Proactive cyber defense: understanding Stealer malware
In the booming age of digital technology, cybersecurity threats are increasing dramatically and becoming more sophisticated. One of the dangerous types of malicious software that needs attention today is stealer malware. So what is stealer malware? What types of stealer malware are there? The first article in the series “Proactively defending against stealer malware” will provide readers with detailed information.
1. An overview of Stealer malware
Stealer is a type of malicious software (malware) designed to collect and steal sensitive information from infected systems. The information that stealers target often includes accounts, passwords, credit card numbers, cryptocurrency wallets, and other personal information. They work by infiltrating the system, collecting data, and sending this information to the attacker through command and control servers (also known as C&C servers).
In today’s world of cybersecurity, Stealer malware is emerging as one of the most worrying threats. Along with the continuous development of prevention measures, stealer malware is also constantly improved and becoming more sophisticated, making its detection and prevention more challenging than ever. Notable stealer malware includes: Redline, Raccoon, Meta, StealC, Mystic, and more. They all have diverse and powerful attack capabilities, targeting both individual users and organizations.
The Stealer problem not only causes serious privacy violations but also leads to huge financial losses and the risk of identity theft. This highlights the importance of raising awareness and strengthening cybersecurity defenses to deal with the growing threat from Stealer malware.
2. Stealer families and variants
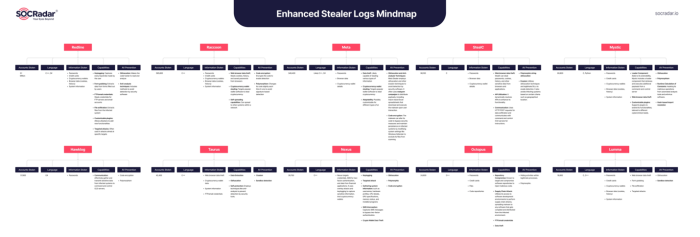
Based on analysis results and reports about Stealer published by reputable security companies, we have researched, synthesized and identified the 10 most popular Stealer malware families. This result is intended to create favorable conditions for individuals and enterprises to carry out threat hunting activities effectively and proactively.
Source: SOCRadar.io
2.1. Redline
– Redline Stealer, written in C++ and C#, is designed to steal a variety of sensitive information such as passwords, credit card details, cryptocurrency wallets, browser data and system information.
– It is capable of keylogging, form grabbing, and login credential stealing from FTP servers and email accounts.
– Redline Stealer uses diverse obfuscation and anti-analysis techniques to evade detection by security software, ensuring covert operations within infected systems.
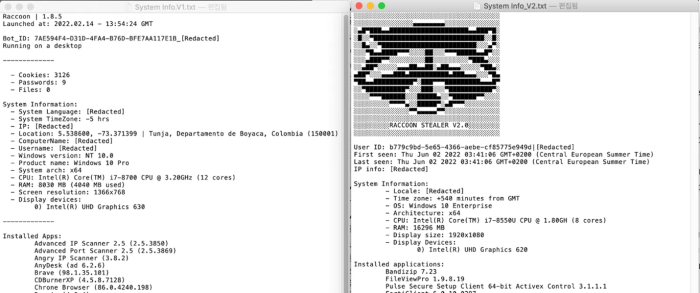
2.2. Raccoon
– Raccoon Stealer, written in C++ and more recently in C, is famous for its ability to steal sensitive information from diverse sources, including passwords, credit card details, cryptocurrency wallets, browser data and system information.
– It is capable of spreading itself, stealing data from popular web browsers and cryptocurrency wallet software, and changing code every time it runs to evade detection.
– Latest version v2.3.0, introduced in August 2023, includes improvements such as quick search for cookies and passwords, automatic bot blocking, detailed log statistics and increased throughput, enhancing user experience and malware effectiveness.
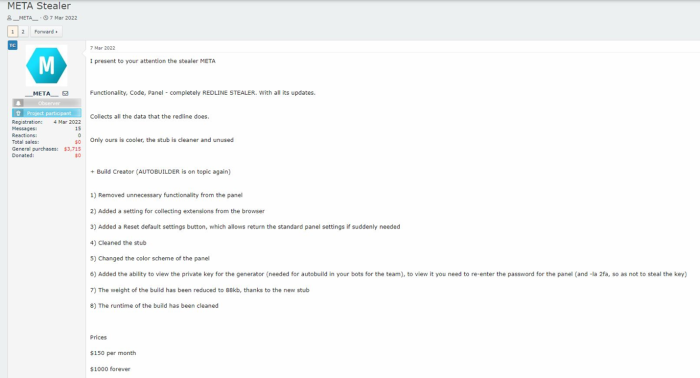
2.3. Meta
– Meta Stealer is designed to target and extract sensitive information such as passwords, browser data, and cryptocurrency wallet details.
– It targets popular cryptocurrency wallet software and is customizable for different types of attacks, using obfuscation and anti-analysis techniques to evade detection.
– Meta Stealer is often distributed through malspam campaigns, which include Excel spreadsheets containing macros that load and execute malicious code upon user interaction.
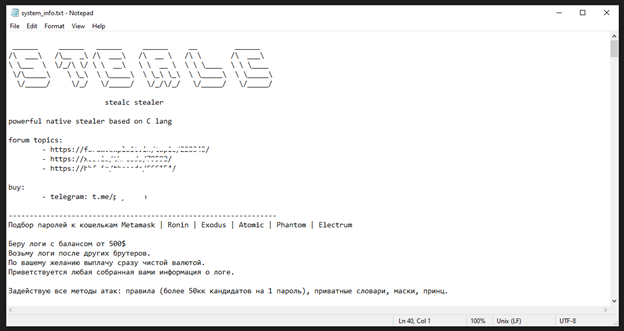
2.4. StealC
– StealC Stealer, developed in C programming language, focuses on stealing sensitive data such as passwords, browser data, and cryptocurrency wallets from popular browsers and computer applications.
– It uses dynamic API resolution to extend functionality and compatibility with different environments, using obfuscation and evasion techniques to defend against security software.
– StealC also avoids infecting systems based on certain criteria, such as geographic location, to enhance evasion and maintain anonymity while performing malicious activities.
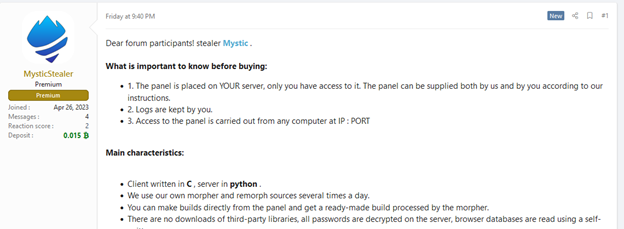
2.5. Mystic
– Mystic Stealer appeared in April 2023, targeting different data sources, including more than 40 web browsers, 70 browser extensions, cryptocurrency wallets, Steam, and Telegram.
– This malware uses obfuscation techniques such as string obfuscation, polymorphism and hash-based import API to evade detection, communicating with command and control servers via a custom encrypted binary protocol.
– Mystic Stealer is developed in C for the client side and Python with Django for the console, using anti-analysis measures such as binary expiration, anti-virtualization techniques, and dynamic constant computation to make analysis difficult.
2.6. Hawklog
– Hawklog is a private cloud service group that specializes in spreading stolen data, sharing exfiltration log data periodically by offering monthly or weekly membership plans.
– In January 2024, Hawklog was attacked by the hacker group Mooncloud, leading to the exposure of a large amount of sensitive data amounting to approximately 1.71GB, mainly consisting of emails, occurring in Telegram channels.
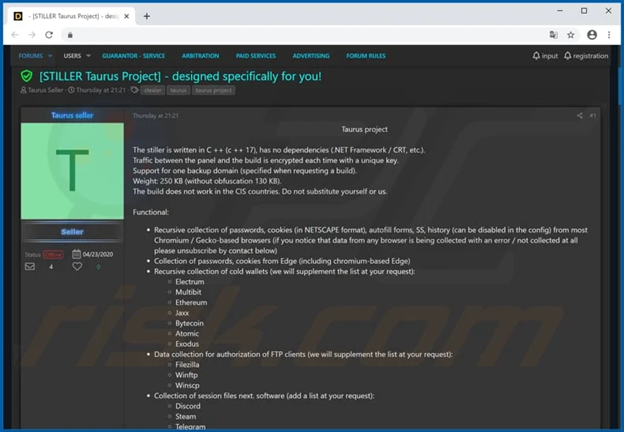
2.7. Taurus
– Taurus is a new malware campaign that appeared in early June 2020, developed by the cybercriminal group “Predator the Thief”, aimed at stealing sensitive information from victims’ systems.
– It is capable of stealing passwords, cookies, and autofill forms along with the history of Chromium- and Gecko-based browsers. Taurus can also steal some popular cryptocurrency wallets, commonly used FTP client credentials, and email client credentials.
– Taurus uses obfuscation code and anti-sandbox techniques to evade detection, applying a fileless method, compressing stolen data into a Zip file directly in memory before sending it to the device command and control (C&C) servers.
2.8. Nexus
– Nexus Stealer appeared in 2020, introduced on the underground forum with a rich feature set, targeting numerous popular applications and platforms.
– Its target list includes web browsers like Chromium and Yandex-Browser, messaging platforms like Authy, Telegram, Discord and Steam, file transfer protocols like FileZilla and WinSCP, as well as other software such as Windows Secure Vault, Internet Explorer, Edge, Pidgin, PSI, PSI+, NordVPN and ProtonVPN.
– Nexus Stealer collects data from the target system, including system information, username, hardware configuration, CPU and GPU details, memory status and installed programs, sends this information back to a centralized web console for threat actors.
2.9. Octopus
– Octopus Scanner appeared around 2018 and targeted repositories on GitHub, infecting repositories that developers accidentally downloaded and integrated into their projects.
– When activated, it scans the system to detect NetBeans IDE and infects build files by installing a dropper that installs a remote access Trojan (RAT), allowing attackers to take control of the infected machine.
– Octopus Scanner uses measures against removal and infection of the source code of affected projects, making cleanup and remediation more difficult.
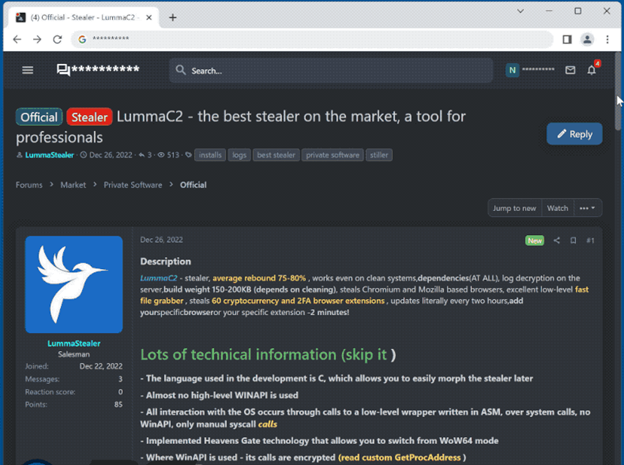
2.10. Lumma
– LummaC2 Stealer is a malicious program designed to steal sensitive data and install applications on infected devices, targeting operating systems from Windows 7 to Windows 11.
– It collects device details such as OS version, CPU, and browsing history from browsers like Chrome, Firefox, and Edge, as well as targeting cryptocurrencies and extracting the information such as usernames, passwords, credit card details and personal identification information.
– LummaC2 uses obfuscation and anti-debugging techniques to evade detection, communicates with remote servers, and sends stolen information as zip files, with recent updates including anti-sandbox techniques, Google cookie recovery capabilities, and integration with Discord CDN and API for distribution.
Stay tuned for how stealer malware works and how to prevent stealer attacks in part 2: “Proactive cyber defense: dealing with Stealer malware for individuals and enterprises”
| Exclusive article by FPT IS technology experts
Author Le Hong Hai – Information Technology Security Engineer at FPT IS |