Outstanding cybersecurity trends for operational technology (OT)/industrial control systems (ICS)
In the face of increasingly sophisticated and complex cyberattacks, OT/ICS systems – responsible for monitoring and controlling physical devices and processes in industrial facilities such as power plants, water plants, oil and gas refineries, transportation systems, and smart buildings – are encountering numerous risks and challenges.
Meanwhile, due to the nature of OT/ICS systems, any infiltration or sabotage can cause physical damage to the environment, production, daily life, and human health and safety. Understanding security trends for OT/ICS, therefore, is crucial for agencies and organizations to construct robust “digital fences” around essential national infrastructures, contributing to the stability and quality of life for the populace.
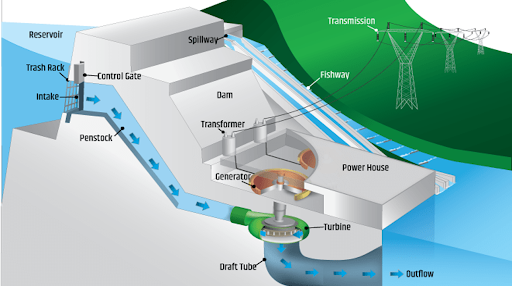
Operation model of a hydropower plant, controlled by an industrial control system. (Image: US Department of Energy)
1. Cybersecurity risks for OT/ICS systems
1.1. Security weaknesses exposed by IT/OT convergence
Last year, 7% of industrial organizations were targeted by cyber attacks, with 26% of those being attacked weekly. Historically, industrial control systems were safeguarded by two principles: (1) Air Gap Security, in which OT/ICS systems were entirely contained within factories and facilities, protected by physical security measures such as fences, security cameras, security gates, guards, etc., without any external network connections; and (2) Security by Obscurity, in which OT/ICS systems used technologies, equipment, connections, and protocols distinct from IT systems, making them inaccessible to IT hackers.
However, the trend towards IT/OT convergence has led to the integration of IT technologies, products, protocols, and connections into OT/ICS systems, causing the systems to lose their previous physical isolation. This integration has exposed several vulnerabilities and security weaknesses, including an OT/ICS architecture focusing on operations rather than security, unencrypted network communication, hidden or forgotten assets during upgrades and tests, lack of clear visibility of the OT network, limited awareness of cybersecurity threats, outdated operating systems, firmware, and software due to long life cycles (15-20 years), existence of numerous vulnerabilities, the use of some non-standard and undocumented protocols, difficulty in deploying patches, and a shortage of personnel with adequate security skills and understanding of OT/ICS systems.
These issues have placed critical systems at high risk of attack, with the potential for severe damage.
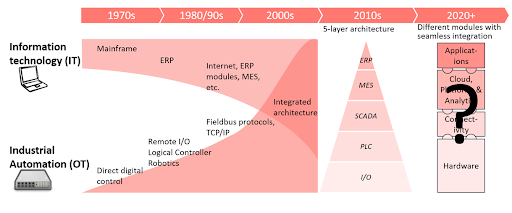
IT/OT convergence trend. (Source: IoT Analytics)
1.2. Increased cybersecurity threats
Cybersecurity threats can be categorized into three types: mainstream hackers, organized cybercriminals, and terrorism/state-sponsored groups. Some notable OT/ICS incidents worldwide include: the hacking of the smart meter system in Puerto Rico, which led to the tampering of the billing system and a loss of $400 million in 2012. In 2015, researchers demonstrated how to spoof a BMW server to unlock the car remotely. Industroyer malware attacked power companies in Kyiv, Ukraine, causing widespread power outages in 2015 and 2016. In 2021, ransomware attacked the IT system of Colonial Pipeline in the USA, forcing the company to shut down its OT system and causing an energy crisis in 16 states. In 2022, a variant of the BlackEnergy malware targeted Ukraine’s electricity system amid the war with Russia.
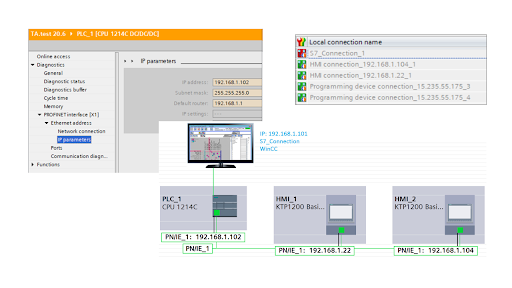
In Vietnam, a security team discovered a way to access a programmable logic controller (PLC) that had not been fully hardened. They were able to collect the control source code, analyze it to uncover internal connection data, read the list and value of control variables, detect PLC configuration errors that allowed modifications of these control values, and change the source code. Further analysis revealed that the PLC was part of the control system of a water plant, responsible for managing the water pumping schedule and monitoring water quality parameters such as pH and chlorine content. Although the team did not alter any parameters or control programs, this incident highlighted the real cybersecurity risks for OT/ICS systems in Vietnam.
The PLC at a water plant in Vietnam was not fully hardened
2. Cybersecurity trends for OT/ICS
2.1. Strategic approach adjustment
With the irreversible reality of the Industry 4.0 revolution and the national digital transformation trend, OT/ICS systems are increasingly connected and integrated into various aspects of life and production. Consequently, agencies and organizations are shifting from traditional boundary defense and attack prevention strategies to deploying security solutions and services that help detect and respond early to cyber threats.
Prioritized measures being proposed include: enhancing network segmentation/network zones and conduits, improving system visibility, monitoring and early detecting vulnerabilities and security incidents, and prioritizing patch management and virtual patching.
2.2. Continued expansion and specialization
The trend of expanding and standardizing OT/ICS system security is evident in the series of documents from the US National Institute of Standards and Technology (NIST):
- In 2002, NIST issued an internal report on IT Security for Industrial Control Systems (NIST IR 6859).
- In 2011, after 9 years, NIST replaced IR 6859 with the Special Edition of Guide to Industrial Control Systems (ICS) Security (NIST SP 800-82), focusing on industrial environments and recognizing that cybersecurity solutions for IT environments are not suitable for ICS systems.
- In 2013 and 2015, NIST announced upgraded versions R1 and R2 for NIST 800-82, with expanded and more detailed content.
- In September 2023, NIST released version R3, renaming the publication to Guide to Operational Technology (OT) Security to cover a broader range of content compared to industrial control systems (ICS). With OT, NIST provides guidance not only industrial systems but also non-industrial systems with similar operating models and technical characteristics, such as building management systems (BMS), heating, ventilation, and air conditioning (HVAC), and smart cameras.
In addition to NIST, several agencies and organizations worldwide provide standards, reference frameworks, and practice guides to help OT/ICS owners and operators to better understand and protect them. Examples include the Critical Infrastructure Protection (CIP) standard of NERC (USA) and the ISA/IEC 62443 series of standards from the International Society of Automation (ISA) and the International Electrotechnical Commission (IEC).
3. Recommendations for government agencies and OT/ICS operators
The above analysis shows that integrating Information & Technology solutions into OT/ICS systems can enhance automation in operations, enable near-real-time collection and analysis of operational and production data, optimize production activities, reduce costs, and improve business efficiency. However, this integration also introduces new security risks that, if exploited, can result in significant harm to people, the environment, and society.
Therefore, leveraging his knowledge and practical experience in researching and implementing security solutions, Dr. Nguyen Thanh Binh, Global Cybersecurity Consultant at FPT IS, proposes the following recommendations to ensure cybersecurity for OT/ICS:
For OT/ICS Owners and Operators:
- Organize training and enhance awareness for leaders, industrial system operations engineers, and office users about real cybersecurity risks for control systems in their infrastructure and factories, and common methods used by attackers for initial intrusion, such as email phishing.
- Develop specialized cybersecurity teams in OT/ICS, including managers, security personnel, and system engineers.
- Periodically review and enhance hardening for OT/ICS systems and devices, particularly those connected to networks (WAN and Internet).
- Research and conduct testing activities, gradually implement technical solutions to protect the OT/ICS environment, prioritizing network segmentation and connection control (zone and conduit), network visibility, incident detection systems (IDS), data transfer control (one-way and two-way, USB kiosk ports), and virtual patching.
- Perform comprehensive security assessments at least once a year against standards/frameworks that support OT/ICS environments, such as CIS Control, NIST CSF, C2M2, or IEC 62443. Note that Vietnam lacks specific standards/guidelines for OT environments, while Circular 12 along with Decree 85 issued by Ministry of Information & Communications relating to level-based information system target IT environments only.
For government agencies:
- Identify the role of OT/ICS cybersecurity for systems critical to national security (under the Cybersecurity Law) and those assessed at levels 4 and 5 (under the Cyberinformation Security Law). Conduct reviews to fully understand and update the security status of these systems.
- Research, test, and implement basic solutions to quickly provide protection layers and minimize risks, such as network segmentation, incident monitoring and detection, virtual patching, and system hardening.
- Create, deploy, and amend strategies, policies, regulations, guidelines, and practical measures for OT/ICS cybersecurity, tailored to specific sectors such as electricity, oil and gas, transportation, and healthcare.
- Establish an OT Cybersecurity Information Sharing and Analysis Center (OT-ISAC) to centralize, coordinate and support OT cybersecurity on a national scale, facilitating active communication with relevant parties within the appropriate scope.
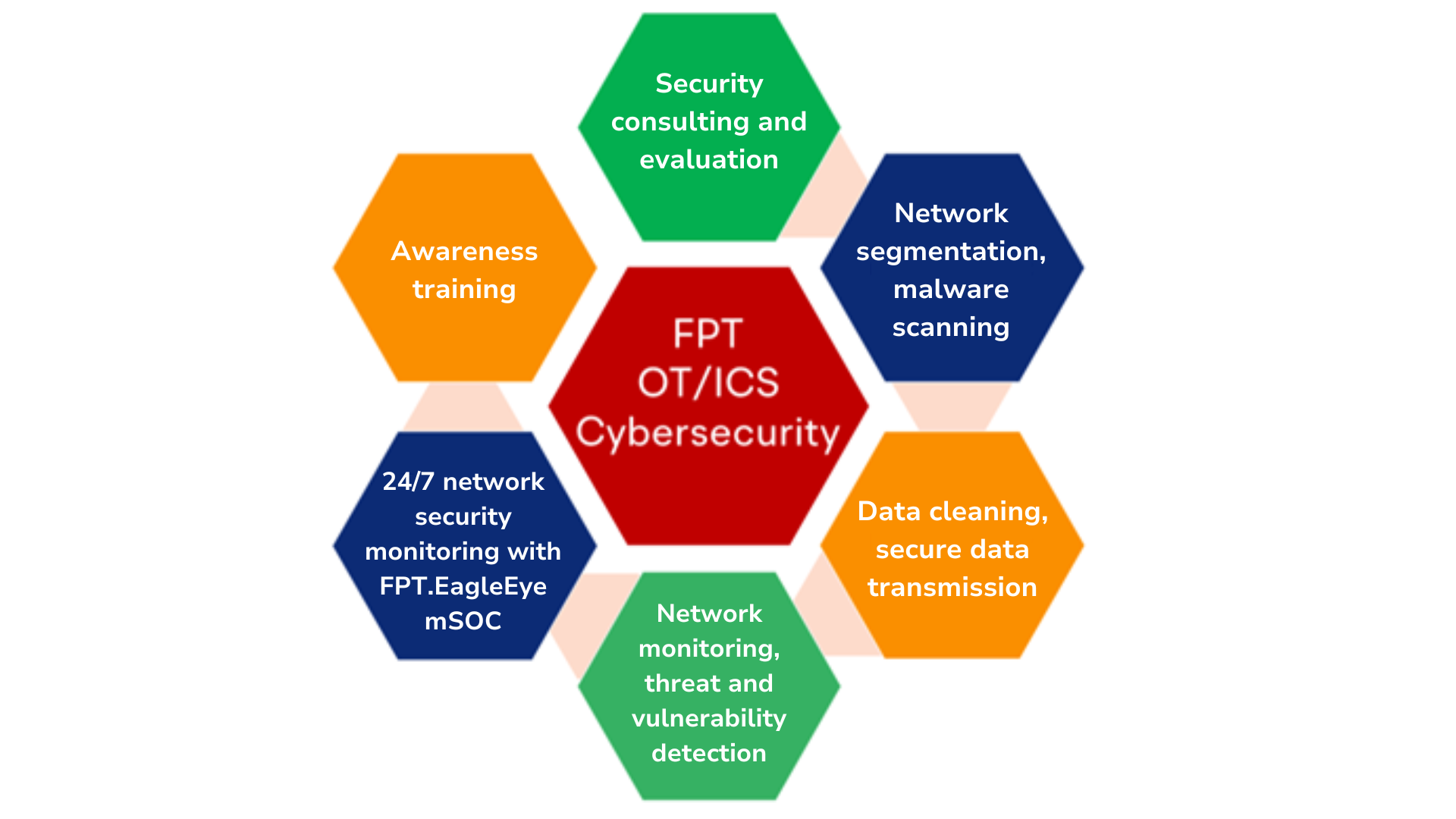
Suite of OT/ICS cybersecurity solutions and services from FPT IS.
With over 25 years of experience in Information Security, FPT IS stands ready to collaborate with government agencies, organizations, and businesses in enhancing OT/ICS security. Our services include IT and OT/ICS security consulting and evaluation, network segmentation, secure data transmission, malware scanning, data cleaning, data control, integrating network monitoring solutions, threat and vulnerability detection, 24/7 network security monitoring with FPT.EagleEye mSOC, and cybersecurity awareness training for OT/ICS systems. Together, we contribute to the comprehensive protection of the country’s critical infrastructure.
| Exclusive article by FPT IS Expert
Author Dr. Nguyen Thanh Binh – Global Cybersecurity Consultant, FPT IS |