When Job Opportunities Become a Trap: The Fake Recruitment Campaign by Vietnamese Hackers
Recently, a cybercriminal group tracked under the name UNC6229 launched a phishing campaign targeting Digital Marketing professionals in Vietnam.
Overview
In October 2025, Google’s Threat Intelligence Group (GTIG) discovered a large-scale phishing campaign by Vietnamese hackers. They exploited fake job postings on legitimate platforms to target individuals in the digital marketing and advertising fields. The attackers used sophisticated methods to distribute malware and phishing toolkits, ultimately aiming to compromise high-value corporate accounts to hijack digital advertising accounts. GTIG has designated this campaign with the tracking code UNC6229.
Google Threat Intelligence Group stated that this campaign primarily targets remote digital advertising employees, those with contract or part-time positions, who may be actively seeking jobs. The attack begins when the victim downloads and executes malware or enters credentials into a phishing website. This inadvertently exposes all of the victim’s information, and the user’s machine becomes a platform for spreading malware or deploying backdoors to take over systems.
Campaign Details
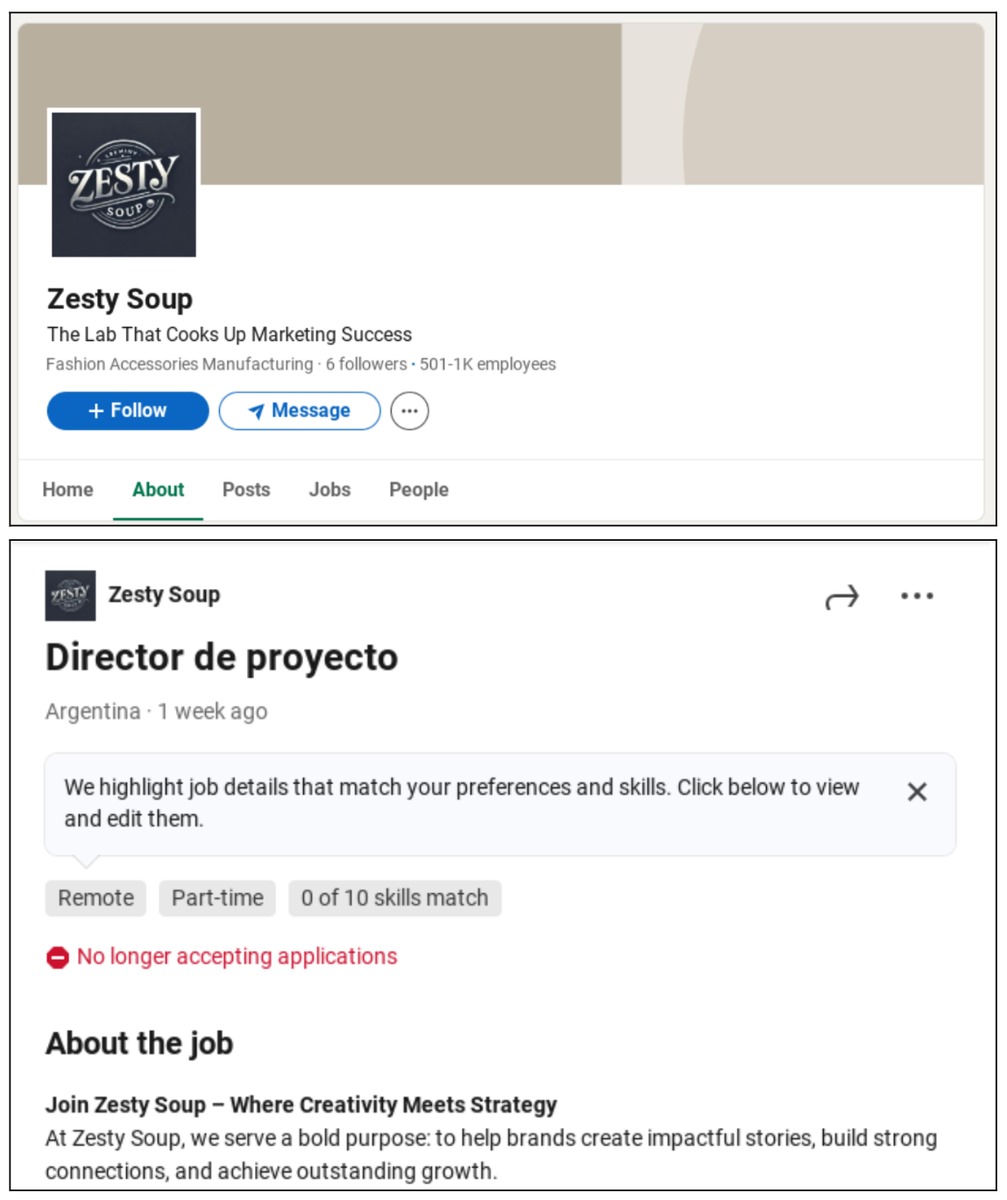
As mentioned, the UNC6229 group will create fake company profiles, often posing as digital media agencies or recruitment companies in the digital advertising industry. They will post attractive positions, remote or flexible work, targeting those seeking part-time or contract jobs in digital advertising.
To build trust with victims, the attackers encourage job seekers to proactively send their information (resume, name, contact). According to one victim, “I applied proactively, so this seemed like a normal recruitment process,” showing how sophisticated and psychologically adept the attackers are.
After posting fake job listings, the hackers will contact the victims and build trust with them. They will reach out via email or direct messaging, sometimes using legitimate CRM tools to send mass emails and manage campaigns. Using legitimate CRM/services helps emails bypass spam filters and makes them harder to control. In this initial step, the emails usually do not contain any malicious attachments to reduce the victim’s suspicion and increase trust.
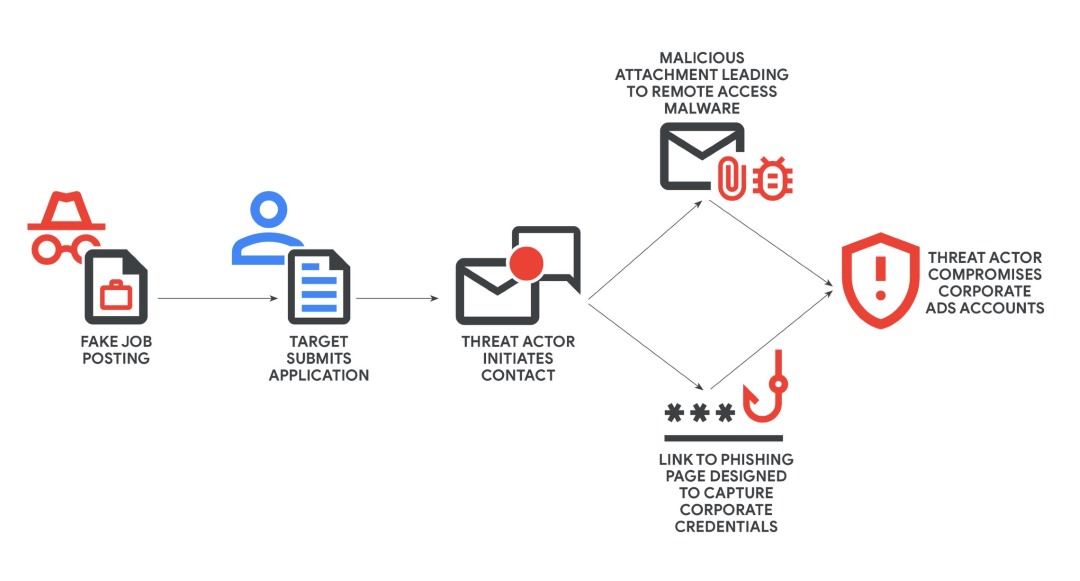
And of course, once they have gained the victim’s trust, the payload will be deployed in two ways.
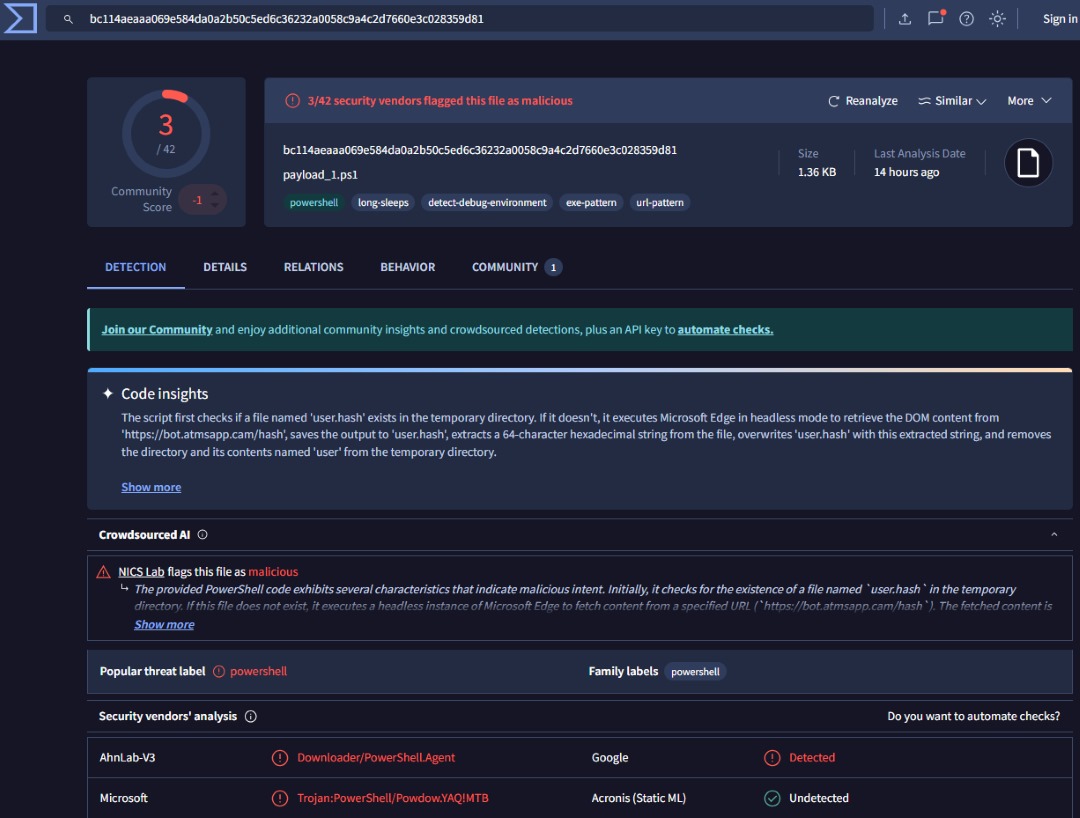
- Malware delivery: UNC6229 will send an attachment (usually a password-protected ZIP file) with an explanation like “skills test” or “mandatory application form.” If the victim extracts and runs it, they may install a remote access trojan (RAT), allowing the attacker to easily control the victim’s machine.
- Phishing link: In this method, the attacker will send links to fake recruitment websites or sites that look like interview scheduling or assessment pages. These pages are cleverly designed and can “capture” multi-factor authentication (MFA) codes from services like Okta, Microsoft, etc.
And of course, if the victim is logged into a company computer or on a personal device with access to the company’s ad accounts, the attacker can exploit this to take control. Once they gain control of the ad or social media account, the attacker can:
- Sell the account to other parties.
- Use it to run scam ads, profiting from advertising or affiliate schemes.
- Increase the risk for the attacked organization, leading to loss of reputation and financial damage.
Conclusion
This campaign has shown that attacks through “fake recruitment” are becoming increasingly sophisticated, as they exploit the real needs of job seekers and rely on the victim’s trust (social engineering) rather than just technical skills.
GTIG predicts that the group UNC6229 and similar actors will “continue to refine their approach, expand their target industries (not just digital advertising), and use multiple platforms like legitimate SaaS or CRM to deceive victims. This means that organizations and individuals need to be constantly vigilant, not only when encountering “strange” job offers but also by strengthening internal controls, delegating authority, and raising awareness.
Recommendations
-
Separate work and personal accounts
- Do not allow employees to use company accounts to log in on personal browsers or uncontrolled devices.
- Require the use of company accounts through SSO (Single Sign-On) or IAM with MFA.
-
Limit access (Principle of Least Privilege)
- Only those who truly need to manage ads should have access to Ads and Meta accounts.
- Implement role-based access control (RBAC) to separate roles like “viewer,” “editor,” “admin.”
-
Employee awareness and training
- Organize quarterly “Security Awareness” sessions, emphasizing the topic of fake recruitment phishing.
- Provide real examples from the UNC6229 campaign to help employees recognize threats.
- Require employees to report any suspicious recruitment emails to IT Security before opening files/links.
-
Be cautious with attachments and links
- Do not download ZIP/RAR/PDF files from unknown sources.
- Do not enter login information or MFA codes outside of official sites.
- Use a secure browser (Chrome/Edge sandbox) and online virus scanning tools before opening files.
-
If you suspect a scam
- Immediately change passwords for all related accounts.
- Check login history (security activity).
- Update antivirus software and scan the entire system.
IOC
-
Domain
- staffvirtual[.]website
- paxcorporation[.]com
- jobs-career[.]site
- careers-promo[.]xyz
-
File Hash
- 137a6e6f09cb38905ff5c4ffe4b8967a45313d93bf19e03f8abe8238d589fb42
- 33fc67b0daaffd81493818df4d58112def65138143cec9bd385ef164bb4ac8ab
- 35721350cf3810dd25e12b7ae2be3b11a4e079380bbbb8ca24689fb609929255
- bc114aeaaa069e584da0a2b50c5ed6c36232a0058c9a4c2d7660e3c028359d81
- e1ea0b557c3bda5c1332009628f37299766ac5886dda9aaf6bc902145c41fd10
Reference
- Help Wanted: Vietnamese Actors Using Fake Job Posting Campaigns to Deliver Malware and Steal Credentials | Google Cloud Blog
- Google Warns of Cybercriminals Using Fake Job Postings to Spread Malware and Steal Credentials
Exclusive article by FPT IS Technology Experts Luu Tuan Anh – FPT IS Cyber Security Center