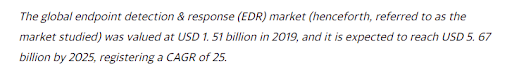Trending technology solutions in cybersecurity
Cutting-edge technologies in cybersecurity, including systems that detect and respond to threats at endpoints, rapid passwordless online authentication protocols, and the application of artificial intelligence (AI), are leading the way in preventing and detecting attacks, aiming to provide comprehensive protection against cyber threats.
Current status of cybersecurity
As the world progresses, the role of technology has become crucial in enhancing societal and individual well-being. Technological breakthroughs are continually introduced by researchers and developers, particularly in computer technology. Over the past 20 years, this field has made incredible strides, with notable advancements in Artificial Intelligence (AI), 5G Networks, Cloud Computing, and Blockchain. These innovations have significantly contributed to our global development. However, they also bring concerns about privacy and cybersecurity. A new war has emerged, not on traditional battlefields, but within servers, computers, screens, and mobile phones. In fact, cybersecurity is becoming increasingly important as user and business information consistently becomes the target of organizations and individuals seeking to exploit Internet vulnerabilities through cyberattacks.
To prevent and combat cybersecurity attacks, user education remains the most effective solution. Educating Internet users about potential risks on the platforms they use has proven to be the best way to minimize both the number and impact of cybersecurity attacks. However, this approach is ideal only in a hypothetical perfect world. Relying entirely on users to know what they are doing is a flawed strategy in any industry, including cybersecurity. Therefore, the current approach is to continuously improve and develop technologies that support cybersecurity, while consistently updating knowledge and reporting on past attacks to find the most advanced prevention solutions.
1. Cybersecurity and trending solutions
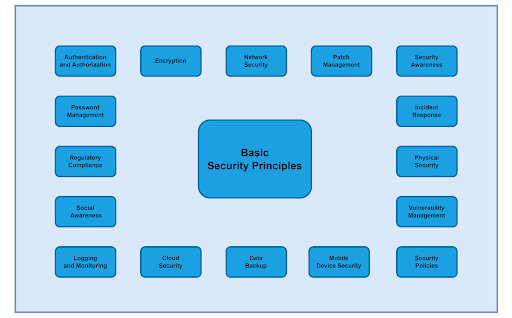
Cybersecurity can be clearly explained and visualized through a “Blueprint” of its activities.
Figure 1 – “Blueprint” for Cybersecurity
This “blueprint” is a synthesis and simplification of 16 key aspects of cybersecurity, including “Authentication and Authorization,” “Access and Monitoring,” “Encryption,” “Endpoint Security,” “Password Management,” “Network Security,” “Cloud Security,” “Hardware Protection,” “Mobile Device Security,” “Patch Management,” “Incident Response,” “Vulnerability Management,” “Data Backup,” “Security Awareness,” “Security Compliance,” and “Privacy Policy.” These aspects can be utilized by organizations to enhance their information security. They can also be classified into broader groups, as defined by IBM, such as “People,” “Data,” “Applications,” “Infrastructure,” and “Monitoring and Administration.” Due to its comprehensive nature, the “blueprint” serves as an important tool in providing an overall view of cybersecurity and a guideline for organizations to implement plans to prevent and combat vulnerabilities or attacks on their databases.
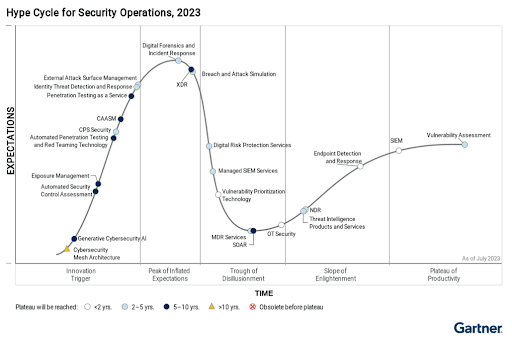
Although the contents of the “Blueprint” cover all important aspects of cybersecurity, each organization has its own characteristics and operational methods. This is reflected in the specific aspects they need to focus on when investing in security systems. For instance, a commercial company doing business online may need to secure its sales website more than a manufacturing company whose website simply displays products. Similarly, a business using cloud computing services will need to focus on protecting information in the cloud, unlike another business that uses products internally. However, there are certain aspects that every organization should consider, which, along with solutions, are seen as new “Trends” in cybersecurity. Gartner’s “Hype Cycle” (2023) provides the clearest illustration of these “Trends” in the current technology era.
Figure 2 – Gartner’s “Hype Cycle”.
This chart provides viewers with an intuitive overview of current factors and solutions in cybersecurity. In addition to listing solutions and their projected time to success, the chart also illustrates the level of adoption and expectations of each solution along a graph axis. Solutions on the left side are those expected to be successful in the future, reaching the highest level of expectation over time. If implemented and put into practice, they gradually move to the right side of the chart. Given the large number of solutions, we will focus on one that is approaching the “Plateau of Productivity” on Gartner’s Hype Cycle, indicating that it is recognized as highly practical and effective when applied.
2. EDR (Endpoint Detection and Response)
On the right side of the Hype Cycle, we see EDR, SIEM, and Vulnerability Assessment.
SIEM (Security Information and Event Management) collects event log data from multiple sources, performs real-time analysis to identify abnormalities, and takes appropriate measures. It can also serve as an effective input for cybersecurity monitoring centers, allowing experts to analyze and promptly detect information security incidents. Currently, SIEM is widely deployed and used in most security systems.
Vulnerability Assessment focuses on reviewing and assessing security vulnerabilities, a solution that must be performed regularly to ensure robust security. As for EDR (Endpoint Detection and Response), it merits a deeper analysis to understand its necessity and practicality.
EDR is designed to protect an organization’s devices from external threats such as viruses, spyware, and ransomware, as well as to prevent malicious actors from exploiting internal data vulnerabilities. The term “Endpoint” refers to devices that serve as network connection points, such as desktop computers, laptops, servers, and mobile devices. According to Gartner, “EDR is defined as solutions that record and store endpoint-system-level behaviors, use various data analytics techniques to detect suspicious system behavior, provide contextual information, block malicious activity, and provide remediation suggestions to restore affected systems.” Essentially, EDR solutions enhance the ability to monitor system activities, synthesize information, and help security teams quickly identify and mitigate risks. When suspicious activity is detected, an EDR system generates alerts, quarantines threats, and provides users with relevant information.
The proliferation of endpoint devices, ranging from computers and phones to IoT devices, has made exploiting vulnerabilities easier than ever before. Due to their interconnected nature, these devices are inherently vulnerable to cyber-attacks and often lack robust self-defense mechanisms. Consequently, a specifically designed system is essential to safeguard the critical information stored on endpoint devices from malicious individuals and organizations. A report published by Mordor Intelligence LLP in 2020 forecasts a steady increase in the market for EDR solutions, surpassing the $5 billion mark in the near future.
Figure 3 – Excerpt from Mordor Intelligence LLP’s report
The strength of EDR solutions lies in their ability to prevent internal threats by detecting unusual activity from devices or applications. In a study conducted by a group of authors from Korea and posted to IEEE (Institute of Electrical and Electronics Engineers), the EDR system was utilized to defend against targeted attacks based on the well-known MITRE ATT&CK framework. The conclusion drawn from the study was that “detection and comprehensive analysis of targeted attacks through the EDR system is feasible,” and that “EDR solutions offer high performance and are capable of delivering favorable results.” This study further solidifies the position of EDR solutions as a key component in the future of cybersecurity.
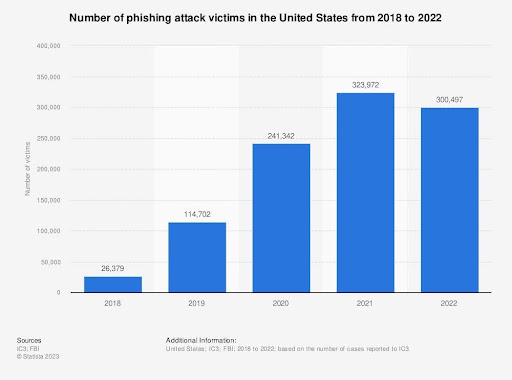
Indeed, while an EDR system can offer comprehensive and reliable security for endpoint devices, there remains a significant need to prevent malicious organizations and individuals from gaining unauthorized access to areas where important data is stored. A report by the FBI (US Federal Bureau of Investigation) in 2022 reveals a stark reality: in the United States alone, nearly 1 million individuals fell victim to phishing attacks over the span of five years, from 2018 up to the time of reporting.
Figure 4 – Total number of victims of phishing attacks in the US (2018-2022)
The prevalence of phishing attacks raises a pressing question for cybersecurity teams worldwide: how can they prevent and counter this increasingly popular form of attack, and more importantly, address user behavior on networks? Doubts about the safety of personal passwords emerged as early as 2004 when Bill Gates, then president of Microsoft, speculated about their disappearance from the future landscape of the IT industry. Before the advent of passwordless authentication, users relied on fixed passwords registered with service providers to access the service. However, this reliance on passwords poses significant security risks. Communications between servers of service providers and login devices are vulnerable to exploitation by malicious actors. Furthermore, the widespread habit of using the same password across multiple services exacerbates the risk for information security. Attacks such as “Man in the Middle” by utilization of virtual wifi or “Phishing” by malicious emails exploit these vulnerabilities, posing significant threats to network user login information. Traditional authentication methods, unfortunately, offer limited protection against such threats, despite repeated warnings about the inherent problems of personal passwords. Although multi-factor authentication protocols have been introduced, password-based login remains the standard for online security and authentication, failing to keep pace with evolving cybersecurity trends. In response to this urgent issue, pioneers and leading organizations in the cybersecurity field have collaborated to develop a new standard: FIDO (Fast Identity Online), a secure authentication method with high reliability.
3. FIDO (Fast Identity Online)
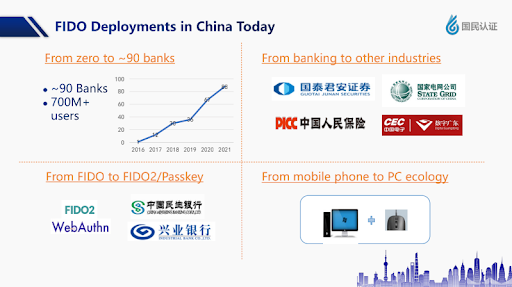
FIDO, or Fast Identity Online, represents a groundbreaking standard for authentication, relying on “Keys Cryptography” – the utilization of security keys. This method enables users to securely sign in to online services without the need for passwords. In practice, login operations now entail the generation of a pair of keys: one stored on the user’s personal device and the other by the service being accessed. These keys are then utilized for user authentication, eliminating the reliance on personal passwords and reducing the risk of phishing attacks. Since its inception in 2013, FIDO has gradually supplanted traditional passwords, gaining traction among organizations and users alike. As more entities prioritize data security, passwordless authentication solutions are becoming increasingly crucial in the evolving landscape of information technology. According to insights from leading industry experts attending the FIDO APAC Summit 2023, the market for passwordless authentication is experiencing continuous expansion. A report by Lenovo in China reveals that since 2016, over 90 local banks (representing 700 million users) in the country have implemented FIDO into their authentication systems, with the trend extending to various other sectors. Another report from Samsung indicates that passwordless authentication is predominantly applied in banking and finance industries, as well as public services.
Figure 5 – Lenovo’s report on FIDO application in the Chinese market
Demonstrating the widespread adoption of FIDO, several typical solutions are widely utilized worldwide, including fingerprint authentication, face authentication, and authentication via physical keys. A prime example of passwordless authentication employing physical keys is the YubiKey product by Yubico. In this authentication method, users no longer enter passwords to log in to services. Instead, they use the YubiKey, a physical key with a USB port, which they connect to their device and lightly touch to authenticate their fingerprint. A secure connection is established between the service provider and the key. The service provider’s server then sends a login challenge to the YubiKey, which signs it with the private key stored on the YubiKey’s hardware. The signed information is returned to the server, which utilizes the public key to verify the login. Although this process may seem lengthy, advancements in integrated technologies have streamlined it significantly. Completing a login with YubiKey now takes mere seconds, much faster than entering passwords traditionally. Moreover, the risk of phishing attacks targeting this process is minimized, enhancing overall security.
Figure 6 – FIDO YubiKey product
4. Artificial Intelligence in Cybersecurity
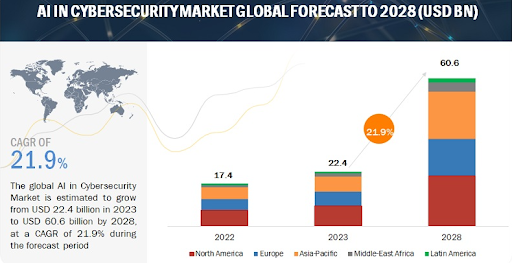
The emergence of artificial intelligence (AI) has significantly impacted the cybersecurity landscape in recent years. AI has introduced a new paradigm for both hackers and information security units. As the scale of the cybersecurity sector expands, the integration of AI methods into information security processes becomes increasingly vital. There is an urgent need for machine learning and continuous information updates to enhance AI systems’ efficacy. According to a study published on the MarketsandMarkets platform, the AI market specific to the cybersecurity industry, encompassing products and solutions, is projected to reach $22.4 billion by 2023. Furthermore, it is anticipated to maintain a cumulative growth rate of 21.9% in the subsequent years, extending until 2028.
Figure 7 – AI development forecast to 2028
The predictive trajectory of AI becoming an indispensable component in cybersecurity stems from its potential to upgrade and optimize security solutions through self-analysis and adaptive solution finding capabilities, rather than rigid rule-based approaches. Achieving this capability entails continuously feeding attack information to the analysis system, essentially enabling the machine to “learn” from these experiences.
Machine learning can be categorized into two types: “shallow” learning and “deep” learning. In the traditional or “shallow” method, industry experts analyze complex connections and synthesize them into rules for the AI system to follow. Conversely, “deep” machine learning involves feeding large volumes of raw data to the machine, allowing it to identify connections or variations within the data and construct a framework containing the rules inferred from the dataset. When applied to cybersecurity, artificial intelligence (including machine learning) plays a crucial role in detecting intrusions, analyzing malicious software, and preventing phishing attacks. Research presented at the 2018 International Conference on Cyber Security by a group of authors from the University of Modena and Reggio Emilia in Italy indicates that machine learning methods, both traditional and modern, are utilized across all three categories of cybersecurity mentioned above.
However, assessments suggest that while the potential of machine learning methods in cybersecurity is significant, they are unlikely to entirely replace the role of humans—at least not at present. Experiments conducted by researchers aimed at detecting network intrusion attacks (Network Intrusion Detection) and virtual domain creation attacks have revealed that adversarial attacks, wherein attackers employ deceptive tactics such as fake data, can cause AI algorithms to become inaccurate. Consequently, continuous training and human refinement are necessary to mitigate these challenges and maintain the efficacy of AI algorithms.
When considering Gartner’s “Hype Cycle”, it is evident that artificial intelligence is still in its early stages of development. It will take some time for this technology to fully mature and gain widespread acceptance. However, improvements in machine learning to enhance information security solutions will persist. Experts anticipate that in the not-too-distant future, we will witness the emergence of artificial intelligence and machine learning which will become indispensable technologies in cybersecurity solutions and products.
5. Conclusion
The cybersecurity industry stands out as a focal point in global development. While advancements enhance daily life, the proliferation of technologies and equipment inadvertently creates vulnerabilities, offering opportunities for malicious entities to exploit and sabotage vital systems. Over time, numerous technologies have been introduced and integrated into cybersecurity solutions and products. Depending on the specific activities and information security concerns of each organization or business, they may invest in cybersecurity systems differently. However, certain trending solutions are garnering widespread interest today. These include endpoint detection and response systems, passwordless authentication protocols, and the application of artificial intelligence in preventing and detecting attacks. While these technologies may be at different stages in their life cycle, they are poised to become pioneering solutions in the field of cybersecurity in the near future, with the collective aim of comprehensively protecting users from cyber attacks.
| Exclusive article by FPT IS Expert
Author Dao Gia Hanh – Head of Technology Partner Development Department, FPT IS |