Warning: AI-Powered FunkSec Ransomware
A ransomware group named FunkSec has gained notoriety after admitting to attacks targeting over 80 organizations in December 2024.
Information about the FunkSec group
FunkSec is a newly emerging ransomware group in recent times. This group has been operating a data leak site in December 2024 to compile their attack activities. The extortion method used by FunkSec primarily involves double extortion, combining data theft and encryption to pressure victims into paying a ransom. The group’s website displays announcements, a self-developed DDoS tool, and recently a service offering malware as Ransomware-as-a-Service (RaaS).

FunkSec has attracted community attention as up to 85 organizations have been identified as victims of this group in just over a month of operation. Notably, FunkSec demands very low ransoms, sometimes only $10,000, and the price for selling data to third parties is also very favorable. This has led to their activities being actively discussed on cybercrime forums, further enhancing their reputation.
AI Support Capabilities
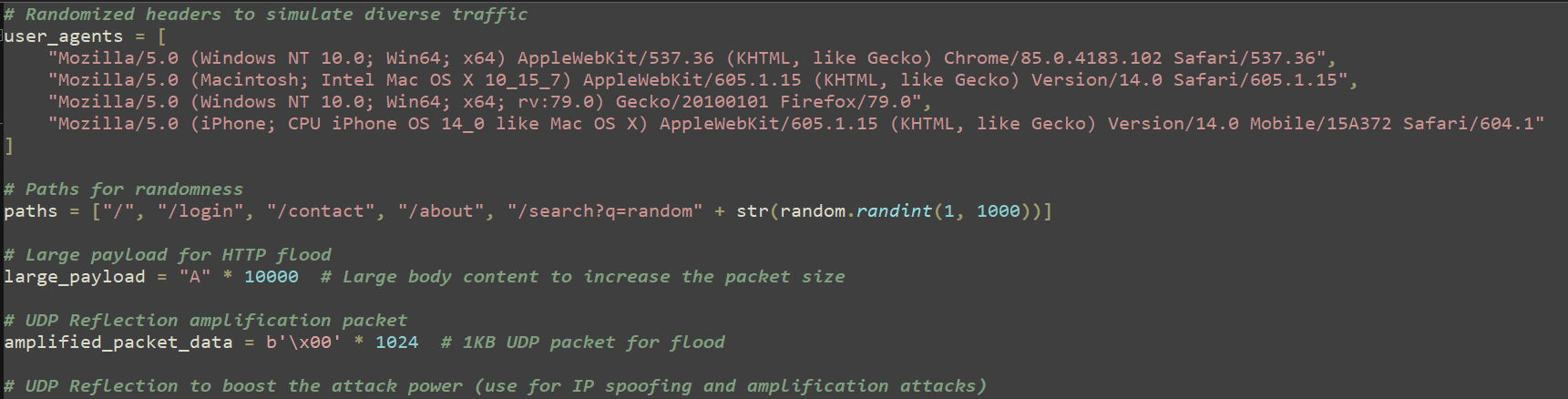
FunkSec has utilized AI in their products to enhance features. The lines of code in the DDoS script and several other products of the group include very detailed comments, seemingly created by a Large Language Model (LLM).
The group has also deployed an AI chatbot based on Miniapps to support their activities. Miniapps is a platform for creating and using AI applications and chatbots, and it is not limited in language. The bot developed by FunkSec is specifically designed to support malicious activities.
Figure 4. Chat interface using Miniapps Scorpion
Features of FunkSec Malware
When executed, the FunkSec ransomware runs a series of commands to disable security features such as turning off Windows Defender’s real-time protection, disabling application and security event log recording, disabling PowerShell execution restrictions, and deleting hidden backups.
| Command | Function |
Set-MpPreference -DisableRealtimeMonitoring $true |
Disable Windows Defender real-time protection |
wevtutil sl Security /e:false |
Disable Security log recording |
wevtutil sl Application /e:false |
Disable Application log recording |
Set-ExecutionPolicy Bypass -Scope Process -Force |
Disable PowerShell execution restrictions |
vssadmin delete shadows /all /quiet |
Delete hidden backups |
The malware also searches for and terminates about 50 processes, mostly task processes, then begins searching for files to encrypt, adding the extension ‘.funksec’ to those files, and then creating a ransom note.
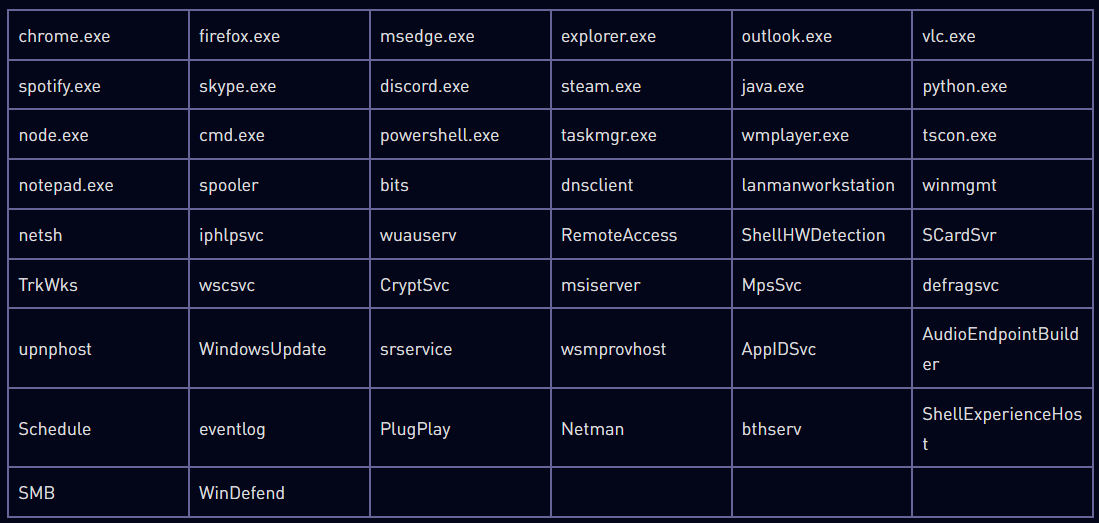
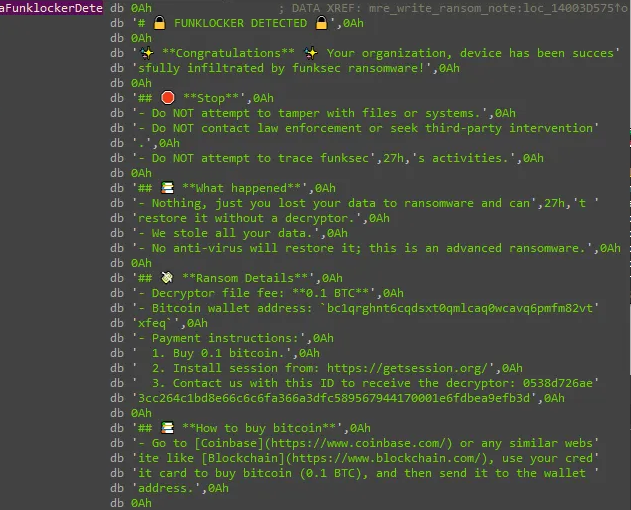
IOCs Related to FunkSec Malware
| Value | IOC Type |
| c233aec7917cf34294c19dd60ff79a6e0fac5ed6f0cb57af98013c08201a7a1c | SHA-256 |
| 66dbf939c00b09d8d22c692864b68c4a602e7a59c4b925b2e2bef57b1ad047bd | SHA-256 |
| dcf536edd67a98868759f4e72bcbd1f4404c70048a2a3257e77d8af06cb036ac | SHA-256 |
| b1ef7b267d887e34bf0242a94b38e7dc9fd5e6f8b2c5c440ce4ec98cc74642fb | SHA-256 |
| 5226ea8e0f516565ba825a1bbed10020982c16414750237068b602c5b4ac6abd | SHA-256 |
| e622f3b743c7fc0a011b07a2e656aa2b5e50a4876721bcf1f405d582ca4cda22 | SHA-256 |
| 20ed21bfdb7aa970b12e7368eba8e26a711752f1cc5416b6fd6629d0e2a44e5d | SHA-256 |
| dd15ce869aa79884753e3baad19b0437075202be86268b84f3ec2303e1ecd966 | SHA-256 |
| 7e223a685d5324491bcacf3127869f9f3ec5d5100c5e7cb5af45a227e6ab4603 | SHA-256 |
Recommendations
FPT Threat Intelligence recommends organizations and individuals take several measures to prevent this campaign:
- Regularly back up data: Store data offline and periodically test recovery capabilities.
- Update software: Always update operating systems and applications to patch security vulnerabilities.
- Use security software: Install and activate antivirus and anti-malware solutions.
- Carefully check emails: Do not open emails, links, or attachments from untrusted sources.
- Limit access rights: Use accounts with low privileges to reduce risk.
- Enable two-factor authentication (2FA): Enhance security for important accounts.
- Security awareness training: Increase user understanding of ransomware threats.
- Network segmentation: Limit spread within the system by dividing the network.
- Incident response planning: Prepare and periodically test response plans for incidents.
References
| Exclusive article by FPT IS Technology Experts
Tran Hoang Phong – FPT IS Cyber Security Center |