PassiveNeuron – a mysterious APT campaign targeting global industrial infrastructure
Overview
A recent campaign has been discovered targeting Windows Servers in government, financial, and industrial organizations in Asia, Africa, and Latin America. This campaign was detected by Kaspersky and named PassiveNeuron. The campaign was first discovered in 2024, then paused for about 6 months, and resumed from December 2024 to at least August 2025.
The main targets of these attackers are Windows Servers that frequently run services like MS SQL. Here, they insert backdoors and upload payloads, gather information, and lay the groundwork for further attacks. In the campaign, new implants (specialized malware) were discovered, which had not been recorded before.
Main Impact
System Intrusion and Control
- Gain control of servers
- Establish C2 (Command & Control) channels
Information Leakage, Theft, and Manipulation
- Steal sensitive data
- Manipulate and destroy data
- Move laterally within the internal network
Espionage and Long-term Threats
- Gather intelligence
- Build a “foothold” for future attacks
- Affect reputation and legal standing
Campaign Details
First, we need to go over the initial context of this campaign. During the investigation and handling of incidents related to machines infected with PassiveNeuron in both 2024 and 2025, analysts found that most of the target machines were running Windows Server. Specifically, in this campaign, the attackers gained initial remote command execution on compromised servers through Microsoft SQL software. The attackers have three methods to exploit these SQL servers:
- Exploit vulnerabilities in the server software itself.
- Exploit SQL vulnerabilities in applications running on the server.
- Access the database administrator account.
To avoid web shell detection, the attackers installed them using the following methods:
- Drop a file containing a Base64-encoded web shell into the system.
- Remove the PowerShell script responsible for decoding the Base64 web shell file.
- Launch a PowerShell script to attempt to write the decoded web shell payload into the file system.
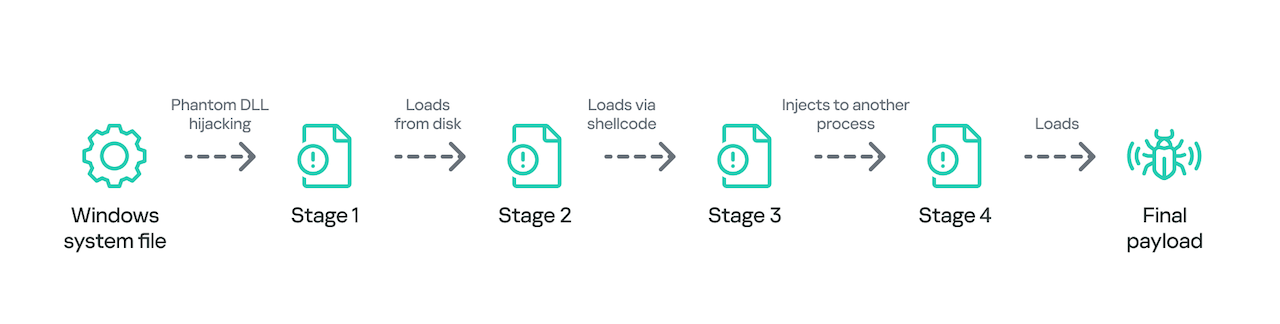
As mentioned, the attackers will carry out the campaign in three stages:
- Initial intrusion stage.
- Deploying implants and malicious payloads.
- Implants and tools used.
In the first stage – initial intrusion, the attackers will target SQL servers, possibly by exploiting SQL server vulnerabilities, SQL injection, or gaining SQL admin credentials to execute arbitrary commands. Once they have execution rights, the attackers will deploy a web shell (such as an ASPX file) for remote access.
After the initial intrusion into the system, the attackers will deploy implants and malicious payloads. You might wonder, what is an implant? In this campaign, the attackers use many of them. An implant is a malicious component (malware) that is “implanted” into the victim’s system to maintain access, gather information, or execute remote commands. Simply put, an “implant” is a special type of backdoor. Experts have noted that three implants were used:
- Neursite: A backdoor written in C++ with modular capabilities, process management, proxy traffic through the infected machine, and plugin loading to support functions like shell commands, file system management, and TCP socket.
- NeuralExecutor: A loader written in .NET, supporting multiple communication protocols and loading and executing .NET assemblies sent from the command-and-control (C&C) server.
- Cobalt Strike: A commercial red-teaming tool, used here by the attackers as part of the payload.
Implants are usually loaded through a DLL loader chain. These DLL files are placed in the C:\Windows\System32 directory with fake names like “wlbsctrl.dll”, “TSMSISrv.dll”, “oci.dll” to exploit DLL hijacking techniques or ensure they load at system startup.
Immediately after, the attackers will extract local credentials from memory, look for misconfigurations, or exploit internal vulnerabilities to escalate privileges to admin or domain admin. Once they have the credentials, they will move to other hosts or abuse remote services (SMB, WMI, RDP) to deploy loaders and implants on other servers to expand their reach.
Of course, in any campaign, the attackers will still make C2 connections to gather important data (DB dumps, config files), package it, and send it out.
Recommendations
- Access Control
- Limit servers accessible from the Internet:
- Only allow access to services that are truly necessary (e.g., ports 443, 1433).
- Use a VPN or Zero Trust Gateway to hide administrative services from the Internet.
- Set ACL (Access Control List) for SQL Server, IIS, or RDP — only accept specific trusted IPs or subnets.
- Disable or remove any unused services (IIS sample pages, SQL Browser, SMBv1, Telnet, old FTP).
- Limit servers accessible from the Internet:
- Updates and Patching
- Maintain a regular patching cycle (at least monthly).
- Automatically check for security patches using WSUS or Ansible/Puppet.
- For SQL Server: always apply the latest Cumulative Updates (CU) to prevent RCE exploits (such as CVE-2023-21529, CVE-2024-30097).
- Privilege Management and Enforcement
- Run SQL/IIS services under a non-Administrator account.
- Enable Windows Defender Exploit Guard (or equivalent) to block DLL injection and memory tampering.
- Apply AppLocker or WDAC (Windows Defender Application Control) to only allow signed or whitelisted files to run.
- Training and Operational Policies
- Train the operations team on:
- Detecting signs of server intrusion.
- How to check for web shells, process chains.
- Procedures for isolating and reporting incidents.
- Establish internal server security policies, including:
- Minimum configuration (security baseline).
- Regular log review procedures (at least once a week).
- Semi-annual security assessment mechanisms..
- Train the operations team on:
Conclusion
The PassiveNeuron campaign is a clear warning that servers—especially Windows servers and SQL Servers—remain the number one target for sophisticated APT campaigns, not just “endpoints.” Targeting servers allows attackers to penetrate deeply, maintain long-term access, and gather large amounts of information.
With signs pointing to a Chinese-speaking group and the use of new techniques (Neursite, NeuralExecutor, dead-drop via GitHub), this campaign should be considered a real threat by government organizations, financial institutions, and industries in all regions, including Vietnam.
IOC
- FIle Hash
- 751f47a688ae075bba11cf0235f4f6ee
- 12ec42446db8039e2a2d8c22d7fd2946
- 406db41215f7d333db2f2c9d60c3958b
- 44a64331ec1c937a8385dfeeee6678fd
- 8dcf258f66fa0cec1e4a800fa1f6c2a2
- d587724ade76218aa58c78523f6fa14e
- f806083c919e49aca3f301d082815b30