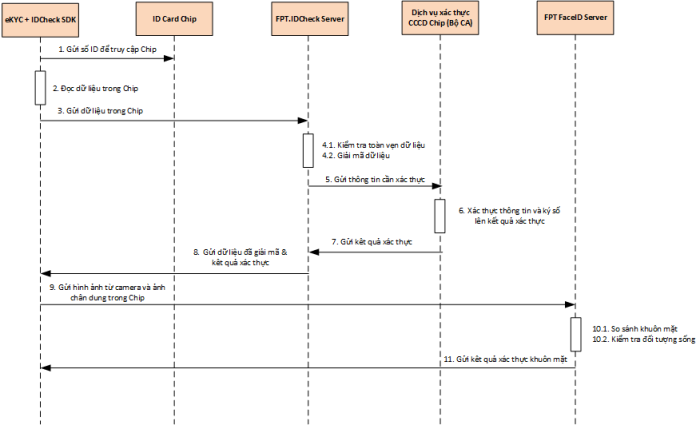
To comply with the State Bank’s regulations as mentioned above, financial and banking institutions in Vietnam must build a centralized biometric authentication system that combines Chip ID cards and electronic identification (VNeID). By simply requiring customers to authenticate their ID Chip cards when making transactions, financial and banking institutions have added two additional factors in the multi-factor identity authentication process:
- First factor: Item (ID Chip card) that is unique to the authorized user, is typically carried with them, and cannot be duplicated.
- Second factor: User’s biometric characteristics unique to the individual user (fingerprint, face stored in the ID Chip card).
FPT IS has built the FPT.IDCheck solution, which integrates ID Chip cards into the multi-factor authentication process:
FPT.IDCheck solution helps Financial and Banking organizations have the ability to almost completely prevent identity authentication fraud:
- Prevent using fake ID cards
- Prevent taking/recording pre-staged videos from other devices
- Prevent app activation on simulated virtual machines (simulator)
- Have a mechanism to verify the source of images or videos before submitting them to the processing server
- Have advanced AI models that prevent deepfakes created by face-matching AI software
- Create a facial biometric blacklist of suspicious people who are questionable or have a history of dishonest activity
- Compare the collected customer facial biometrics each time the customer makes a transaction to minimize risks
- Compare customer facial biometric data with facial biometric data from the residential database via ID Chip card
Approximately 30 Vietnamese financial-banking organizations have successfully implemented the solution thus far, and by 2024, it is anticipated that this number will have increased to roughly 50.
Conclusion
Finance and banking companies must include biometric authentication into their multi-factor identification authentication process due to the rise in digital transactions in the industry and the associated significant security issues. Specifically, facial biometric authentication is the best approach due to its high security, ease of implementation, and most importantly, its seamless integration with residential databases via ID Chip cards and the upcoming electronic identity card (VNeID).
Exclusive article by FPT IS Technology Expert
Phan Thanh Toan
Director of Digital Authentication Solutions
FPT Information System Company