Ransomware the ghost: When data is used as a blackmail weapon
Growth with the pandemic
The pandemic has accelerated global digitalization, however, this has also made ransomware a significant threat to businesses. Ransomware is a type of malware with the ability to encrypt a victim’s data and demand a ransom in exchange for the decryption. Recent ransomware attacks have caused significant financial and operational losses to many large businesses.
In May 2021, a ransomware attack caused five days’ disruptions to the Colonial Pipeline fuel supply chain in 17 states in the US. The company was forced to pay a ransom of USD 4.4 million. Similarly, JBS – the world’s largest meat processor – also had to pay USD 11 million to deal with a similar attack.
According to a IBM report, the average ransomware attack costs USD 4.54 million, not including the ransom itself. This figure includes many costs such as downtime, reputational damage, and new security measures. Check Point’s research shows that the actual total cost of a ransomware attack is nearly seven times higher than the ransom amount.
A forecast reveals that ransomware will cost its victims around USD 265 billion annually by 2031, with a new attack every two seconds.
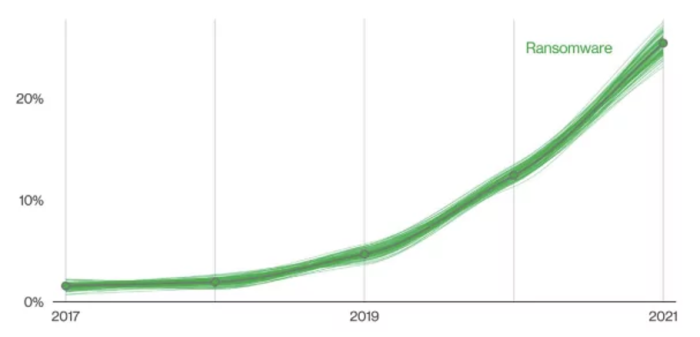
(Figure 1). Ransomware is considered the fastest growing type of cybercrime, according to Cybersecurity Ventures.
According to the 2022 Verizon Data Breach Investigations Report (DBIR), ransomware attacks increased by 13%, which was the biggest increase in the past five years combined (Figure 2). This alarming pattern indicates that ransomware attacks are becoming more dangerous.
Figure 2: Number of ransomware breaches over time (the 2022 Verizon DBIR Report)
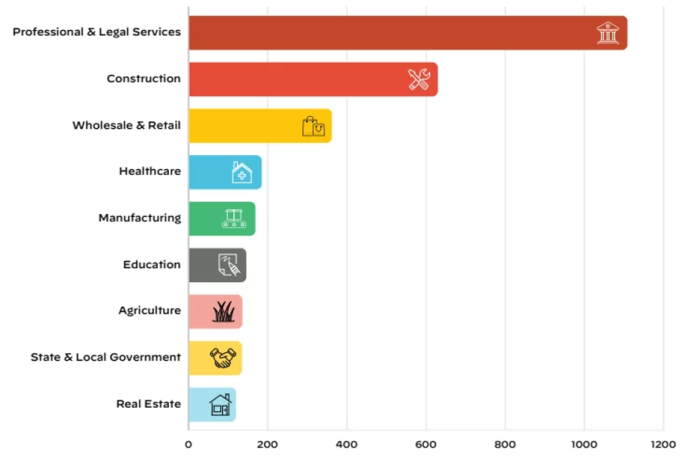
In addition to posing a threat to certain industries, ransomware has spread to an array of sectors, including transportation, telecommunications, finance, healthcare, education, law, manufacturing, food, and also law enforcement (Figure 3). Regardless of company size, both large and small enterprises run the risk of being targets of this kind of cybercrime. Any organization, business, or individual in cyberspace can become a victim of ransomware.
Figure 3: Most ransomware attacked industries sourced from leaked website data (Palo Alto Unit 42, 2022 Ransomware Threat Report)
The ransomware spread “service”
Ransomware has become the most significant cybersecurity threat today and a top priority for Chief Information Security Officers (CISOs) due to its evolution into a well-organized business model for cybercriminals.
Ten years ago, ransomware was the target of only a few digital criminals. However, as more and more attacks occur, it has developed into a professional criminal industry. Ransomware has become the center of an entire ecosystem created by cybercriminal groups. Along with developing malware, they also provide support services so that victims can contact them and pay the ransom.
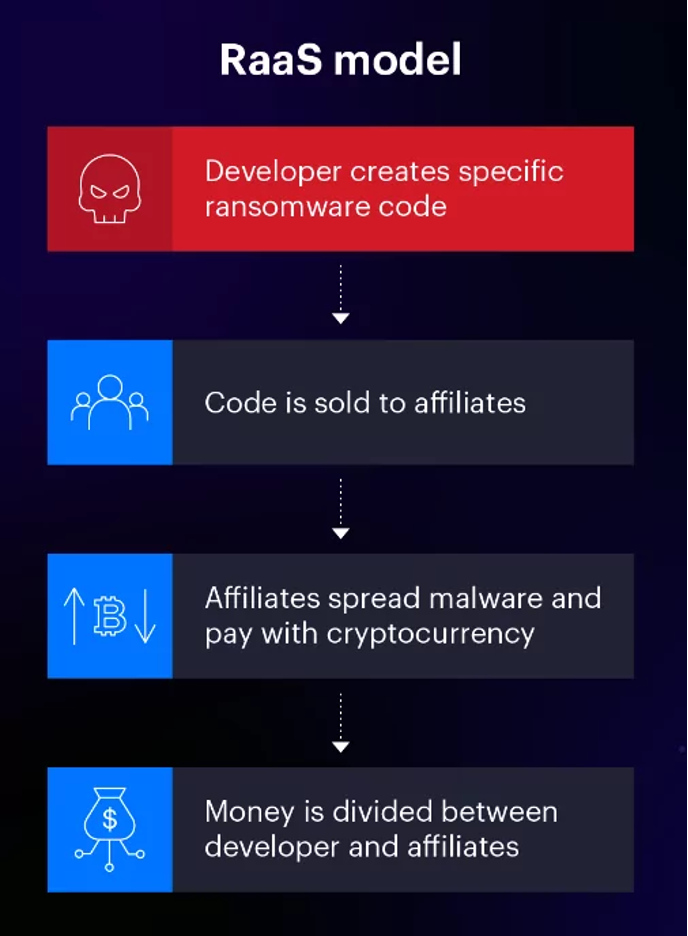
Moreover, the Ransomware-as-a-Service (RaaS) model emerged, in which malware creators offer their tools to clients referred to as “affiliates”. Even without much technical knowledge, affiliates can spread malware. In the end, the ransomware operator and its affiliates share the ransom. This model creates an environment in which ransomware attacks can be executed by non-technical people as well (Figure 4).
Figure 4: Ransomware-as-a-Service (RaaS) model (Varonis, 2021)
Multiple cases of blackmail damage
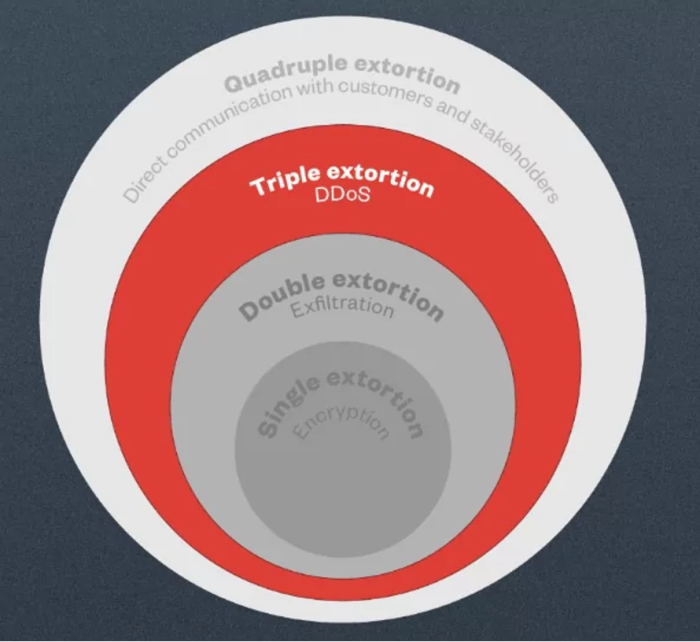
Another significant reason in why ransomware has become a serious threat is that hackers use a variety of extortion tactics after gaining control of an organization’s data and resources (Figure 5).
Today, hacker groups often use up to four extortion techniques, called “quadruple extortion”, to put more pressure on victims to pay ransom:
- First, they encrypt all data, asking victims for payment to give them back access.
- Next, hackers either steal all the data or a part of it and threaten to make it public or resell it if the ransom is not paid.
- If the above two techniques are not effective, they threaten to conduct a Denial of Service (DoS) attack to block the victim’s public services.
- Finally, hackers contact customers, partners, employees and the media to harass and report the security breach.
The variety of techniques used in ransomware extortion shows how dangerous this type of cybercrime is and the importance of implementing effective prevention and response measures. When attacked, the organization will be incapacitated because it cannot access its data. Systems can be down for days or weeks, causing a severe impact on business operations.
Figure 5: Four phases of ransomware extortion (Trend Micro Research, 2021)
Given its sophisticated extortion techniques and unpredictable consequences, ransomware might easily cause significant financial losses and serious reputational damage to organizations. Therefore, organizations frequently agree to pay large ransoms to resolve the problem quickly.
However, satisfying the demands of hackers would only lead to an increase in criminal activities and an uncontrollable downward spiral. Therefore, effective prevention and response is critical to protecting data and business operations from ransomware risks.
How does ransomware spread?
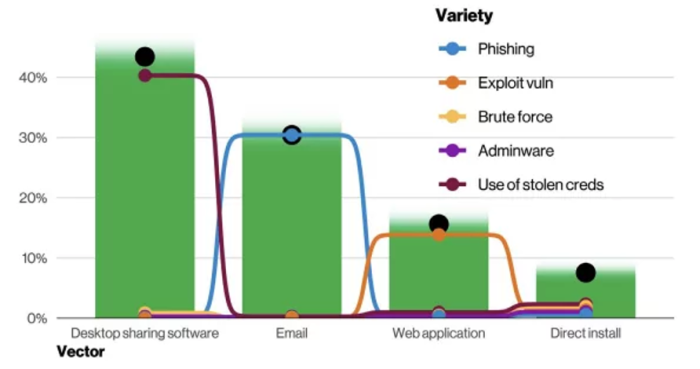
Ransomware infects systems through the three most common attack vectors; remote desktop protocol (RDP, SSH), phishing and security vulnerabilities in web applications. Attackers use different tools for each infection vector, as in Figure 6.
Figure 6: Types of action vectors in ransomware incidents (Verizon DBIR Report 2022)
How to detect and prevent ransomware?
How to stop this threat or how to detect when we are under attack is the question we need to answer.
To effectively defend against ransomware, organizations must deploy a comprehensive strategy that includes the following measures:
- First, take inventory of all IT assets to get an overview of all the critical systems, applications, and data that need to be protected. Next, do routine security vulnerability assessments and identification, and promptly initiate a vulnerability management and remediation process. In addition, strictly monitor services published on the Internet to minimize the risk of attacks.
- Organizations should perform regular security assessments to detect vulnerabilities and remediate them before bad actors take advantage of them. Additionally, deploying 24/7 security monitoring and proactive threat hunting will help detect suspicious activities early and promptly prevent attacks.
- Building an information security process that standardizes security policies, procedures and measures across the organization is crucial. Finally, effectively leveraging threat intelligence sources to stay informed of new threats and the latest attack techniques can enhance organizations’ readiness.
By concurrently putting the above measures in place to safeguard data and business operations, organizations will greatly increase their ability to combat ransomware and several other cyberthreats.
| Exclusively written by the FPT IS experts
Information Security Incident Response Team Cyber Security Center – FPT IS. |